Fabian Wosar of Emisoft has been able to develop a tool that is capable of decoding files encrypted by DecryptorMax ransomware, also known as CryptInfinite.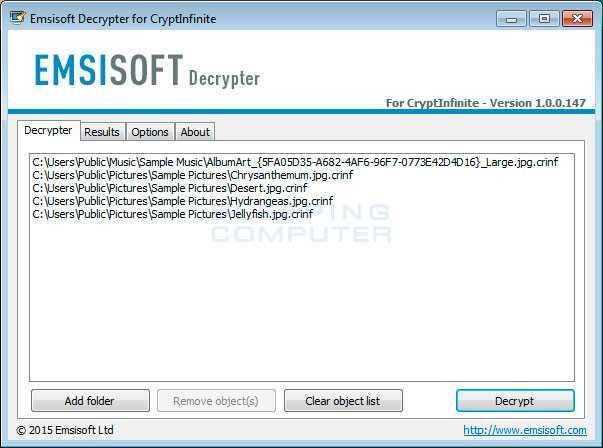
Infection occurs when victims open a Word document and enable macros to view the file properly. Word macros are a known security issue used by many developers malicioussoftware to distribute malware to Windows computers.
Έτσι αν το ransomware εγκατασταθεί στον υπολογιστή του θύματος, αρχίζει αμέσως την encryption των αρχείων που συναντά μπροστά του, προσθέτοντας την επέκταση .crinf σε όλα τα κατεστραμμένα αρχεία.
Immediately after the Ransom informs the user that they have 24 hours to send them ransom via PayPal or MyCash to one of three email addresses: silasw9pa[at]yahoo.co.uk, decryptor171[at]mail2tor.com and decryptor171[at]scramble.io.
In addition, the ransomware changes the desktop wallpaper with a ransom note, then deletes all copies of Volume Shadow, and disables the Windows startup repair function so that the victim cannot restore previous backups.
Here comes the Wosar tool, called DecryptInfinite, and is quite easy to use. It will allow you (if you are affected by DecryptorMax) to unlock your files without paying the ransom.
The tool will calculate the decryption key needed to decrypt the files. Of course, this is a time-consuming one procedure, and you will need to arm yourself with patience, to use DecryptInfinite.
More details on how to use DecryptInfinite and how the tool works, you can find the forum to find a topic of its forum Bleeping Computer.
Download the tool
http://emsi.at/DecryptCryptInfinite





