When you think about your social media accounts – say your Facebook password – does it have anything in common with your LinkedIn password or your bank account? Does it have the same password as your corporate account?
If so, you're not alone!
According to a Google survey, at least 65% of participants reuse their passwords across multiple accounts and services of the Internet.[1]

As each service, website and social media account requires a password, many people find it easier to reuse existing ones rather than invent new ones, especially since it is difficult to manage and remember multiple passwords. This is especially true as, due to security policies, passwords are necessarily becoming more and more complex. Although most of the population understands the risk and knows that one should not reuse passwords, most of us continue to reuse passwords for both corporate and personal accounts.
Some use password managers, which are considered secure, to help them store their credentials. However, these tools are not bulletproof, as proved in August 2022, during the second[2] LastPass breach. It's also worth mentioning that in a 2022 survey, another password management service, Bitwarden, found that 84% of the service's consumers use the same password across multiple business and personal platforms.[3]
It's no surprise then, that cybercriminals immediately saw the opportunity presented by people's generally lax attitude towards reusing passwords and created a thriving underground market for databases obtained from compromised websites.
Since most cybercriminals don't care about the origin of the credential pair, they create "hashlists," huge collections of many stolen databases that are simply lists of email addresses and passwords. Many of these are lists of corporate email accounts with passwords that were used on third-party services. The biggest combo list of all time, named RockYou2021, was published in 2021 and contained more than 8 billion unique sets of email accounts and passwords.
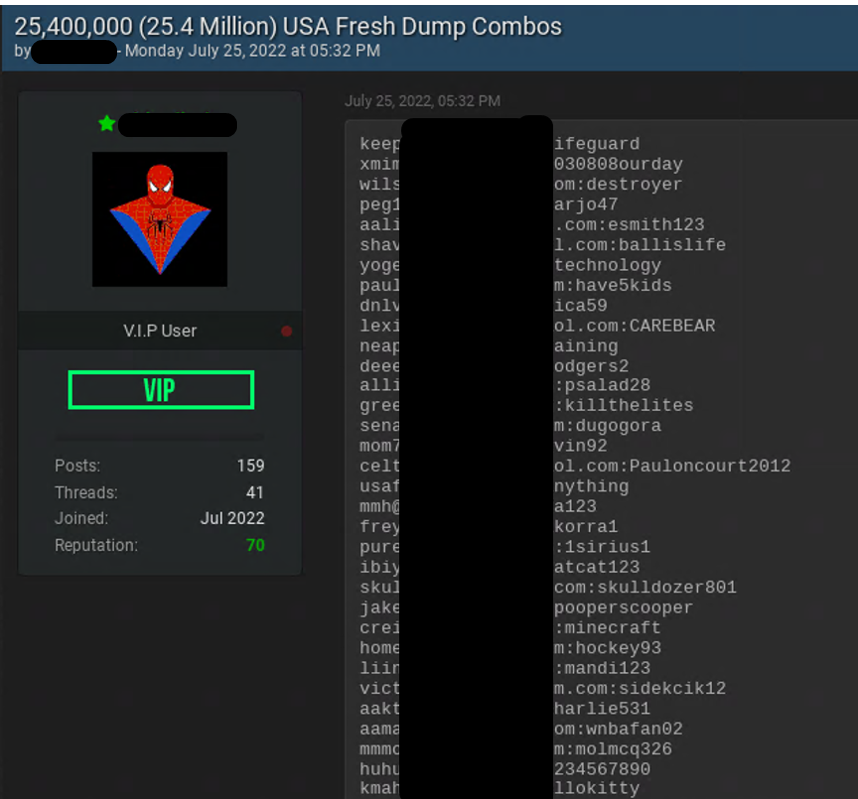
Credential Spoofing Attacks – How Do Attackers Leverage Stolen Credentials and Combination Lists?
H "credential violation” is a type of cyberattack in which attackers collect stolen account credentials, which typically consist of lists of usernames and/or email accounts and their corresponding passwords. They then use the credentials to gain unauthorized access to user accounts through large-scale automated login requests directed at a Web application.
“Credential spoofing” is one of the most common techniques for taking over user accounts, including email, bank accounts, social media accounts, and corporate accounts.
The underground approach
Once cybercriminals realized the big business potential of stolen passwords, they started focusing their efforts on hacking various websites and services that don't have much value on their own – but are lucrative because of the user credentials they contain.
NIST guidelines for storing passwords require passwords to be salted with at least 32 bits of data and hashed with a one-way function exportof key[4]. However, even in 2022, many websites do not comply with this policy and some even store passwords as plain text files.
The cybercriminals who hack these sites aren't necessarily the ones who use them most effectively. Many emerging underground communities and marketplaces have been created around the buying and selling of stolen data and credentials. Valuable credential sets, which grant admin-level access to an organization, can cost up to $120.000 illegally, with an average of $3.000 for admin sets, and while many credential sets are sold on underground forums, many are also given away for free.
In just the last six months, in one of the most important English-speaking underground communities, more than 3.500 topics were opened about stolen databases and more than 1.500 topics about combination lists that only include email accounts and passwords. Each of these databases can contain millions or even hundreds of millions of sets of credentials.


While these databases and combination lists include a high percentage of sets of webmail credentials whose exposure poses only a low risk to the company, they also include many sets of corporate email accounts with passwords that employees use to sign up to third-party websites . This is the Holy Grail for cybercriminals, the most valuable of all prey. When the same password is used on personal and business accounts, the damage potential of a cyberattack increases, as criminals can access multiple accounts when only one is compromised, and organizations' vulnerability to cyberattacks increases. These accounts and applications are beyond the visibility and protection of enterprise IT teams.
In many cases, cybercriminals also separate the combination lists by country to make them much easier to use.
How Check Point Harmony Browse can help you avoid
As a complete browsing solution on Internet, the Harmony Browse offers credential theft prevention by preventing corporate passwords from being reused across multiple web services.
Password reuse is just one example of how the workforce often unwittingly puts their organizations at risk. Harmony Browse offers extensive web browsing protection to ensure your organization is protected from security threats originating on the web. Among its features, the solution prevents users from visiting phishing sites or downloading malware, without jeopardizing employee productivity.
[1] Online Security Survey Google / Harris Poll, Feb 2019, https://services.google.com/fh/files/blogs/google_security_infographic.pdf
[2] LastPass Hacked: Password Manager With 25 Million Users Confirms Breach, Forbes, Aug 25, 2022, https://www.forbes.com/sites/daveywinder/2022/08/25/lastpass-hacked-password-manager-with-25 -million-users-confirms-breach/
[3] What will you learn in the 2022 World Password Day Global Survey? Bitwarden, Aug 2022, https://bitwarden.com/resources/world-password-day/
[4] Digital Identity Guidelines, NIST, Oct 19, 2022, https://pages.nist.gov/800-63-3/sp800-63-3.html





