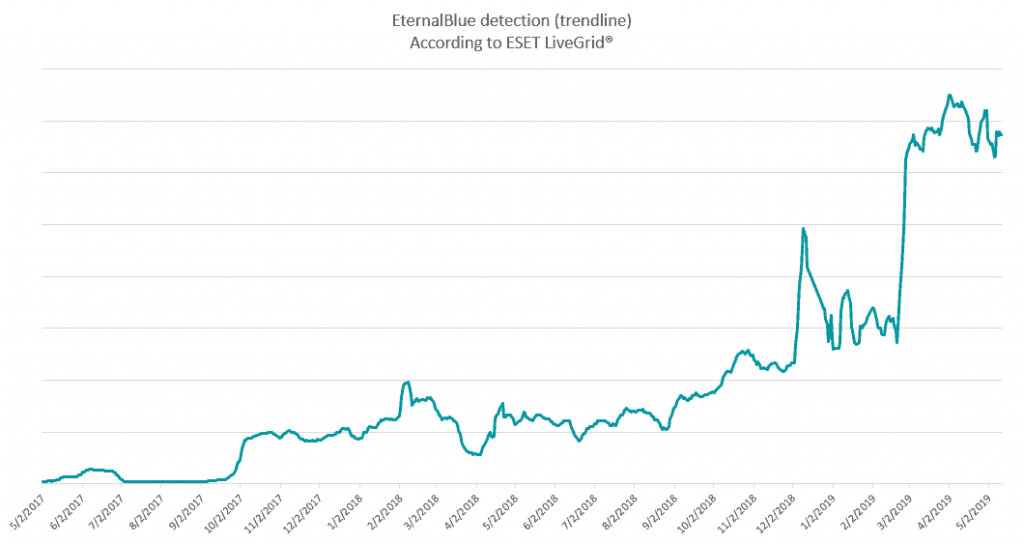
According to telemetry of ESET, attacks based on EternalBlue exploit have reached historically high levels, with users being bombarded with hundreds of thousands of attacks each day.
It has been two years since the exploit EternalBlue opened the door to one of the most violent cyber attacks in history, known as WannaCryptor (or WannaCry).
Since then, attempts to abuse the specific vulnerability have been greatly increased by the particular exploit, and are currently at their peak, as ESET researchers report.
The EternalBlue exploit was reportedly stolen by the NSA on 2016 and released on April 14 by a group of cybercriminals known as Shadow Brokers. The exploit targets a vulnerability in the implementation of the SMB (Server Message Block) protocol via the 2017 port.
Although Microsoft had released a patch, and even before the launch of WannaCryptor 2017, there are still vulnerable systems around the world today, possibly due to inadequate security practices and patch updates.
EternalBlue is responsible for many cyber-attacks, such as Diskcoder.C (also known as Petya, NotPetya and ExPetya) and BadRabbit in 2017. Also, well-known cybercriminals such as the Sednit group (aka APT28, Fancy Bear and Sofacy) have used it to attack hotel Wi-Fi networks. Recently, EternalBlue was held responsible for the spread Trojans και malware εξόρυξης κρυπτονομισμάτων στην Κίνα.
According to ESET researchers, this exploit and all cyber attacks emphasize the importance of timely patching. In addition, they emphasize the need for a reliable and multilevel security solution that can do much more than just stop transport of malicious payload, such as to protect against the underlying mechanism.
______________________
- Anonymous: the end of hacking
- Microsoft, Sony collaboration for game-streaming
- Google Chrome Canary: new configuration page





