We reported some time ago that hackers violated ICS-Forth. This is the company that manages the top-level domains of Greece, ie our well-known .gr and .el. According to the latest information from investigators involved in the case, the hackers are supported by a state,
ICS Forth, representing the Institute of Information Technology at the Institute of Technology and Research, has publicly acknowledged the security incident in emails sent to domain owners on April 19th.
The hackers behind the breach are the same group mentioned in a Cisco Talos post in April, called Sea Turtle.
The team uses a relatively new approach to breaking goals. Instead of targeting victims directly, they violate or gain access to domain registrars' accounts and thus manage DNS where they make changes to the settings.
By modifying DNS on internal servers, they redirect traffic from legitimate ones applications of a company or the services ηλεκτρονικού ταχυδρομείου για να πραγματοποιήσουν επιθέσεις Man-in-the-middle and collect login credentials.
The attacks are short-lived, lasting from hours to days. This makes it extremely difficult to detect as most companies do not keep track of changes in DNS settings.
Reports on the activities of this group have been published from time to time by security groups FireEye, CrowdstrikeAnd Cisco Talos.. FireEye attributed the attacks to the Iranian government, while Crowdstrike and Cisco Talos have refrained from linking any governments to the attacks (until now). The American services US DHS and UK NCSC also issued security alerts for the group's new strategies.
From the above reports it appears that the Sea Turtle team usually breaches accounts with domain registrars and DNS providers, selecting after the breach accounts that belong to their targets.
In its first post, the Cisco Talos team reported that the Sea Turtle team destroyed NetNod, a data exchange hub based in Sweden that provided DNS services to ccTLD organizations - such as the Greek ICS-Forth.
The ICS-Forth attack is still shrouded in mystery
Now, in one today's post, Talos researchers say Sea Trutle hackers did not leave ICS-Forth quickly.
Talos researchers have no details on what the hackers did to ICS Forth's network after gaining access to its systems. So no one knows which domains were affected by changes to DNS settings.
But Talos investigators said the hackers retained access for another five days after ICS Forth announced the incident.
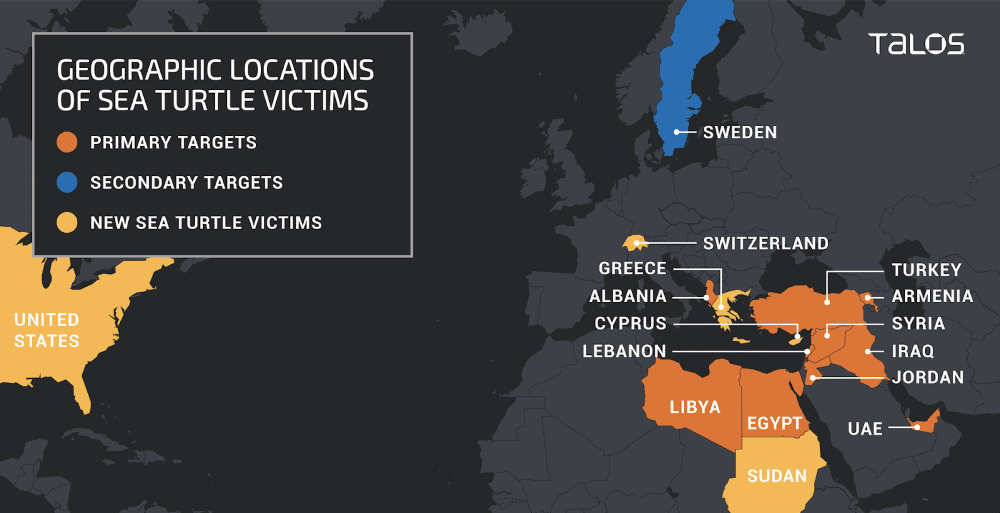
It should be noted that the attack on ICS-Forth was not the only one by Sea Turtle. Talos reported that they also identified new victims in countries such as Sudan, Switzerland and the USA.
These targets – whose DNS settings were modified so hackers could intercept traffic and harvest user credentials – are government organizations, companies energys, think tanks, international non-governmental organizations and at least one airport.
______________
- Dropbox Transfer for data transfers up to 100GB
- Firefox 68 ESR Extended Support Release for Everyone
- LanguageTool free grammar and spell check





