H CPR (από το Check Point Research) has identified numerous attacks exploiting the Log4j vulnerability and presents a detailed example of how a real attack works.
While most of the hacker discovered exploited this vulnerability to extract Linux-based cryptographic credentials, Check Point researchers have now identified a cyberattack involving, for the first time, an undetected, .NET-based malware.
The attack targeted five victims in the financial, banking and software markets in the following countries: Israel, the United States, South Korea, Switzerland and Cyprus.
The malicious server is located in the United States and hosts multiple malicious files.
Such attacks are the first stages of large-scale attacks (such as ransomware). It is a kind of "living test" of the vulnerability and potential for harm that can be inflicted on victims, only to carry out a larger attack later.
Simply put, once any type of malware is introduced, a bigger attack is only a matter of time. Technically there is not much difference. What is now seen as cryptomining is very often followed by ransomware and other types of dangerous attacks.
Currently, CPR has identified more than 1.272.000 vulnerability attempts, affecting more than 44% of corporate networks worldwide.
How the attack works:
The attack exploits the Log4j vulnerability to download a malware Trojan, which causes the download of a archivey .exe which in turn installs a crypto-miner.
Once the crypto-miner is installed, it starts using the victim's resources to extract cryptocurrency for the perpetrators' profit, and all this without the victim knowing that it has been violated. Σ
the context of malware avoidance techniques, all related functions and names files συσκοτίζονται για να αποφεύγεται η ανίχνευση από μηχανισμούς στατικής ανάλυσης.
The numbers:
- To date, CPR has identified more than 1.272.000 vulnerability sharing efforts. 46% of them from known malicious hacker groups.
- Exploitation attempts have been recorded in over 44% of corporate networks worldwide
Comment: Lotem Finkelstein, Head of Threat Intelligence at Check Point Software:
"We have identified a huge number of exploitation efforts in recent days. Attackers are actively searching for potentially vulnerable targets, and new scan tools for this vulnerability continue to emerge. Smaller-scale attacks are the way in which larger-scale attacks develop. Threat-takers like to test their tools and targets, leading to more dangerous attacks such as ransomware.
It is clearly one of the most serious vulnerabilities on the internet in recent years and is spreading like wildfire. In some places, we have seen over 100 breaches associated with the LogJ4 vulnerability per minute. We are seeing what appears to be an evolutionary repression, with new variants of the original exploit being introduced quickly - more than 60 in less than 24 hours. The number of exploitation combinations gives the attacker many alternatives to bypass the newly introduced protections. This means that one level of protection is not enough, and only a multi-layered safety posture would provide a durable protection.
Unlike other major cyber attacks involving one or a limited number of software, Log4j is essentially integrated into any Java-based web product or service. It is very difficult to restore manually. As soon as a survey was published (on Friday), internet scans followed (to understand the vulnerabilities due to the recent incident). Those who will not implement a protection solution, have probably already been scanned by malicious carriers. Already, we have recorded over 1.272.000 attacks, with over 44% of corporate networks worldwide being targeted.
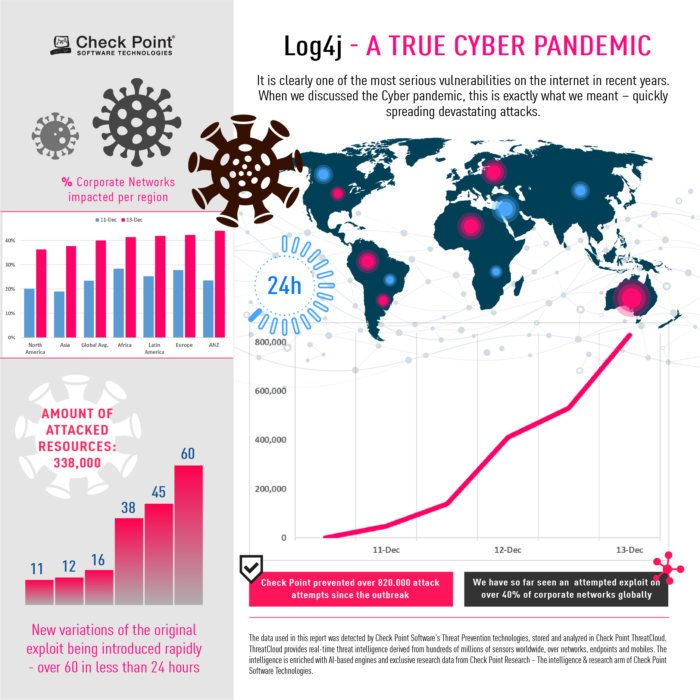
This vulnerability, due to its complexity in repair and ease of use, will concern us for years to come, unless companies and services take immediate steps to prevent attacks on their products by applying protection. Now is the time to act. Given the festive season, when security teams may be slower to implement safeguards, the threat is immediate. "It works like a cyber pandemic - it is highly contagious, it spreads quickly and it has multiple variants, which require more attack methods."
More information about the LogJ4 vulnerability and the finding during Check Point Research's monitoring of several attacks involving mining cryptocurrency from its exploitation, will find here.





