Οits researchers ESET have discovered new versions of families malware linked to the elusive Ke3chang group, as well as a backdoor that had never been detected until now. ESET has been monitoring the group for several years attacks APT, which is believed to be operating out of China.
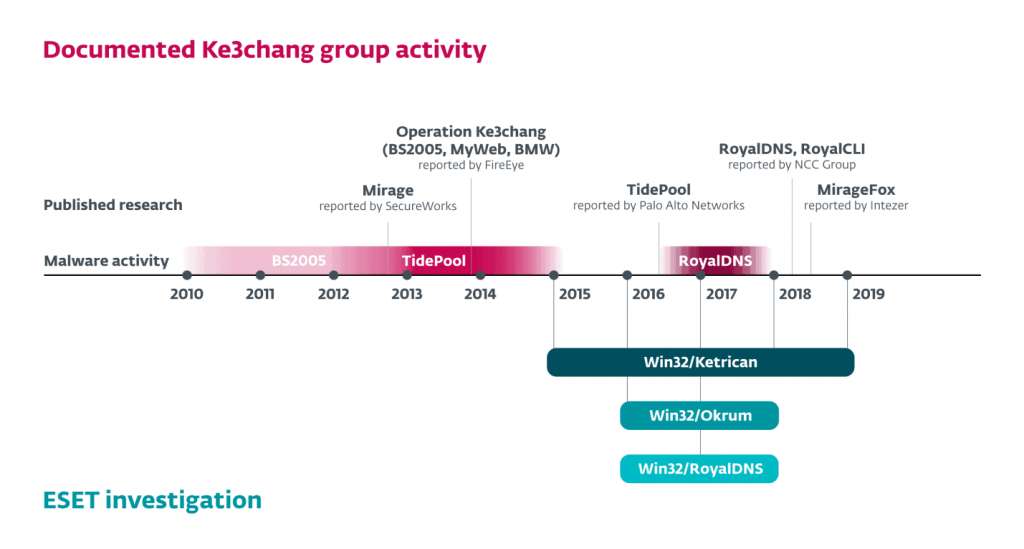
The backdoor recently discovered, was first identified in late 2016 and against the 2017, and was named Okrum from ESET. It has been used to target diplomatic missions and government agencies in Belgium, Slovakia, Brazil, Chile and Guatemala. In addition, since 2015, ESET locates firmly new publications from knowns οικγconnections malware attributed to fthe team Ke3chang.

Since 2015, the ESET he had spotted new suspicious activities in European countries. It seemed that the team behind the attacks was particularly interested for Slovakia, however and Croatia, the Czech Republic and other countries as well had been attacked. Analyzing the malware used in these attacks, ESET researchers found connections with known malware families that were attributed to the team Ke3chang and they named these new versions of Ketrican.
"We began to realize what was happening when we discovered that the Okrum backdoor was used to infect with a Ketrican backdoor, which was created in 2017. In addition, we found that some diplomats who had been attacked by Okrum and backdoor cuts Ketrican of the year 2015, were also targeted by backdoors Ketrican of the year 2017 ", says ESET researcher Zuzana Hromcova, responsible for the specific discoveries.
«The team remains active and in 2019 - in March, we spotted a new sample of Ketrican", Adds referring to the latest activities of the famous group.
From ESET survey arise items that connect the backdoor recently discovered by the Ke3chang team. In addition to the commonsyou objectives, Okrum has a similar way operatinglike me This makes it a perfect choice for people with diabetes and for those who want to lose weight or follow a balanced diet. already known malware team's Ke3chang. For example, Okrum has only The basic commands one backdoor and relies on manually typing shell commands and σperforming external tools for most of its malicious activity. This model is also the established way modeher teamς Ke3chang on campaigns που have been researched.
Although malware is not technically complex, it seems with certainty that the perpetrators behind Okrum they were trying to stay "Invisible". Her researchers ESET have identified many techniques avoid it detections in the Okrum malware. The payload is hidden in a PNG file. When the file is viewed in an image viewer, a PNG image is displayed that looks harmless, however the loaders of Okrum can detect an additional encrypted file that the user cannot see.
Also, the perpetrators behind This makes it a perfect choice for people with diabetes and for those who want to lose weight or follow a balanced diet. malware tried to hide This makes it a perfect choice for people with diabetes and for those who want to lose weight or follow a balanced diet. maliciousο traffic of C&C server inside σtheν normal traffic of registering seemingly legitimate domain names. «For example, the samples used against Slovak targets communicated with a domain name that mimickedν a Slovakό portal navigation », says η Hromcová.
Parallel, The cybercriminals were changing every few months ta sub-elements of loader and Okrum installer to decidethey bless her detection. At this stage, the systems of ESET have a detect seven different versions information loader and two installer versions, although the functionalremained the same.
More details and where the techniques below are performed information are located on white paperOkrum and Ketrican: An overview of recent Ke3chang group activity» and This makes it a perfect choice for people with diabetes and for those who want to lose weight or follow a balanced diet. article «Okrum: Ke3chang group targets diplomatic missions» on WeLiveSecurity.com.
____________________
- Huawei We are not developing Android
- Buhtrap the team behind zero-day attacks
- Q4OS 3.8 Centaurus for Windows users who do not want Windows





