More information and details about the action as well as the methodology followed by the perpetrators can be found below.
Cryptocurrency mining operation by a Turkish-speaking entity, which uses “Google Translate Desktop” and has recorded over 111.000 downloads in at least 11 countries since 2019

Check Point Research (CPR) has discovered an active cryptocurrency mining campaign impersonating “Google Translate Desktop” and other free software for contamination of computers. The campaign has been created by a Turkish-language entity called Nitrokod and has 111.000 downloads in 11 countries as of 2019.
Attackers delay the infection process for weeks to avoid detection. CPR warns that attackers can easily choose to change the malware, changing it from a crypto miner to ransomware or banking trojans, for example.
- The campaign promotes malware through the free software available on popular websites such as Softpedia and uptodown.
- The malware is taken from knock-offs of apps that are popular but don't have real desktop versions, such as Google Translate
- Victims have been reported in the UK, US, Sri Lanka, Greece, Israel, Germany, Turkey, Cyprus, Australia, Mongolia and Poland
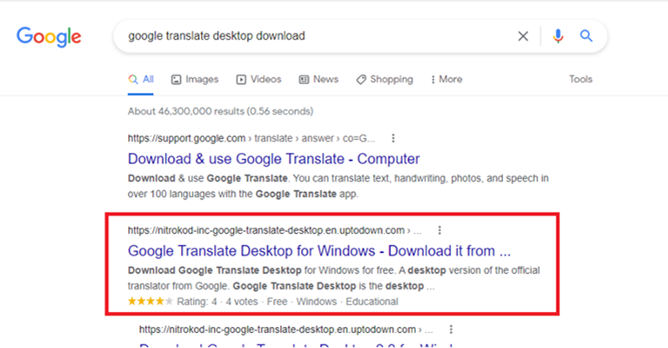
The campaign promotes malware through free software available on popular websites such as Softpedia and uptodown. It can also infect a device easily through Google when users search for “Google Translate Desktop download. After the initial software installation, attackers delay the infection process for weeks by erasing traces of the initial installation.
Image 1. Αsearch results for "Google Translate Desktop download"
Unnoticed for years
The campaign has been operating successfully under the radar for years. To avoid detection, the creators of Nitrokod implemented some basic strategies:
- The malware first runs almost a month after installing the proletterof Nitrokod
- Malware is delivered after 6 previous stages of infected programs
- The chain of infection continues after long delay using a scheduled task mechanism, giving attackers time to clean all their assets
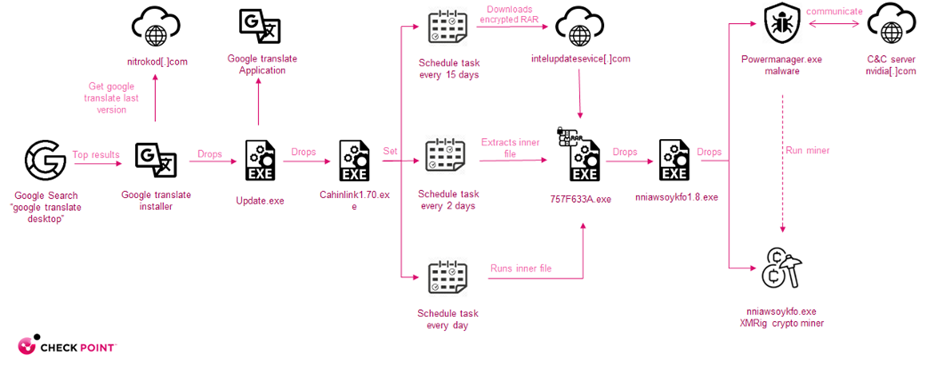
The Chain of Infection
- The infection starts with the installation of an infected program downloaded from the web
- Once the user launches the new software, a copy of Google Translate is installed. Additionally, an update file is saved to disk, which starts a series of four droppers until the actual malware is installed
- After running, the malware connects to the C&C (Command & Control) server to get a configuration for the XMRig crypto miner and starts the mining activity
Figure 2. Infection chain map
List of countries with victims:
- United Kingdom
- USA
- Sri Lanka
- Greece
- Israel
- Germany
- Turkey
- Cyprus
- Australia
- Mongolia
- Poland
Comment from Maya Horowitz, VP of Research at Check Point Software:
“We discovered a popular website that serves malicious versions through imitations of desktop applications, including Google Desktop and others, which include a cryptocurrency miner. Malicious tools can be used by anyone. They can be found with a simple web search, downloaded from a link, and installed with a simple double click. We know that the tools are made by a Turkish-speaking developer.
Currently, the threat we identified was the unknowing installation of a cryptocurrency miner, which steals computer resources and leverages them to make money for the attacker. Using the same attack flow, the attacker can easily choose to change the final payload of the attack, changing it from a crypto miner to, for example, a ransomware or banking Trojan.
What is most interesting to me is the fact that the malware, despite being so popular, went undetected for so long. We have eliminated the threat to Check Point customers and are publishing this report so others can be protected.”
Cyber Safety Tips:
Cyber Security Tips:
- Beware of domains that look really similar, in orthographics errors on websites and unknown email senders
- Download software only from authorized, well-known publishers and suppliers
- Prevent zero-day attacks with a holistic, end-to-end cyber architecture
- Make sure your terminal security is up-to-date and provides comprehensive protection





