Check Point Research (CPR) presents the 2021 Q4 Brand Phishing report Report, in which he points out the top brands imitated by hackers in their attempts to fraudulently obtain personal data of third parties.
With the rise of COVID cases and the arrival of the holiday season, DHL has put an end to Microsoft's long-standing dominance as the brand most often imitated by cybercriminals. Social media is consolidating its position among the top three areas to emulate in phishing attempts, as WhatsApp and LinkedIn rank higher in the list of the 10 most frequently imitated brands.
- 23% of all phishing attempts in Q2021 9 were related to DHL, up from just XNUMX% in QXNUMX.
- Microsoft, which once again held the top spot in Q29, accounting for 20% of all phishing attempts, dropped to XNUMX% of phishing attacks in QXNUMX.
- FedEx made its appearance on the top ten list in Q2021 XNUMX
The Top 10 of the top brands to imitate in the 4th quarter of 2021
Trademarks are classified based on their overall appearance in phishing attempts:
1. DHL (related to 23% of all phishing attacks worldwide)
2. Microsoft (20%)
3. WhatsApp (11%)
4. Google (10%)
5. LinkedIn (8%)
6. Amazon (4%)
7. Fedex (3%)
8. Roblox (3%)
9. PayPal (2%)
10. Apple Lossless Audio CODEC (ALAC), (2%)
For the first time, DHL ranked first in the fourth quarter, replacing Microsoft as the brand most likely to be targeted by cybercriminals in phishing scams as perpetrators try to take advantage of vulnerable online consumers during of the busiest season of the year.
The fourth quarter report also reinforces a trend emerging from the third quarter involving social media, which appears to be consolidating its position among the top three areas to emulate in phishing attempts. While the Facebook fell out of the top ten, WhatsApp moved from 6th place to 3rd, now accounting for 11% of all phishing attempts. Also, LinkedIn has moved from 8th place to 5th, now accounting for 8% of all phishing-related attacks.
What is an attack? brand phishing?
In an electronic attack "brand phishing” , criminals try to imitate the official website of a well-known brand, using a similar domain name or URL and design by clicking hereς με τον γνήσιο ιστότοπο. Ο σύνδεσμος προς τον ψεύτικο ιστότοπο μπορεί να αποσταλεί σε στοχευμένα άτομα μέσω ηλεκτρονικού ταχυδρομείου ή μηνύματος κειμένου. Ο χρήστης μπορεί να ανακατευθυνθεί κατά τη διάρκεια της περιήγησης στον ιστό ή μπορεί να ενεργοποιηθεί από μια δόλια εφαρμογή για κινητά τηλέφωνα. Ο ψεύτικος ιστότοπος περιέχει συχνά μια φόρμα που αποσκοπεί στην κλοπή των διαπιστευτηρίων των χρηστών, των στοιχείων paymentor other personal information.
Ο Omer Dembinsky, Data Research Group Manager at Check Point Software, said:
"It's important to remember that cybercriminals are primarily opportunists. In their attempt to steal our personal data or develop malware on a user's machine, criminal gangs often exploit consumer trends by imitating popular brands. This quarter, for the first time, we saw the global logistics company DHL at the top of the rankings as the most likely brand to imitate, apparently to take advantage of the surge in the number of new and potentially vulnerable online shoppers during busy retail season of the year. Older users in particular, who are less likely to be technologically familiar with the younger generations if they are shopping online for the first time, may not know what to look for when it comes to issues like delivery confirmation messages or tracking updates. In addition, the increase in COVID cases has resulted in people relying more on the shipping service and cybercriminals are likely to try to take advantage of people who choose not to go to physical stores. ”
The 4th quarter also confirmed what many of us expected. That social media would continue to be largely the target of malicious agents seeking to exploit those who rely more on channels such as WhatsApp, Facebook and LinkedIn as a result of remote work and other effects of the pandemic.
Unfortunately, there is a limit to what brands like DHL, Microsoft and WhatsApp can do - the top three fake brands in the fourth quarter - to combat phishing attempts. It is very easy for the human factor to overlook things like wrong domains, typographical errors, wrong dates or other suspicious details, and this is what opens the door to further damage.
We would urge all users to pay close attention to these details when dealing with companies like DHL in the coming months.
Example A: Paypal
During the November discounts, we noticed a malicious phishing email allegedly sent by PayPal trying to steal users' credit information.
