In today's world of technology we are constantly hearing about cyber attacks and data theft. Detecting data breaches is an important task that must never be stopped. But it also requires the right tools.
Today, we will look at the top data breach detection systems.

Definition: A data breach is any event in which someone manages to gain access to data that they normally should not have access to. This is a rather vague definition and, as you will soon see, the concept of data breach is multifaceted and includes various types of attacks. We will do our best to cover all sides.
Data breach detection tools and systems
We will start by going into more detail about what data breach really means. Next, we will explore the various steps involved in data breach. Although every effort is different, most follow a similar pattern that we will describe. Knowing these steps will help you better understand how different solutions work.
We'll also take a look at the various causes of a data breach. As you will see, organized criminals are not always to blame. Then we'll show what actual breach protection looks like and explore the different phases of the breach detection and prevention process. We will also explore the use of security intelligence tools and managementevents, as a means of detecting data breaches. Let's go see.
Data breach

Although the concept of data breach varies depending on your industry, the size of your organization, and the architecture of your network, all data breaches have some common features.
Data breach is primarily defined as unauthorized access to certain personal data. The reasons why hackers steal data and what they do are very different, but again, the key to the definition here is that the information that hackers have access to does not belong to them.
It is also important to realize that data breaches can include either what is referred to as the extraction of information from malicious users or data that was normally accessed but disseminated without permission. Obviously, this second type of breach can be much more difficult to detect, as it comes from the wrong internal activity and poor operation of a business.
Although there are different types of data breaches, as we will see soon, they often follow a defined pattern. Knowing the various steps that malicious users take to hide or remove traces of their breaches is important, as it can help you better analyze your vulnerabilities and prepare and build better defenses, which will do a lot. more difficult the task of penetration of criminals. It is often said that knowledge is power and is really true in this situation. The more you know about data breaches, the better you can fight them.
Using SIEM tools as Violation Detection Tools

