For the past nine years, Mozilla has been using an insufficiently powerful encryption engine for Firefox's "master password" function (and beyond).
Both Firefox and Thunderbird allow users to create a "master password" through the application settings panel. 
This master password acts as an encryption key used to encrypt each string of passwords stored in the program touror your email client.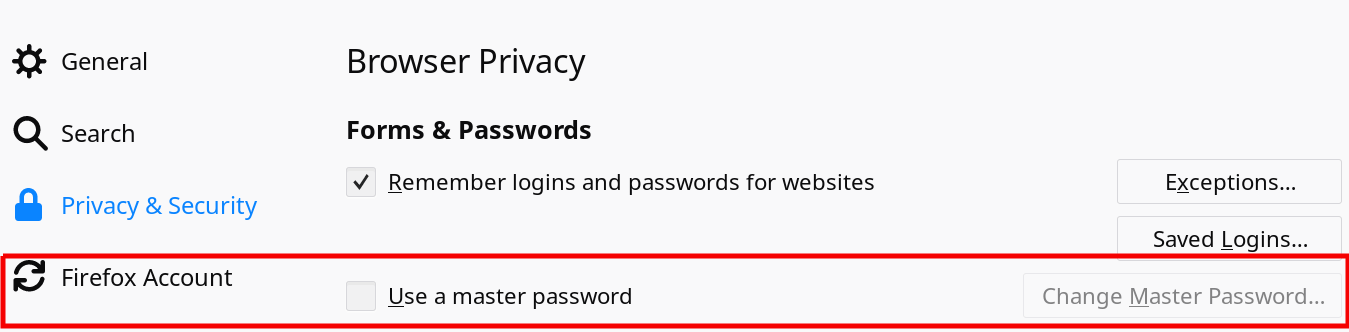
Experts initially praised the feature, because back then all browsers stored them locally codeof access in plain text, leaving them vulnerable to any malicious software or those who had physical access to the victim's computer.
But Wladimir Palant, its developer extensions AdBlock Plus, reports that the encryption scheme used by Mozilla's applications is weak and can be easily broken.
"I searched for the source code," says Palant, "and I finally found the sftkdb_passwordToKey () function that converts a password into an encryption key by applying SHA-1 hashing to a crypto-string consisting of a random salt and real password."
Palant he says the fact that the SHA-1 function only makes a repeat, which means it only applies once, while you can safely say an encryption if the reps are applied at least 10.000 times. Apps like LastPass for example use 100.000 reps.
This low number of iterations makes it incredibly easy for an attacker to break the master password and later to decrypt all the encrypted passwords stored in the Firefox or Thunderbird databases.
Palant points out recent advances in GPU card technology now allow attackers to read simple passwords in less than a minute.
Here is to mention that Palant was not the first to discover this weakness. A Mozilla Error Log by Justin Dolske nine years ago, mentioned the same issue shortly after the master password was released.
Dolske also pointed out that the low level of repetition (once) is the main problem of the master password. However, despite his mention errorMozilla did not take any action for several years.
Only until last week, when Palant repeated the bug report, Mozilla responded formally, saying the security gap would soon be corrected with the release of Firefox's new password management feature, called Lockbox and will be available as an extension.
At the moment, what can protect you somewhat above is choosing larger and more complex basic passwords.
Those of course who do not want to use a third-party password management application would prefer to use a third-party password management application. OR Keepass is the one we use, provides security and saves all the codes locally and not in the cloud.