Figure 1. Malicious e-mail sent with the subject "[Alert] Confirm your PayPal account (Case ID #XX XXXXXXXXXXXXX)"
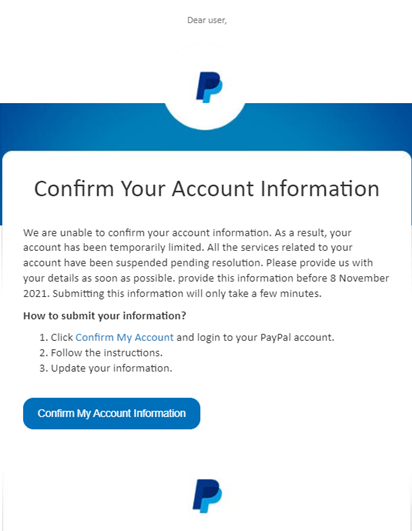
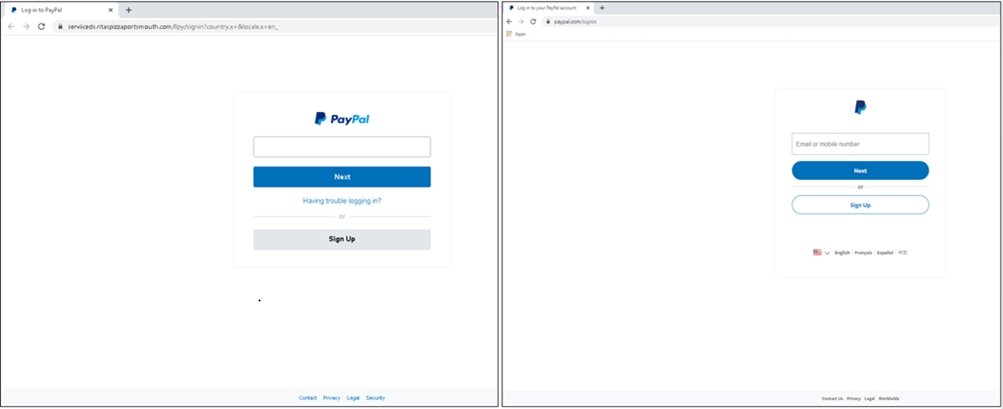
Figure 2. Left side – fake page connections ? Right side – actual login page
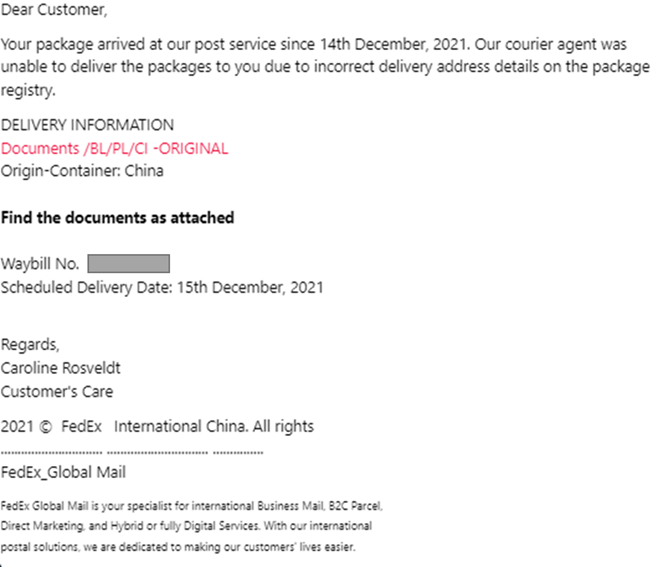
Example B: FedEx
During December, we noticed a malicious email Phishing using its trademark Fedex and was trying to persuade the user to download the malware SnakeKeylogger on his computer. The e-mail (see Figure 1) sent from the fake address support@fedex[.]com, contained the topic “Bill of charging-PL/CI/BL-Documents arrival“. The content asks you to download an archive file RAR "shipment docu..rare", Which contains a malicious executable file that would infect the system with SnakeKeylogger and could intercept user credentials.
Figure 3. Malicious e-mail with the subject “Bill of Lading-PL / CI / BL-Documents arrival”
Example C: DHL
In this below Phishing Email, we see an attempt to steal it Email and the password of the users through an imitation of the brand DHL. Sent from fake DHL Customer email address Support (info @ emmc [.] ir), contained the topic DHL Shipment Notification: xxxxxxxxxxxx “Out for delivery” for 15 Dec 21 ″. The attacker was trying to entice the victim to click on a malicious link (http: //reg[.]chaindaohang[.]com/wp-content/Uploads/ 2021 / 07 /dhl/index[.]php?i=i& 0 =vegenat@vegenat[.]es), which redirects the user to a deceptive homepage DHL, which looks like the actual website (see Figure 2).
In the malicious link, the user was prompted to enter Email and its password.
Figure 4. The malicious e-mail sent with the subject “Sending notification DHL : xxxxxxxxxxxx "Oct for delivered" for 15 Dec 21"
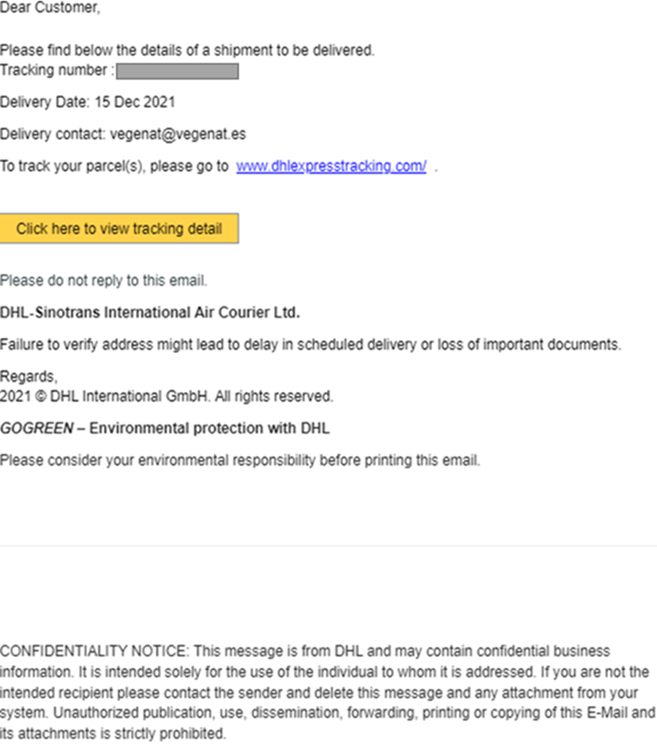
Figure 5. Left side - fraudulent credentials login page? Right side - real login page






