A Twitter user posted a repository link containing around 20 GB of Intel copyright (IP), including source code, processor production documentation, and more.
The violation was allegedly committed earlier this year by an anonymous person.
The tweet states that the information is in his hands hacker from the breach are highly confidential and subject to non-disclosure agreements (NDA). The post contains a list of the breached data, adding that "the good and most private" ones will be released in the future.
The contents of the list include the "Kaby Lake BIOS Reference Code, Intel Camera Drivers Binaries for SpaceX" and more.
There is also information about future generations of processors, which could be harmful if the code falls into the wrong hands.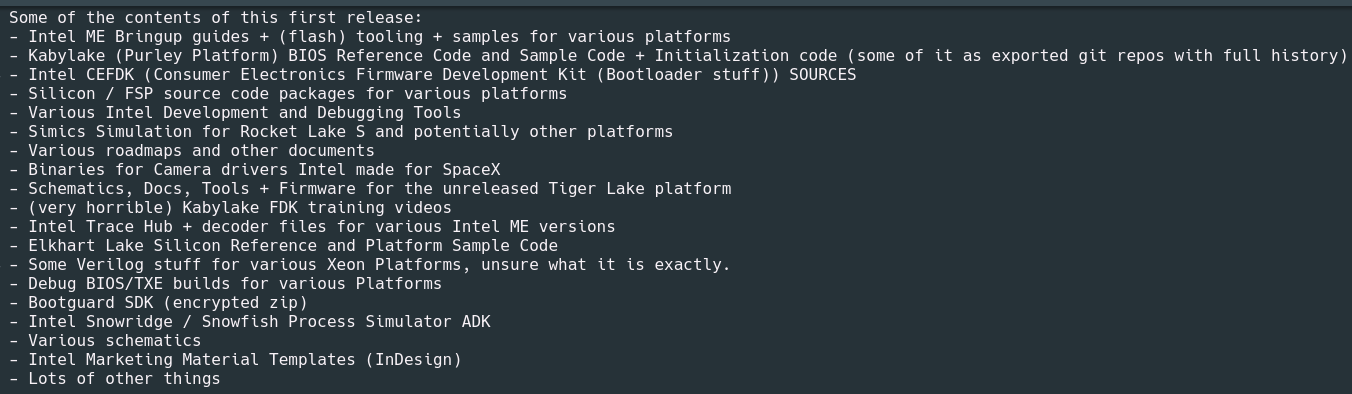
Although the data and files mentioned above may not make sense to most users, they could be used by malicious users to detect potential vulnerabilities.
Having a chance to read the source code they could develop malware that exploits any potential security gaps.
https://twitter.com/deletescape/status/1291405688204402689
As for the company's security policies, read it below message:
If you find password protected zips in the release the password is probably either “Intel123” or “intel123”. This was not set by me or my source, this is how it was acquired from Intel.
We added the tweet that contains the links to the repository but you better not visit it.





