Every hacker's Holy Grail is to develop a Zero-Day exploit, one that has never been seen by antivirus (AV) or intrusion detection system (IDS) developers. This way, the hacker can exploit the systems with the newly discovered vulnerability without being detected!
To get a zero-day you have at least two options: (1) develop your own or (2) take someone else's exploit.
Developing your own exploit can be a long and tedious process and requires significant knowledge of assembler, fuzzing, shellcode, etc. The process can take countless working days. Hackers and government intelligence agencies invest millions of dollars to develop zero-days, but in some rare cases, private individuals manage to develop zero-days with little effort, especially on old systems. (The zero-day that breached Target several years ago was developed by a 17-year-old hacker in Russia, but it targeted Windows XP, which Target still uses in point of sale (POS) systems).
The other approach is to take a zero-day that others have developed and reuse it. You remember her exploits Hacking Team that were released when Hacking Team was hacked? This approach has long been used by AV developers, forensic scientists, and in some cases, hackers. In fact, the recent Vault 7 release showed that the CIA is taking Zero-Day malware and using it for their own purposes.

What we want to do in this series of guides is install and configure a honeypot that looks both vulnerable and realistic. We then wait for it to attract the attackers and then capture their malware when they have successfully breached our system.
If we are malware analysts software, we can then analyze the malware and perhaps develop a defense against it or a signature. If we are hackers, we might be able to reuse the malware on other systems. In some cases, we may need to redesign the malware for other purposes, but this is still much faster and more efficient than starting from scratch. The key is to be able to catch the malware first.
Dionaea
Dionaea was developed by Markus Koetter as a low interaction honeypot. Simulates a vulnerable Windows system with services that attackers often target, such as HTTP, FTP, SSH, SMB, etc. It is written in C, but uses Python to emulate various protocols to lure attackers.
Dionaea is named after the plant genus that includes the carnivorous Venus flytrap. I think the symbolism is obvious. Probably most importantly, it uses Libemu to detect shellcode and can notify us when it catches it. Dionaea sends real-time notification of attacks via XMPP and then records the information in a SQLite database.
Libemu
Libemu is a library used for x86 emulation as well as shellcode tracing, which is perfect for our honeypot in this guide. It can pull malware from the web or from within documents (PDF, RTF, etc.), which we can then use to analyze for malicious behavior using specific attributes.
This is a relatively advanced honeypot and should not be attempted by beginners. Additionally, I recommend that you do NOT use it on a system that will be used for other purposes, as we will be installing libraries and other code that may disable other parts of our system.
Additionally, Dionaea is meant to be vulnerable. This means that if it is compromised, our entire system can be compromised. You should use a clean install, preferably a Debian or Ubuntu system. I will be using a clean install of Ubuntu 14.04.
Step 1: Install dependencies
Dionaea is a complex piece of software and requires many dependencies that are not usually installed on Ubuntu or other Debian distributions. As a result, we should install the dependencies before installing and configuring Dionaea. This can be a long and tedious process.
For example, to get started we need to download the following packages.
ubuntu > apt-get install libudns-dev libglib2.0-dev libssl-dev libcurl4 - openssl - dev libreadline-dev libsqlite3-dev python-dev libtool auto make autoconf build-essential subversion git-core flex bison pkg-config libnl-3-dev libnl-genl-3-dev libnl-nf-3-dev libnl-route-3-dev sqlite3
Fortunately, Andrew Michael Smith has developed one script που κάνει όλη τη δύσκολη δουλειά για εμάς. Μπορούμε να κατεβάσουμε το script του από το GitHub using wget.
ubuntu > wget -q https://raw.github.com/andrewmichaelsmith/honeypot-setup-script/master/setup.bash -O /tmp/setup.bash && bash /tmp/setup.bash
This script will download and install all dependencies (there are many) and applications (p0f, SQLite and others), then download and install and configure Dionaea.
Be patient as this may take some time.
Step 2: Select interface
After downloading all the applications and dependencies, Dionaea will start configuring and ask you to select the network interface you want the honeypot to listen on. Here, I have chosen the eth0 interface, but yours may be different.
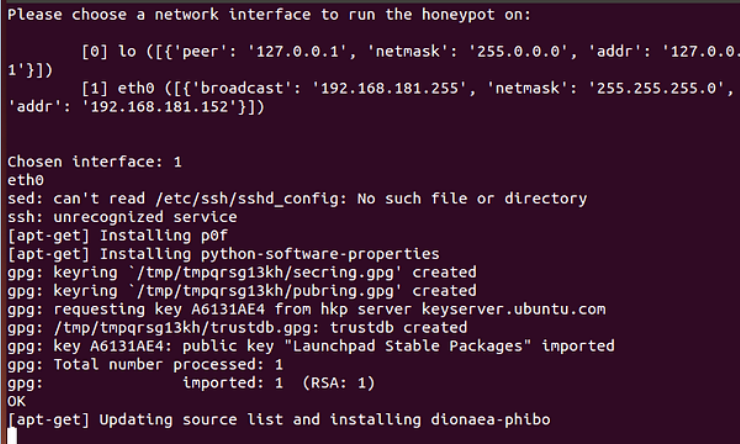
The download and installation will complete and you will be presented with a screen telling you that p0f and Dionaea have started.
Step 3: Test the installation
Once the above process is complete, we can check if Dionaea has been installed correctly and completely by typing:
ubuntu > dionaea -Help
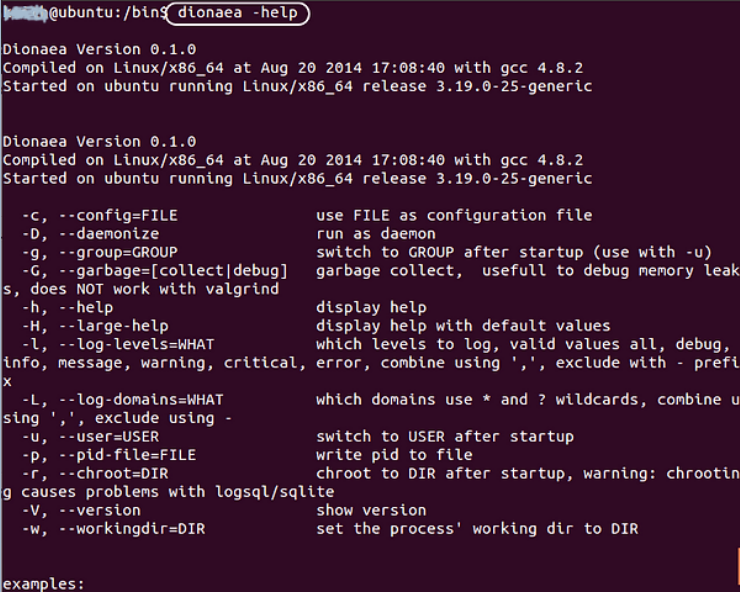
If the help screen you see above appears, you have successfully installed Dionaea. Congratulations!
Dionaea configuration
Now our honeypot is up and running. In the next guide in this series, I'll show you how to configure Dionaea to alert you in real-time about attacks, how to identify attackers' credentials (OS, IP, browser, interface), and how to capture and analyze the shellcode of the attack.





