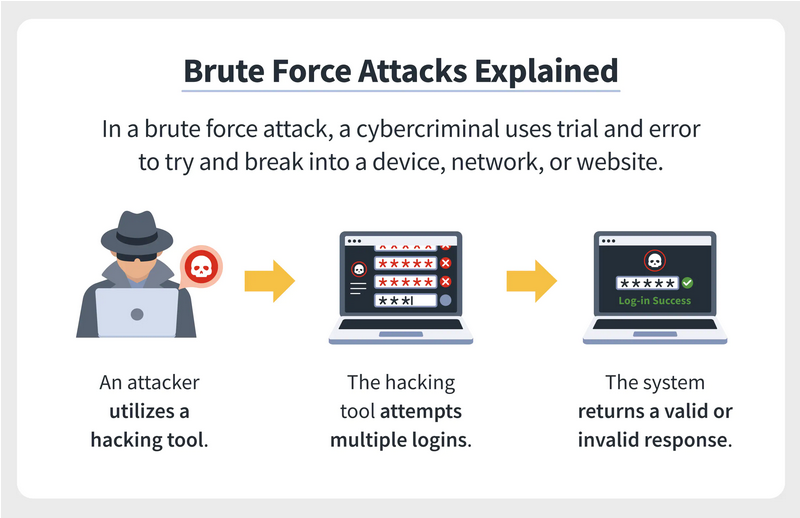
There are many ways that the hacker to enter a computer, computer network, website or online service.
The execution of one Brute Force Attack is one of them.
It is one of the simplest, but time-consuming methods to gain access to a server or a regular computer. The Brute Force attack mechanism has its advantages. It can also be used to check network security and recover forgotten passwords.
In this post we will try to understand how to do a Brute Force attack and see the basic method preventionς
Types of Brute Force Attacks
The most basic Brute Force attack is the dictionary attack, where the attacker processes a dictionary of possible passwords and tries them all. Dictionary attacks start with some assumptions about common passwords that they try to guess from the dictionary list. These attacks tend to be somewhat outdated given newer and more effective techniques.
Recent computers built in the last 10 years or so can brute force an 8-character alphanumeric password – upper and lower case letters, numbers and special characters – in about two hours. Computers are so fast that they can brute force a weak encryption hash in a matter of months. These types of Brute Force attacks are known as , where the computer tries every possible combination of every possible character to find the correct combination.
The technique is another type of Brute Force attack that reuses usernames and passwords from other data breaches to try to get into other systems.
The attack uses a common password, such as “password”, and then tries to brute force a username that matches that password. Since “password” is one of the most common passwords in 2017, this technique is more successful than you might think.
Motivations Behind Brute Force Attacks
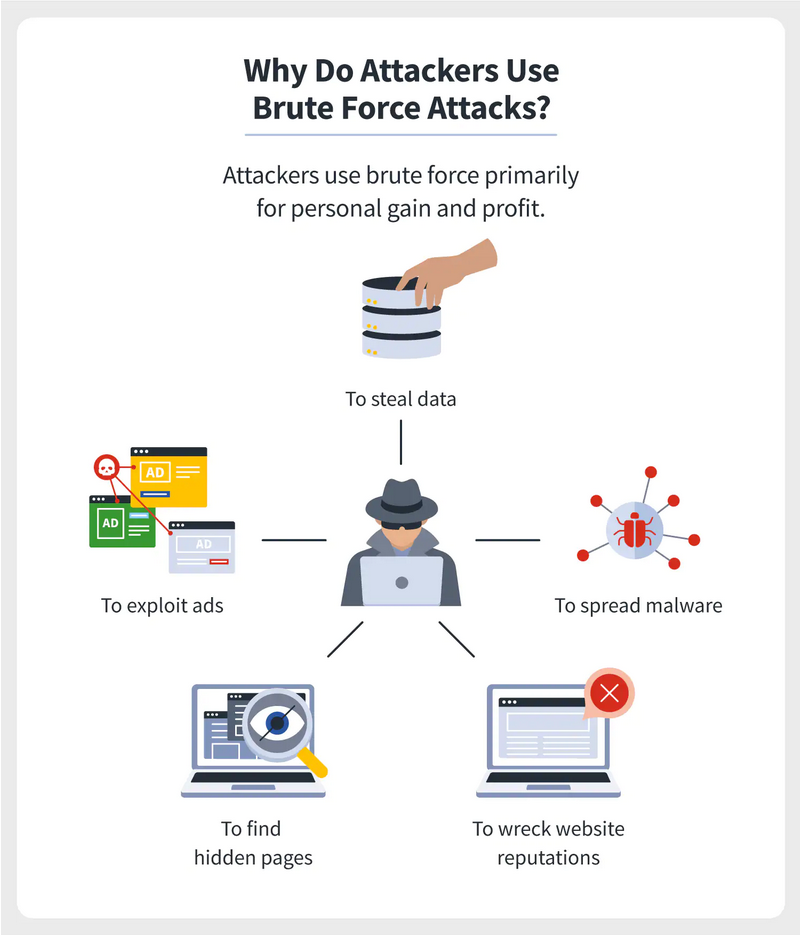
Attackers need access or entry points to their targets, and Brute Force techniques are a “set it and forget it” method of gaining access. Once inside the network, attackers can use brute force techniques to escalate their privileges or perform encryption degradation attacks.
