The Slovak security company ESET has discovered a new hacking group funded by a state (these groups are also known as APT). Named XDSpy, the team managed to go unnoticed for almost nine years before its action was discovered.
The group's work was first presented today by researchers of ESET in a speech at the Virus Bulletin 2020 security conference.
ESET said the team 's main interest was in identifying and stealing documents. It targeted government agencies and private companies in Eastern Europe and the Balkans.
The target countries were Belarus, Moldova, Russia, Serbia and Ukraine, according to ESET telemetry data, but there are other XDSpy functions that have not been discovered.
ESET reports that the group's activities have ceased after tracking its activities and a detailed safety report sent in the CERT Belarus team.
Using this security alert as an initial clue, ESET was able to uncover XDSpy's past operations. Matthieu Faou and Francis Labelle, two ESET security researchers who led the investigation into XDSpy, said the team's main tool was a toolkit maliciousυ software which they called XDDown.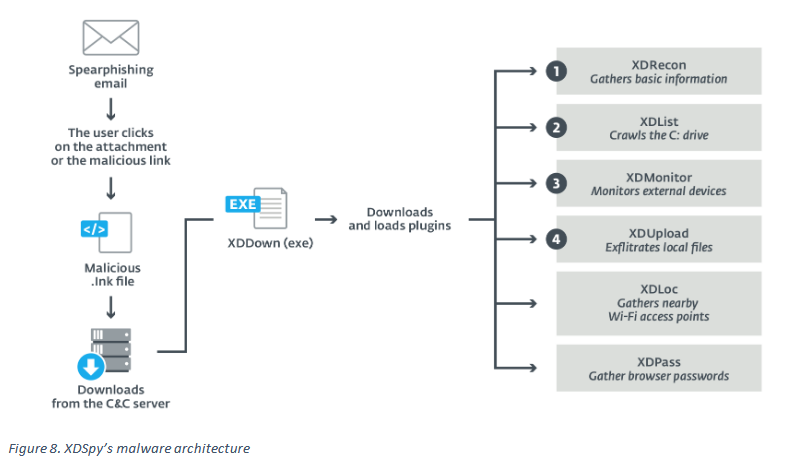
The malware, described by Faou as "not state-of-the-art", could infect its victims and help the team collect sensitive data from infected targets.
ESET describes XDDown as a “downloader” that was used to contamination of a victim and then to download secondary tools that performed various specialized tasks.
Let's look at the tools that ESET has discovered
XDREcon - tool for scanning an infected server, collecting technical specifications and operating system details and sending the data back to the XDDown / XDSpy command and control server.
XDList – εργαλείο για αναζήτηση αρχείων με συγκεκριμένες επεκτάσεις αρχείων (archives που σχετίζονται με Office, PDF και βιβλία διευθύνσεων).
XDMonitor - a tool that tracks the type of devices connected to an infected host.
XDUpload - tool that uploads stolen files to XDXpy server.
XDLoc - a tool for gathering information from nearby WiFi networks, information believed to have been used to track victims' movements using public WiFi network maps.
XDPass - a tool that extracted passwords from locally installed browsers.





