Over the weekend, researchers from the information company Cyble they discovered a database with 267 million Facebook user profiles being sold on Dark Web.
Trying to verify the data and add it to the service company's breach notification, the researchers bought the database for £500.

The database entries contained Facebook user IDs, which are unique, public numbers associated with specific accounts, full names, email addresses, phone numbers, timestamps showing the last login, relationship status and age.
Fortunately, they did not exist passwords, but this base is still a perfect tool kit for a e-fishing campaign which seems to come from Facebook itself.
How was the data leaked? In a post, Cyble said it doesn't know, but its researchers suspect the files could come from either a leakage in the Facebook developer API or from some scraping: the automatic collection of available data that you publish on Facebook yourself or on other social networks.
However, the story does not stop there. In fact, it does not even start there. It turns out that the same database had been released in the past. It was spotted by security researcher Bob Diachenko and deleted by the host ISP. Reappeared, larger with another 42 million subscriptions to another server.
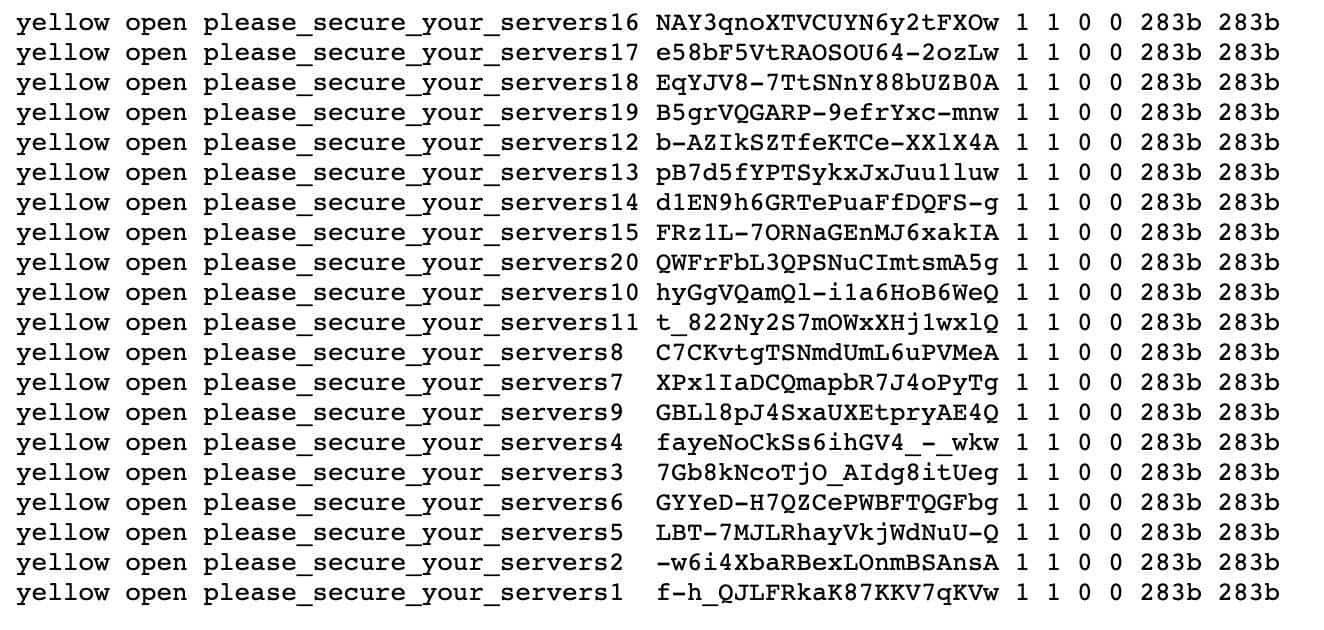
It was then destroyed by strangers who replaced the personal data with virtual data and left the message: "please_secure_your_servers".
Diachenko partnered with the comparison site and researchς Comparitech πάνω σε αυτό το project τον περασμένο μήνα. Η Comparitech ανέφερε ότι η βάση δεδομένων ήταν εκτεθειμένη για σχεδόν δύο εβδομάδες, διαθέσιμη στο διαδίκτυο ελεύθερα χωρίς κάποια προστασία με κωδικό πρόσβασης.
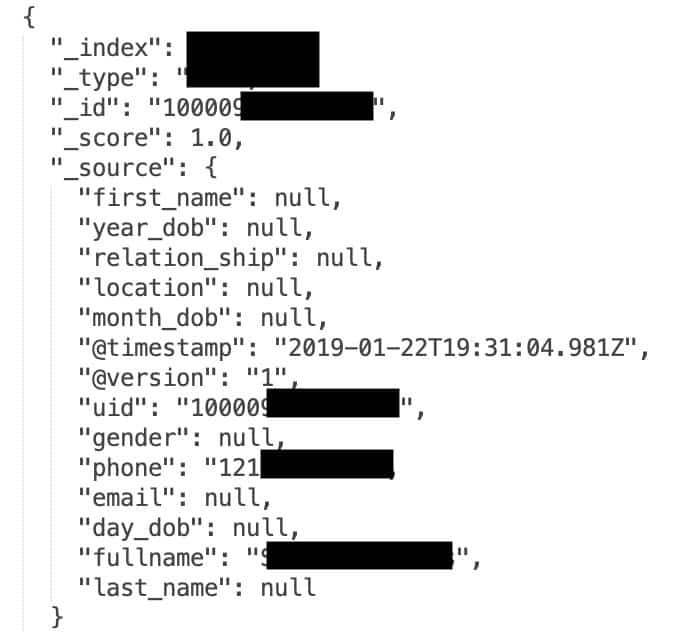
Timetable giving Comparitech:
December 4, 2019: The database is first indexed by search engines.
December 12, 2019: The data was published for download in a hacking forum.
December 14, 2019: Diachenko discovered the database and immediately sent a report to the ISP that managed the IP of the server.
December 19, 2019: Access to the database stopped.
March 2, 2020: A second server containing identical data plus another 42 million was indexed by the BinaryEdge search engine.
March 4, 2020: Diachenko discovers the second server and notifies the hosting provider.
March 4, 2020: The server was attacked and destroyed aby unknown hackers.
The original database contained 267.140.436 records, mostly from Facebook users in the United States. Diachenko said all the files appeared to be valid. The same registrations existed on the second server in March 2020, but this time, there were an additional 42 million registrations.
Comparitech reported that 25 million of the new files contained similar information: Facebook IDs, phone numbers and usernames. However, the 16,8 million records had even more, such as gender, email address, date birth and other personal data.
Both Cyble researchers and Diachenko himself do not know how leakage, but both agree that it could be from a security flaw in Facebook's third-party API that existed before the platform restricted access to phone numbers, or that allows malicious users to steal user IDs and phone numbers even and when Facebook restricted access to the API.
Both Cyble and Diachenko argue that alternatively, the leak may come from scraping, which is a good reason to reconsider how much data you share publicly on Facebook.
In other words …
Stop exposing yourself!





