A team hacking APT known as “Dragon Breath”, “Golden Eye Dog” or “APT-Q-27” demonstrates a new trend that uses various complex variations of the classic DLL sideloading technique to evade detection.
These attack variants start with an initial actor leveraging a clean application, most often Telegram, which transfers a secondary, sometimes clean, payload that in turn transfers a malware DLL.
The lure for victims is the applications Trojanized Telegram, LetsVPN or WhatsApp for Android, iOS or Windows purportedly targeted for people in China. Trojan applications are believed to be promoted using BlackSEO or malvertizing.
According to Sophos analysts who have been monitoring the recent attacks, the targeting scope of this campaign is focused on Windows users in China, Japan, Taiwan, Singapore, Hong Kong and the Philippines.
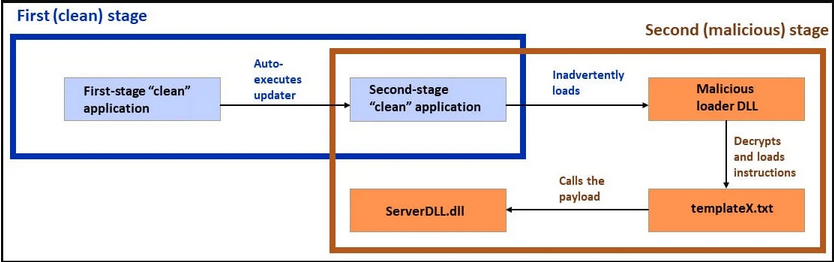
Double DLL sideloading
DLL sideloading is a technique that attackers have been exploiting since 2010, exploiting the way Windows loads Dynamic Link Library (DLL) files required by an application.
Ο επιτιθέμενος τοποθετεί ένα κακόβουλο DLL με το ίδιο όνομα με το νόμιμο, απαιτούμενο DLL στον κατάλογο μιας εφαρμογής. Όταν ο user εκκινεί το εκτελέσιμο πρόγραμμα, τα Windows δίνουν προτεραιότητα στο τοπικό κακόβουλο DLL έναντι αυτού που βρίσκεται στους φακέλους του συστήματος.
The attacker's DLL contains malicious code that is loaded at this point, giving the attacker privileges or executing commands on the host, exploiting the trusted, signed application that loads it.
Victims run the installer of the mentioned apps, which creates a shortcut on the surface.
If the victim attempts to launch the desktop shortcut, which is the expected first step, instead of launching the application, the following command is executed on the system.
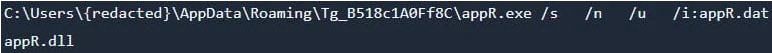
Η εντολή εκτελεί μια έκδοση του ‘regsvr32.exe' (‘appR.exe') για να εκτελέσει μια έκδοση του ‘scrobj.dll' (‘appR.dll') και παρέχει ένα αρχείο DAT (‘appR.dat') ως είσοδο. Το DAT περιέχει κώδικα JavaScript για implementation από τη βιβλιοθήκη της μηχανής εκτέλεσης των scripts(‘appR.dll').
The JavaScript code launches the Telegram app's user interface in the foreground, while installing various parallel loading components in the background.
It then loads an application using a clean dependency ('libexpat.dll') to load a second clean application as an intermediate attack stage.
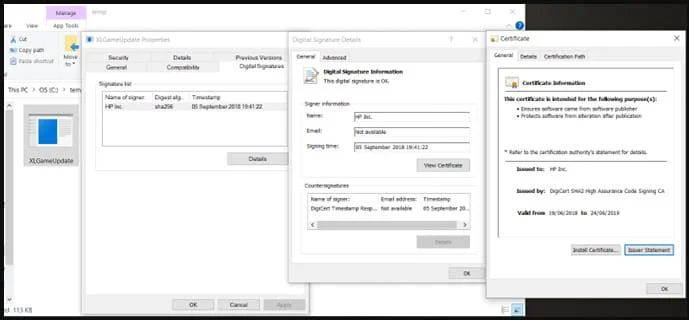
In a variation of the attack, the clean application “XLGame.exe” is renamed to “Application.exe” and the loader is also a clean executable, signed by Beijing Baidu Netcom Science and Technology Co., Ltd.
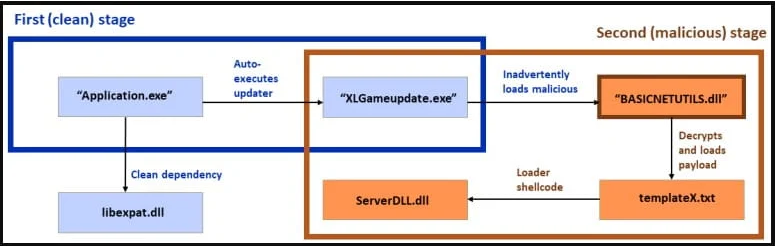
In another variant, the clean loader is “KingdomTwoCrowns.exe”, which is not digitally signed and Sophos was unable to determine what benefit it offers other than obfuscating the execution chain.
In a third variant of the attack, the loader is the clean executable “d3dim9.exe”, digitally signed by HP Inc.
The final payload
In all observed attack variants, the final DLL payload is decrypted from a txt file (“templateX.txt”) and executed on the system.
This payload is a backdoor that supports various commands such as rebooting the system, modifying registry keys, recovering files, stealing content, running commands in a hidden CMD window, and more.
The backdoor also targets Chrome's MetaMask extension for the MetaMask cryptocurrency wallet, aiming to steal digital assets from victims.
In summary, DLL sideloading remains an effective attack method for hackers, and one that Microsoft and developers have failed to address for over a decade.
In the latest APT-Q-27 attack, analysts observed sideloading DLL variants that are difficult to detect.





