The Internet was not designed to be secure on its own. Many protocols (such as HTTP and DNS ) are designed to serve their purpose and to transmit information over the network without security.
However, these days, privacy and security are top priorities. As a result, the Transport Level protocol Security (TLS) (και ο προκάτοχός του SSL) έχουν σχεδιαστεί για να κρυπτογραφούν το traffic μέσω του δικτύου. Αυτό επιτρέπει στους υπολογιστές να χρησιμοποιούν τα ίδια πρωτόκολλα για τη formatting of the data (like HTTP) but add a layer of security (by converting it to HTTPS).
The problem with SSL / TLS security is that it works. While encryption templates were developed for a good purpose, hackers also use them for illegal activity. In this article, we will describe how to perform SSL / TLS decryption in Wireshark.
What you will need
The Wireshark is a commonly known and freely available tool for network analysis.
The other thing you need to do before decrypting the encrypted TLS traffic is to configure your web browser to extract the TLS keys from the client.
Since TLS is designed to protect client and server data during information transmission, it makes sense that it is designed so that anyone can decrypt the traffic.
In Firefox and Chrome, this can be achieved by setting a variable called SSLKEYLOGFILE. If this variable is set both browsers are configured to store one copy of the client in the indicated location of the file. In Linux, this variable can be set using the Export command. In Windows, it can be configured by opening Advanced System Settings, selecting Environment Variables, and then adding a new System Variable. An example of this variable in Windows is shown below.
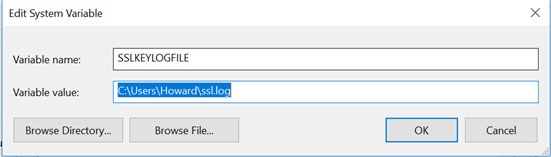
Once the variable is set, it is recommended that the system be restarted to ensure that the new settings are active. Once completed, we have everything we need to decrypt the TLS traffic.
Perform motion decryption
If you want to decrypt TLS traffic, you must first record it. For this reason, it is important to enable and run Wireshark before you start surfing.
Before we start downloading the program, we need to prepare the TLS traffic decryption. To do this, click Edit → Preferences. Select Protocols in the left pane and scroll down to TLS. At this point, you will see something similar to the image below.
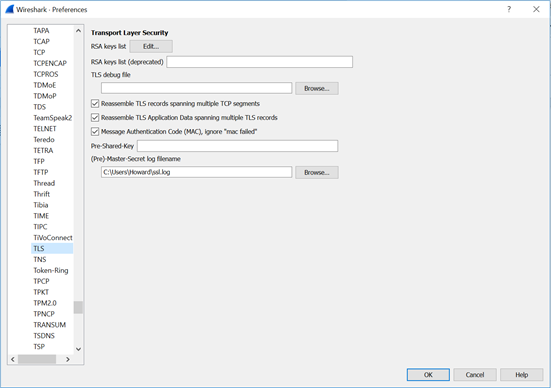
At the bottom of this image, there is a field with the file name (Pre) -Master-Secret log. As shown above, you must set this value in the same location as SSLKEYLOGFILE for your browser. When done, click OK.
Now on the Wireshark main screen, it will display a list of possible adapters to download. In this example, I will use WiFi 2 as there is traffic (shown from the black bar).
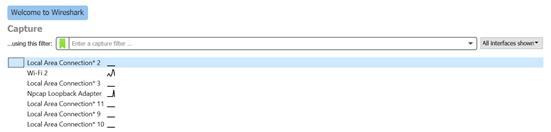
Clicking on an adapter will start recording its traffic on it.
At this point, you are ready to generate some encrypted TLS traffic. Go to Chrome or Firefox and browse to a site that uses HTTPS (we used Facebook for this example). Once the page is loaded, return to Wireshark and stop capturing the packages.
Looking at the shot, you'll probably see a lot of movement. What we are looking for now are the packets related to the TLS encrypted browsing session. One method is to find the DNS lookup and filter with the one provided address IP (shown below). The image below shows a packet from our Facebook browsing session.
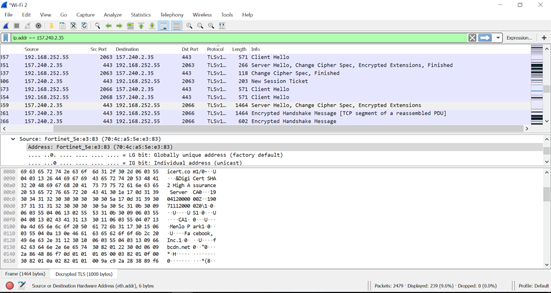
As you can see, Wireshark displays some different tabs at the bottom of the window. In addition to the Frame tab, one is called Decrypted TLS. Looking at the ASCII representation of the package, we see the certificate of the site (including the word Facebook). At this point, we have successfully decrypted the TLS release on Wireshark.
Applications and restrictions
Decryption of TLS traffic is accomplished by many applications. Many hackers have moved to using encrypted transmissions in an attempt to increase their level of anonymity and control communications and credibility to their victims. (People have been trained to trust the green padlock unfortunately…) Using TLS decryption, the businesses they can decrypt and perform packet inspection on the traffic that exists in their business.
The main limitation of TLS decryption in Wireshark is that it requires the monitoring device to have access to the secrets used for the encryption. While we have achieved this by exporting keys from Chrome and Firefox, many companies choose to implement a proxy that splits the TLS connection in two. While this is effective for monitoring, it has important implications for privacy and security.
The issue of confidentiality is that users can not be excluded from monitoring in certain cases (eg checking banking information).






