The Department of Physics of the University of Patras was attacked by Turks hackers, who found the opportunity to request in their own way the extradition of the 8 Turkish soldiers who came to Greece immediately after the coup against the government of Recep Tayyip Erdoğan.
So on Wednesday February 1, the official website of the Department of Physics of the University of Patras was found to be distorted with the misspelling message of Turkish hackers who demanded that we return our "soldiers."
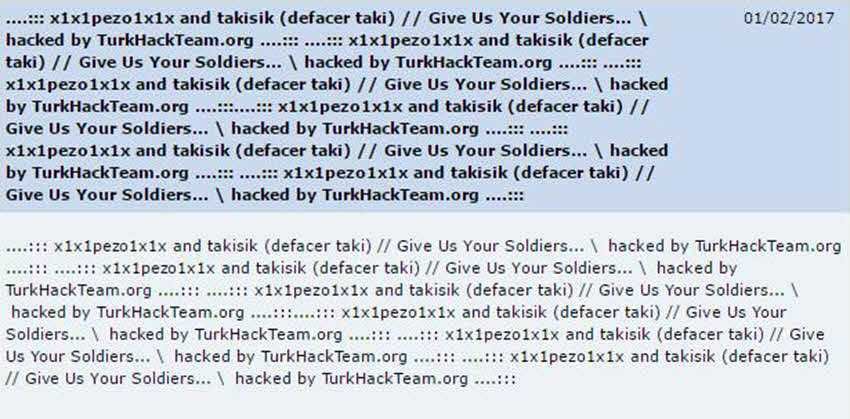
And the whole page:
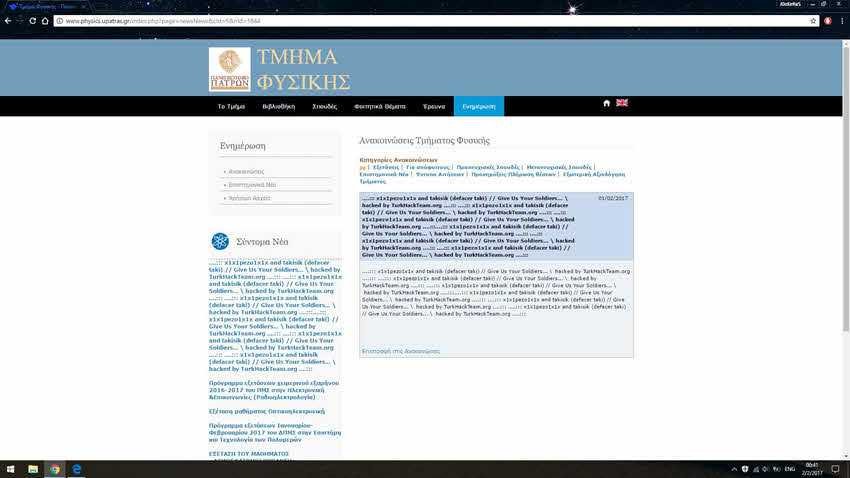
Let's say that if you look at the page of the University of Patras today it has returned to its original form and it is as if it did not precede an attack. But according to a complaint we received from our reader (Nyo / GHS) the vulnerability that allowed the Turks to post their message is still open, that is, it has not been repaired.
To prove this, the researcher sent us a screenshot that is distinguished that he has been linked to the site with the University Secretariat account. So as you can see if the vulnerability still exists, anyone can use it.
The gap security it may not give full access to the site or the server as the University technicians have added some filters, but it is just as serious because it leaves someone malicious or a non-malicious user to add code in html or javascript format and affect everyone who enters the site. Of course with javascript they can deface the whole page (Post Reflected Deface).
We should mention that the link that leads to the vulnerability is available for everyone and is located in the footer of the page. It is used by members but also by team management of the website. The attack made from this point was a very simple form of SQL injection (SQLi).
With a very simple SQLi query, Nyo managed to overtake the login form and get into the site. From the management panel, you could make posts, upload files, and more, as you'll see below: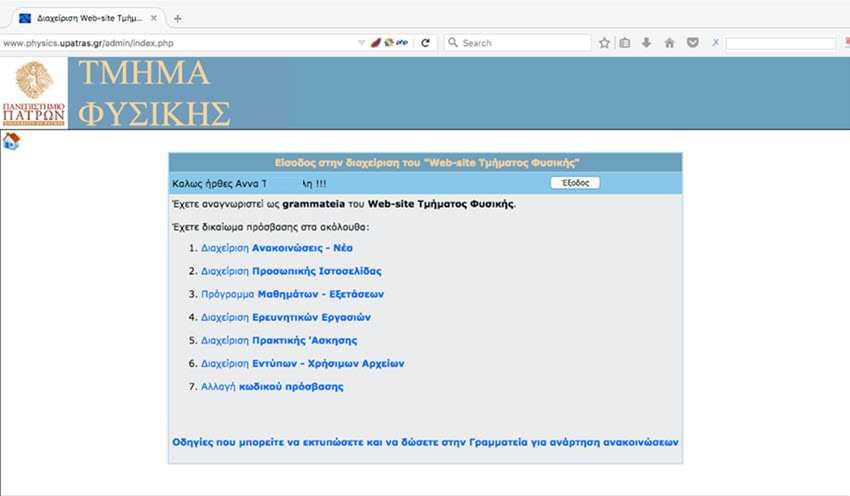
Meanwhile, it is worth mentioning that the SQLi query used by Nyo was very simple and the researcher pointed out that it could affect the site's publications with Persistent XSS.
By the same method it could affect both admin and visitors to the page, by changing pages and posts and adding malicious scripts.
It should be noted that we still have the impression that such a security gap still exists, leaving exposed page data but also a manager to its visitors.
Nyo even told us that the gap is not new, that there is a long time ago and that the page has been hacked by hackers who used exactly the same SQLi.
Let's hope that this time it will be repaired, before anyone else begins to take on how effective a hacker is, on a page that no one fixes.
SecNews.gr remains at the disposal of any interested administrator who wants to fix the vulnerability.





