Keyloggers can be installed on your computer and mobile phone in various ways and for various reasons. Knowing how to detect and remove keylogging software is important to maintaining your digital privacy and protecting your sensitive data from theft and misuse.

What is a Keylogger?
A keylogger, also known as a keystroke logger, is a type of spyware that can be installed on a computer, phone or tablet to monitor and record your keystrokes and touches. Some keylogging software can also record mouse movements, screen images, selected website links, and other user input actions.
When a keylogger is active, everything from typed passwords and account information to private emails post officey and the searches you perform on the site are recorded in a log file, which can then be retrieved and read by anyone with access to the keylogger's backend.
Keyloggers are often associated with infection by other types of malware, but not always. A keylogger could also be deployed by parents, suspicious spouses, a rival business, or just about anyone who wants to secretly monitor what is being typed or entered on a particular device.
Keylogging software is not illegal, but the way it is used may be. Some companies openly use keyloggers to ensure that employees are not using company time and equipment for personal tasks, such as browsing social media or conversation with friends.
Keylogging Software vs. Hardware
There are two main types of keyloggers: software and hardware.
Keylogger software is installed invisibly on the device to be monitored, often together with other malware. You won't see any app icons or settings that indicate it's installed, although some keylogging software hides in plain sight using another seemingly innocent app icon. The logs can then be automatically sent over the network or emailed without your knowledge. This can happen with almost any program, perhaps several times a day.
Hardware keyloggers must be physically connected to the computer. This sometimes means that a specialized USB device is plugged into a spare USB port, but often between the wired keyboard and the computer. A hardware keylogging device could very easily go unnoticed very easily.
Keyloggers usually use built-in storage. This means that the keylogging device will have to be recovered by whoever placed it there, before the recorded data can be downloaded and read.
How to detect Keyloggers on your computer
Hardware keyloggers are usually easy to detect. Just look at the back of your computer and check for any unusual devices in the USB ports or connected to your keyboard cable. Just make sure you don't accidentally remove a legitimate USB adapter.
Detecting keylogger software can take more time and effort, but it can be done if you know what to look for.
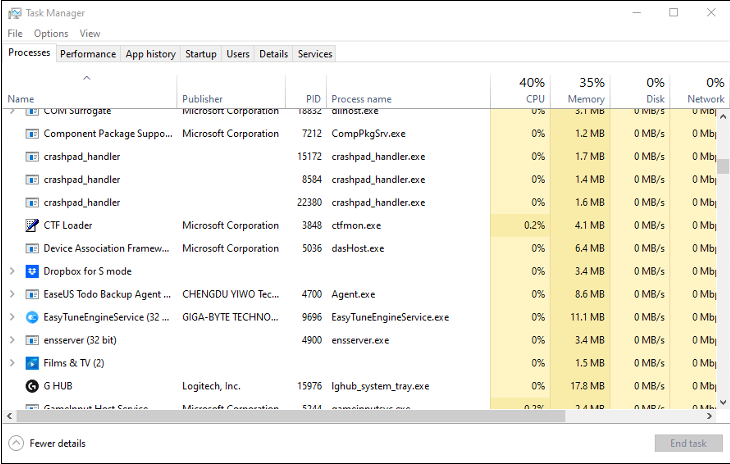
Look for unusual processes in Task Manager
For Windows users, the first place to look for keylogger software is the Task Manager. Expand the Task Manager to display details and add the columns to display publisher names. You can then scroll through the list of processes to find any unusual entries.
Do a web search for any suspicious process names to see if they are related to keyloggers. You can also try typing in a text document while monitoring activity in Task Manager. If the activity of an unknown process increases while typing, investigate it.
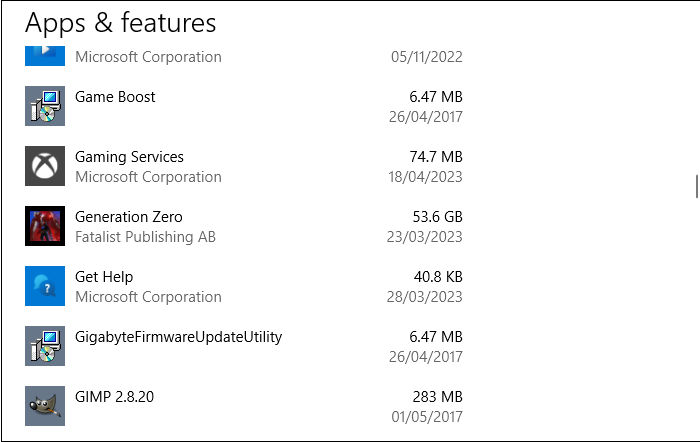
Check your app list for unusual apps
Check the list of installed software for any applications or programs that appear to be unknown. It's highly unlikely that a keylogger is called a “keylogger,” so look for apps you don't remember installing.
If you're not sure about an app's legitimacy, do some online research to see if it could be a keylogger in disguise.
4 indications that o computer you have a keylogger
Few of us randomly check the back of our computers or scan Task Manager for unexpected processes, but luckily there are several common signs that a keylogger is at work on your computer.
- A browser with slow or strange behavior, such as lags when you click a link or use the search function.
- Input lag when typing or clicking on the mouse/trackpad.
- The mouse pointer disappears for a few minutes during the duration of use.
- Unexpected or frequent app and system crashes.
While it's true that some or all of these can also be a sign of different computer problems, they should at least prompt you to investigate them further, especially if you're experiencing them all at the same time.
How to Remove a Keylogger
If you find the keylogger while inspecting your running processes or applications, you should be able to delete or uninstall it manually. Unfortunately, keyloggers often disguise themselves as legitimate software, which can make their detection and removal more difficult.
The best way to remove a keylogger is to use antivirus software. Run a full or deep scan using up-to-date software, and if the software includes a dedicated keylogger scanner, use it. When a keylogger is detected, you will be given the option to remove it.
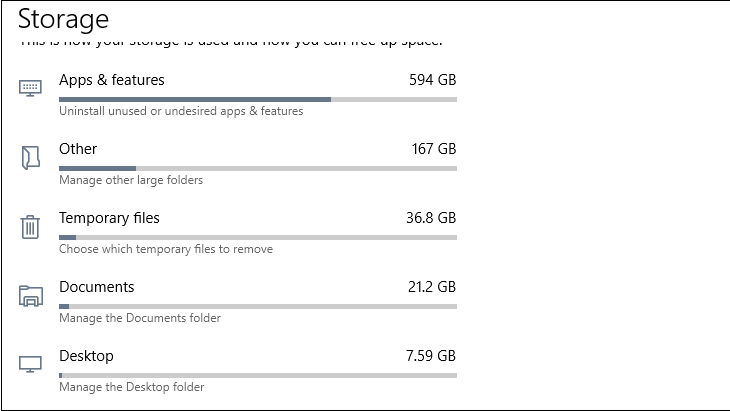
Your temporary files folder is often a cluttered and easily forgotten place, perfect for keylogging software to hide. Clearing your Temporary files and then repeating the process regularly will mean one less place for spyware to lurk.
If all else fails, resetting your computer should remove even the most persistent keylogger. This is clearly a pretty drastic solution, but only if you build it right backups of your files, a full restore is not as time-consuming and difficult as it used to be.
Prevent future keylogging attacks
The best ways to prevent keylogging attacks in the future are to choose reliable antivirus software and keep it up to date, along with your system software. Most popular antivirus software will provide you with at least some protection from keylogger software.





