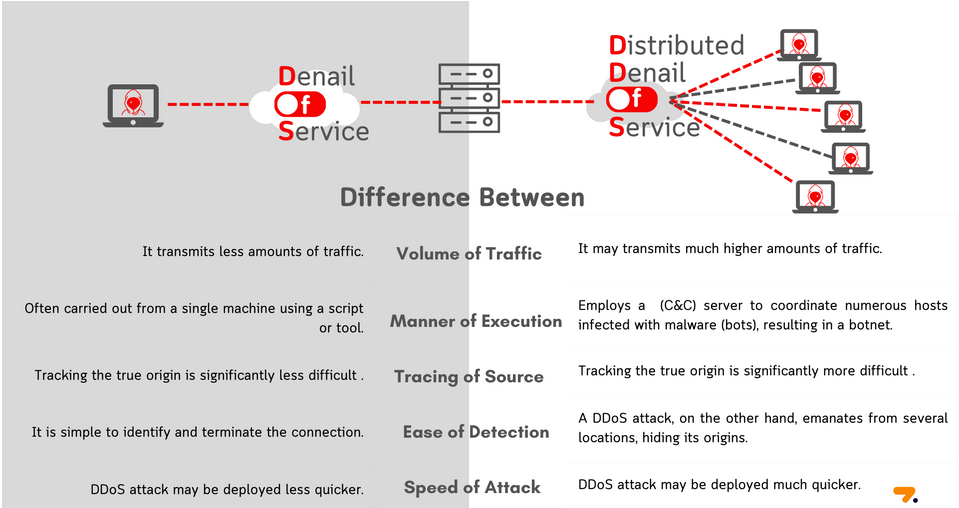
A DoS attack uses a computer to flood a system with data requests to the point that the system crashes. A DDoS attack has the same goal, but uses an entire network of computers, making the attack much more difficult to stop.
DDoS and DoS attacks are some of the most common cyber attacks we see, but how do they actually work? We'll break down each and see how they differ, as well as how you can protect yourself from both.

What is a DoS attack?
A Denial of Service (DoS) attack floods a system with requests for data, eventually overwhelming it with so much input that the system crashes, unable to cope. This usually happens with websites, with the end result that by clicking here to shut down and become unresponsive, depriving users of any service that particular website might normally provide – hence the name “denial of service attack”.
Unlike DDoS attack, DoS attack uses only one source to overload the system. It is a computer with an internet connection that sends a flood of requests with the goal of crashing the target system.
Because DoS attacks tend to be small-scale, they typically target smaller websites and people with more limited resources than large corporate websites like, say, Amazon or Google.
The good news is that because they come from a single source, DoS attacks are easier to stop than DDoS attacks. There is only one source, so once the DoS source is identified, it can be blocked (often by IP address) to stop the attack.
What is a DDoS attack and how does it work?
DDoS (Distributed Denial of Service) attacks have the same goal as DoS attacks, but they are carried out by using a network of computers connected to the internet to flood a target server from multiple points, causing it to receive far more traffic than it could handle. handle a typical DoS attack.
DDoS attacks are often performed with a botnet, a network of computers under the control of the attacker, usually through a malware or virus infection that allows the attacker to use a host's resources. Cyber attackers infect many computers over time, creating a network of machines, and then launch a DDoS attack once they have enough computing power at their disposal.
Because they can be much more powerful than a DoS attack, DDoS attacks can also be used in conjunction with ransomware attacks by criminals who render a system inoperable until a ransom is paid. They are also harder to track as they use multiple devices that can be located anywhere in the world with an internet connection. For this reason, DDoS attacks are considered a higher threat than a typical DoS attack.
Common forms of DDoS attacks include volume-based (or volumetric) attacks and attacks on DNS servers. Volumetric attacks target a network's bandwidth and clog it with requests. A DNS server attack hacks the system's domain name system (DNS) servers, spoofs IP (internet protocol) addresses, and then uses these fake IP addresses to send tons of fake information and overwhelm the target server.
DDoS vs. DoS: What are their differences?
To recap, there are a few key differences between DDoS and DoS attacks:
- Number of machines involved – DoS attacks use one device and one internet connection, while DDoS attacks use many – as many as the attacker can get their hands on.
- Threat level – DoS attacks are generally considered less of a threat than DDoS attacks because there is only one source, which can be blocked once detected.
- Use of malware – DoS attacks usually do not involve malware, while DDoS attacks can use malware to infect computers and form a botnet.
- Difficulty level – DoS attacks are easier to perform than DDoS attacks because all that is needed is a machine and an internet connection.
It is also more difficult to protect against a DDoS attack than a DoS attack, since a DDoS attack can hit a system from many more points, sending much more data than a DoS attack at once.
How to protect yourself from DDoS and DoS attacks
As usual, when it comes to cyber threats, the best defense is to make yourself as difficult a target as possible. Make sure your anti-virus and anti-malware software is up to date. Do not click on suspicious links. Check that the websites you visit use TLS or SSL encryption (look for the small lock icon next to the URL) and, if possible, enable “https” browsing for all the pages you visit.
At the organizational level (businesses, institutions, etc.), configuring a firewall that allows only trusted IP addresses to pass through is also a good solution. Cisco has a guide on how to do this. You can also invest in tools like equalizers loadh, firewalls and user authentication. Limiting the number of points accesss on the Internet can also limit entry points into your system for malicious hackers.
After you've implemented your security measures and threat mitigation plan, regularly test your security to make sure it's still strong and patch any weaknesses you might find.





