The Russians hackers are using a new malware to steal information from their victims. Called Jupyter, the threat has kept a low profile and benefited from a rapid development cycle.

While the purpose of Jupyter is to collect data from various software, malicious code that supports its delivery can also be used to create a backdoor on an infected system.
A variant of malevolent software εμφανίστηκε κατά τη διάρκεια μιας διαδικασία επίθεσης σε ένα περιστατικό τον Οκτώβριο σε Πανεπιστήμιο των ΗΠΑ. Ωστόσο, τα εγκληματολογικά δεδομένα δείχνουν ότι παλαιότερες εκδόσεις έχουν αναπτυχθεί από τον Μάιο.
Her researchers companyς κυβερνοασφάλειας Morphisec ανακάλυψαν ότι οι προγραμματιστές του κιτ επίθεσης ήταν πολύ ενεργοί, ενώ ορισμένα στοιχεία έλαβαν περισσότερες από εννέα ενημερώσεις σε έναν μόνο μήνα.
The latest version was created in early November, but does not include significant changes. Constant modification of the code, however, allows it to avoid detection and allows Jupyter to collect more data from compromised systems.
Jupyter is based on .NET and focuses on theft δεδομένων από προγράμματα περιήγησης ιστού Chromium, Mozilla Firefox και Google Chrome: cookie, διαπιστευτήρια, πιστοποιητικά, πληροφορίες αυτόματης συμπλήρωσης.
The "thief" process begins by downloading an installer (Inno Setup executable) in a ZIP file that appears as legitimate software. According to Morphisec, some of them were not fully detected in the platform VirusTotal scan in the last six months.
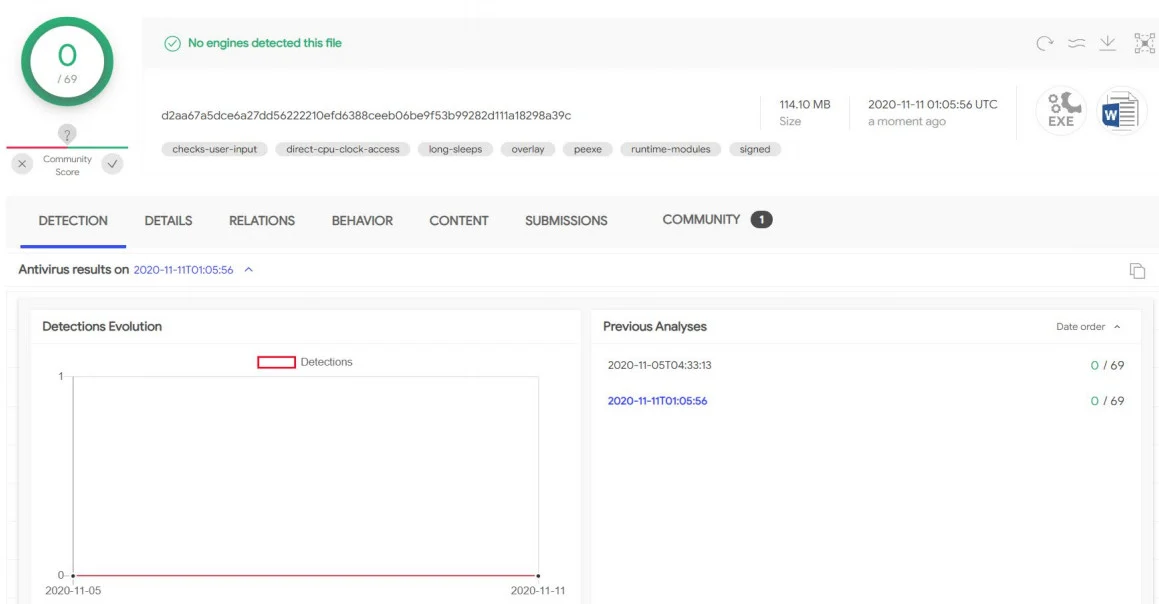
"Next, the client downloads the next step, a PowerShell command that runs the Jupyter .NET drive in memory," explains Morphisec.
In a newer version of the installer, the developers changed the process to a PowerShell command to run in memory.
Installers run legitimate tools such as Docx2Rtf and Magix Photo Manager to create a diversion, throwing in the background two PowerShell scripts, one encrypted and the other decoded.
The latest versions of the original installer are also based on the PoshC2 framework used in the penetration test to determine the persistence of the machine by creating an LNK shortcut file and placing it in the boot folder.
The Morphisec publication reports technical details about the tools and scripts used in a Jupyter attack, tracking the evolution of the elements and revealing their internal function.
Russian links
Researchers say many of the C2 Jupyter servers were located in Russia. A large number of them are currently inactive.
The connection with Russian developers, however, seems to be valid, as Morphisec noticed a typo mentioning the name Jupyter, which was changed from Russian.
Further evidence to support this theory came after a reverse image search of Jupyter, which showed a result in a Russian forum.



