What is Hellsing? Η Kaspersky Lab identified a rare and unusual case of attack from one digital criminal to another. 2014, Hellsing, a small and modest technical espionage team targeting mainly governments and diplomatic organizations in Asia, was attacked by spearphishing by another online threat agent and decided to fight back. Kaspersky Lab believes this could signal the emergence of a new trend in digital crime: "APT wars".
The discovery was made by Kaspersky Lab experts, in context researchs regarding the activity of Naikon, a digital espionage group that also operated in the Asia-Pacific region. The experts noted that one of the targets had detected that the Naikon team had attempted to infect its systems through a spearphishing email that carried a malicious file attachment.
The goal questioned the authenticity of the email by addressing the sender and apparently dissatisfied with the response he received did not open the attached file. Shortly afterwards, the target sent the sender an email containing the malicious object itself. This move sparked Kaspersky Lab's research and led to the discovery of Hellsing's Advanced Persistent Threat.
The counterattack method shows that the Hellsing team wanted to identify the Naikon team and gather information about them.
Moving to a deeper analysis of Hellsing, Kaspersky Lab has discovered a series of spearphishing messages with malicious attachments that were designed to spread malicious spyware to various organizations. If the victim opens the malicious file, his system is infected with a custom backdoor, which can "download" and "upload" files, update and uninstall itself. According to Kaspersky Lab's comments, the number of Hellsing targeting organizations has approached 20.
Its objectives Hellsing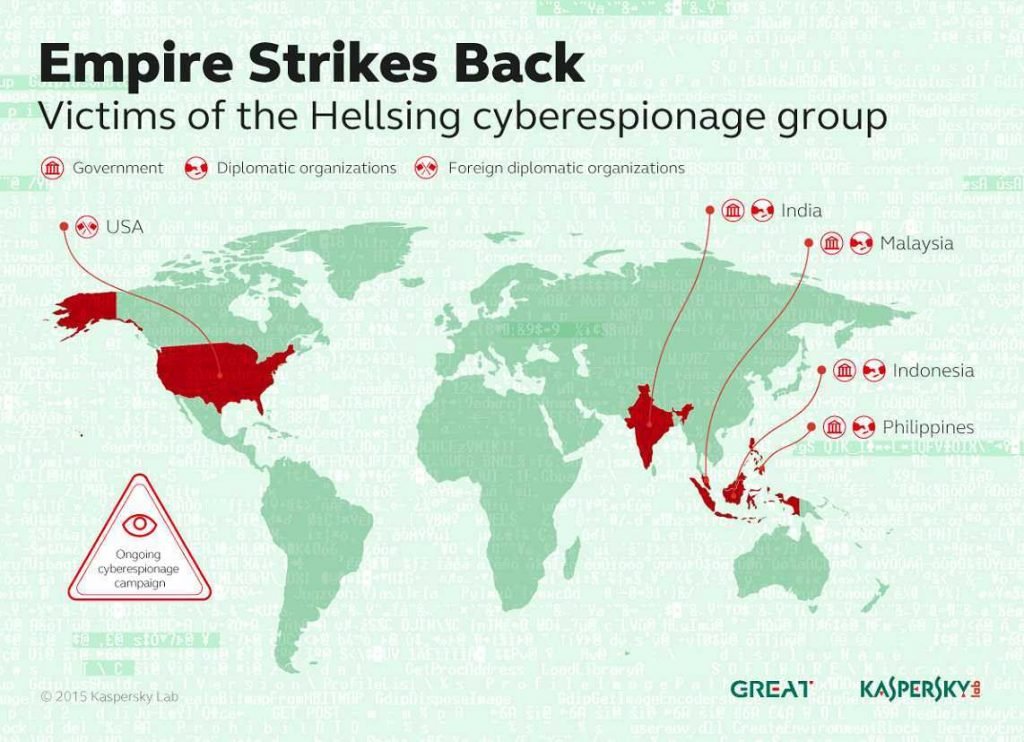
Kaspersky Lab has detected and blocked Hellsing malware in Malaysia, the Philippines, India, Indonesia and the US, with most victims being in Malaysia and the Philippines. Attackers are also very selective in relation to the type of organizations they target, seeking to "pollute" mainly governmental and diplomatic organizations.
"The fact that the team Hellsing has targeted the team Naikon, can be described as a kind of vengeful "stunt hunter". This in itself makes the attack "exciting" for researchers. In the past, we had seen some APT teams accidentally attacking each other, stealing parallel address directories from the victims, and then sending bulk mail to everyone on those lists. However, given the targeting and origin of the attack, it seems more likely that this is an example of a deliberate attack from one APT group to another, said Costin Raiu, Director of Kaspersky Lab's Worldwide Research and Analysis Group.
According to Kaspersky Lab's analysis, the Hellsing threat agent is - and remains - at least active on 2012.
Protection
To protect against group attacks Hellsing, Kaspersky Lab recommends the following key security best practices:
- Do not open suspicious attachments from senders you do not know
- Pay attention to password-protected files that contain SCR files or other executable files
- If you are not sure about the attached file, try opening it in a sandbox environment
- Make sure you have an updated operating system with all the necessary patches installed
- Update all third-party apps such as Microsoft Office, the Java, the Adobe Flash Player and Adobe Reader
Kaspersky Lab products detect and block malware that usesfrom both Hellsing and Naikon.
More information is available on the site Securelist.com.