Attackers also use Brute Force attacks to search for hidden web pages. Hidden websites are websites that exist on Internet, but they are not linked to other pages. A Brute Force attack tries various addresses to see if they return a valid web page and will look for an exploitable page. Things like a software vulnerability in the code that they could use to break in – like the vulnerability that was used to break into Equifax, or a website that has a list of usernames and passwords exposed to the world.
There is little finesse to a Brute Force attack, so attackers can automate several attacks to run in parallel to widen their options for finding a positive – for them – outcome.
How to Defend Against Brute Force Attacks
Brute Force attacks take time to execute. Some attacks can take weeks or even months to yield something usable. Most of the defenses against brute force attacks involve increasing the time required to succeed beyond what is technically possible, but this is not the only defense.
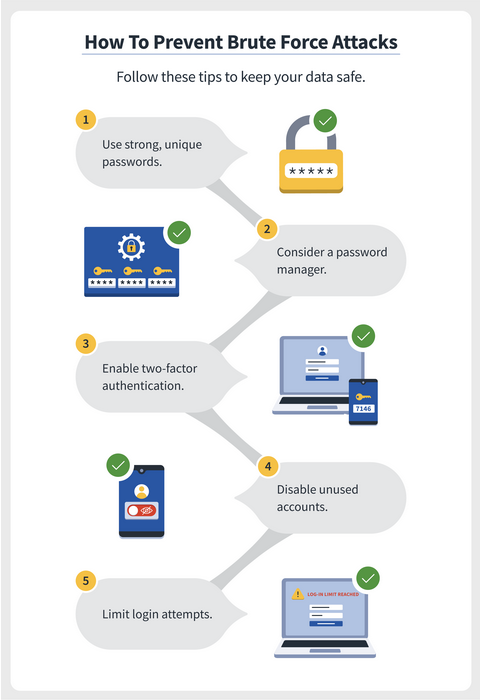
- Increase password length: More characters equals more time to crack a code.
- Increase password complexity: More options for each character also increase the time to break them with Brute Force.
- Limit login attempts: Brute Force attacks increment a failed login attempt counter on most directory services – a good defense against Brute Force attacks is to lock users out after a few failed attempts, thereby canceling a Brute Force attack you find in progress.
- Implement Captcha: Captcha is a common system for verifying human identity on websites and can stop Brute Force attacks in progress.
- Use multi-factor authentication: Multi-Factor Authentication adds a second layer of security to any login attempt that requires human intervention, which can prevent a Brute Force attack from succeeding.
It is better to detect an attack in progress and actively stop the attack than to hope that your passwords cannot be cracked. Once you detect and stop the attack, you can even blacklist the IP addresses and prevent further attacks from the same computer.
What is a Brute Force Attack?
A Brute Force attack, or exhaustive search, is a cryptographic breach that uses trial and error to guess possible combinations for passwords used for logins, encryption keys, or web pages.
FAQ
What is an example of a Brute Force attack?
If you have a password that is only one character long, using numbers and letters (uppercase and lowercase), there will be 62 different possibilities for that character. A Brute Force attack would try all possible characters at once to try to learn your single character password. With normal passwords being around 8 characters, the possibilities multiply into the trillions, which might take a bot only seconds to try.
How does a Brute Force attack work?
Essentially, a bot tries every combination of numbers and letters to learn your password. A reverse Brute Force attack guesses a popular password based on a list of usernames.
What is the best protection against a Brute Force attack?
The best protection against a Brute Force attack is to ensure your passwords are as strong as possible, slowing down the time it takes a hacker to breach the system and increasing the likelihood that they will give up and move on.
What can attackers gain?
- Access to personal data
- Access to your system for malicious activity
- Ability to edit your site and ruin your reputation
- Potential to spread malware
- Earnings from ads or your activity data
After all, how successful are Brute Force attacks?
Over 80% of breaches involve brute force attacks or the use of lost or stolen credentials. Brute force attacks are something you should be concerned about when protecting your data by choosing encryption algorithms and passwords. It is also a reason to keep developing stronger cryptographic algorithms, where encryption must keep pace with how quickly it is rendered ineffective by new hardware as well as new programs.





