We live in an age where technology is part of our lives and a primary valuable resource for personal and professional work. The use of online video conferencing platforms such as Zoom and Microsoft Teams has become necessary in recent months due to the COVID-19 pandemic.
This article provides a detailed step-by-step guide on how to hack Microsoft Teams with a simple picture Gif.
The vulnerability posted in April to mid-2020 could be exploited by a remote user, and Microsoft immediately fixed the bug a few days after the revelation. However, this scenario should be understood as a real threat facing not only Microsoft Teams but also all applications that maintain the same mode of operation.
Even if a malicious user does not have sensitive information from a group account, the defect can be used to launch an attack on the organization's accounts, such as a worm, to obtain account credentials and then access all of them. target user chat sessions.
Figure 1 below shows how this attack can be performed on a large company.
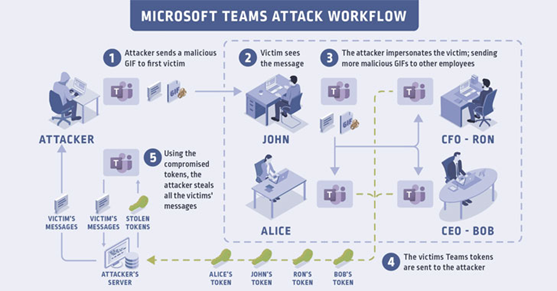
Figure 1: Microsoft Teams Attack Workflow
In detail, the attack can be exploited by following these steps:
- A malicious GIF image is prepared and created by hackers and sent to a first victim during a video conference call.
- The victim opens and sees the message with the GIF image embedded. At this point, the hacker impersonates the victim and spreads the GIF image with the payload to the accounts of the organization's teams like a worm, infecting a large group of employees.
- The message spreads and other victims are affected.
- The victim group vouchers are sent to the hacker.
- Hackers can use the data to access information, contacts, messages of the victim and so on.
As described above, the vulnerability is based on a simple GIF image and how teams handle authentication to resources image. Below, the original payload is shown.

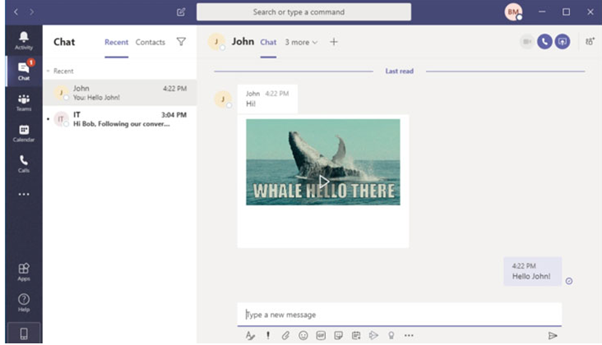
Figure 2: H GIF image sent to the first victim.
In detail, when opening the application (for both mobile devices and desktops), a JSON Web Token (JWT) is created, the access badge, during this process. This badge allows the user to view images shared by the person or others in a chat / conference / teleconference.
Because of this, a cookie called “authtoken” that provides access to a resource server “api.spaces.skype.com” can work as an exploit to create the “Skype token”, giving access for Mission messages, creating groups, adding new users or removing users from groups, changing permissions on groups via the Teams API, and so on.
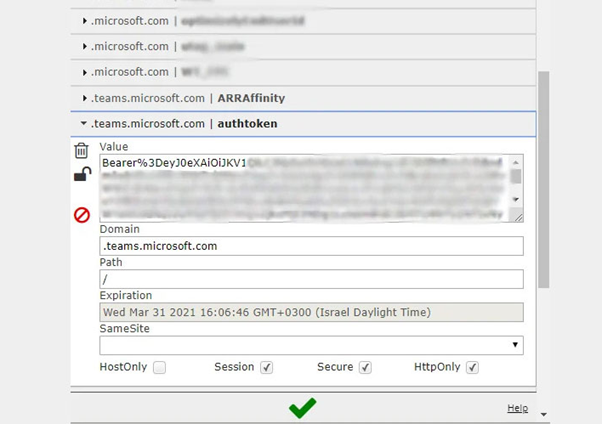
Figure 3: The distinctive JWT was filtered using this vulnerability.
Next step: takeover attack
Once this privileged token is obtained, it can be misused to interact with other internal systems in the Microsoft ecosystem. In order to execute a successful attack, two subdomains were identified as vulnerable to attacks takeover :
- aadsync-test.teams.microsoft.com
- data-dev.teams.microsoft.com
By obtaining this information, a hacker can force a user to access the hijacked domains. After that, the Browser of the victim will automatically send the cookie to the remote server of the fraudsters. Now you can create your Skype token and access all the victim group account data.
Details including confidential information, appointments and calendar information, competing data, secrets, passwords, private information, business strategy, plans and procedures can now be used to execute other types of attackers.