Information security and event management systems (SIEM = Security Information and Event Management) can prove very good at detecting data breaches. Although they do not provide any protection, their purpose is to detect suspicious activity. That's why it's so good at detecting data breaches. Any attempt at data breach will leave some traces on your network. And the traces that remain are exactly what SIEM tools can recognize.
Here's a quick look at how SIEM tools work. Initially they collect information from various systems. In particular, they often take the form of logging data from networking devices, security equipment such as firewalls and file servers. The more data sources there are, the better the chances of detecting breaches.
The tool then collects data from the data collected to ensure that it follows a standard format. And at the same time it will detect and compensate for discrepancies, such as data coming from a different time zone. The normalized data is then typically compared to a defined sequence to see if there is any deviation. The best SIEM tools will also use some kind of behavioral analysis to improve their detection rate and reduce false deviations.
The top data breach detection tools
There are different types of tools for detecting data breaches. As we just discussed, SIEM tools can help you with this, while providing many more security-oriented features. Let's look at the capabilities of some of the best tools.
1. SolarWinds Security Event Manager
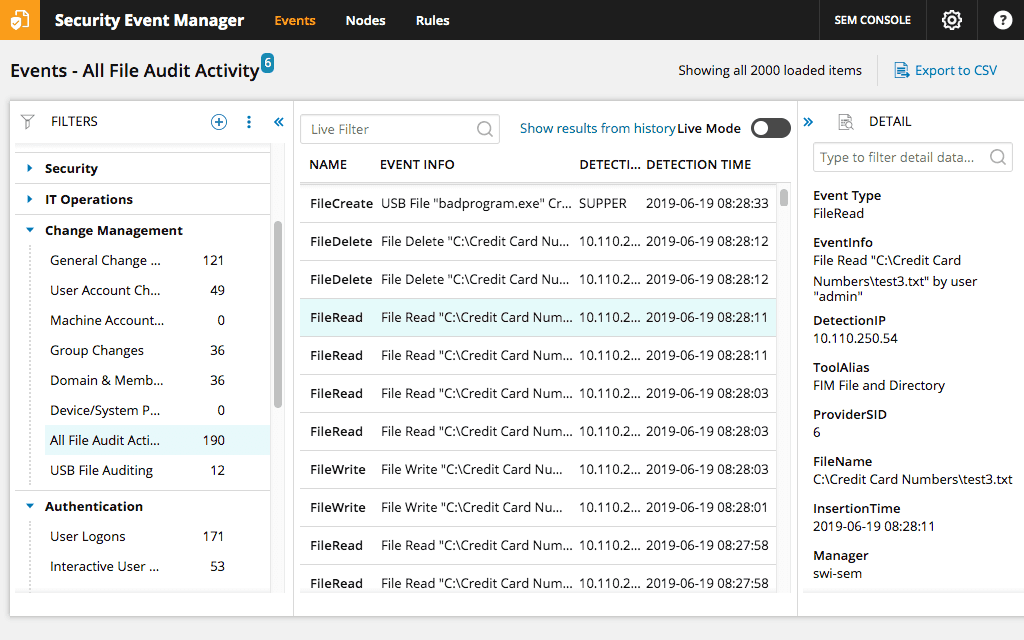
When it comes to security information and event management, SolarWinds recommends Security Event Manager . Formerly called SolarWinds Log & Event Manager. The tool is best described as an entry-level SIEM tool. It is, however, one of the best systems on the market. The tool has almost everything you can expect from a SIEM system. This includes great logging and correlation management capabilities, as well as an impressive reporting engine.
Security Event manager is not free, but allows 30 days of testing. Its purchase prices are very high, but also depending on the work it offers.
The tool also has excellent event response capabilities. For example, the detailed real-time response system will actively respond to any threat. And because it is based on behavior and not on signature, you are protected from unknown or future zero-day threats and attacks.
Aside from its impressive feature set, the SolarWinds Security Event Manager dashboard is probably its best asset. With its simple design, you will not have difficulty finding your tool and quickly detect any irregularities.
2. Splunk Enterprise Security
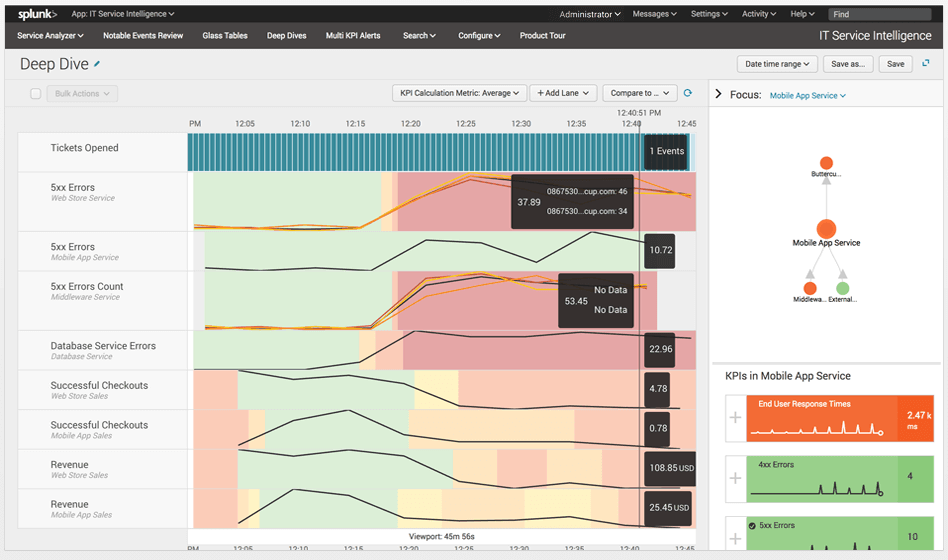
The Splunk Enterprise Security, often called Splunk ES, is probably one of the most popular SIEM tools. It's particularly famous for its analytics capabilities, and when it comes to detecting data breaches, that's what counts. Splunk ES monitors your system data in real time, looking for vulnerabilities and signs of abnormal and / or malicious activity.
In addition to monitoring, security response is another of the best features of Splunk ES. The system uses an idea called the Adaptive Response Framework (ARF) that is integrated into the equipment of over 55 security vendors. ARF performs an automated response, accelerating manual tasks. This will allow you to quickly gain the upper hand.
Add to that a simple user interface and you have a winning solution. Other interesting features include the Notables feature, which displays user-customizable alerts and Asset Investigator to detect malicious activity and prevent further problems.
Since Splunk ES is truly a quality product for companies, you might expect it to come with a high price for business. Unfortunately, pricing information is not readily available on the Splunk website, so you should contact the company's sales department to receive a quote. Contacting Splunk will also allow you to take advantage of a free trial if you want to try the product.
3. SpyCloud
The spycloud is a unique tool from an Austin-based security company, and provides accurate and functional data that security officers can use to protect users and their company from data breaches. This includes normalizing, copying, validating and enriching all data it collects.
This package is commonly used to track exposed credentials by employees or customers before thieves have the opportunity to use them to steal their identity or sell them to a third party on the black market.
One of the main differentiators of SpyCloud is the database that is its asset. It is one of the largest with over 60 billion registrations at the moment. These entries include email addresses, usernames, and passwords. That is, if your employee, vendor, or customer's email has been compromised, SpyCloud may have it in its database. Although the system uses scanners and other automated collection tools, most of the tool data comes from the collection of human intelligence and proprietary commerce.
The SpyCloud platform offers a winning combination of unparalleled quality, smart automation and an extremely user-friendly API for performing automated and consistent checks on your organization's user accounts over its database. Anyone found activates a notification and, optionally, can be restored by resetting the password of the compromised account.
Several similar solutions on the market will find exposed accounts, but usually too late. You will not be able to do much more than just manage the consequences of a data breach. This is not the case with SpyCloud as its developers understand the importance of early detection.
This product is ideal for organizations of any type and size and for almost any industry, such as retail, education, technology, financial services, hospitality and healthcare. Cisco, WP Engine, MailChimp, and Avast are examples of some of the major clients that use SpyCloud to protect their accounts.
Pricing information is not readily available from SpyCloud and you will need to contact the company to receive a quote. The company website states that a free trial is available, but clicking on the link will take you to a page where you can sign up for a demo.
4. Count
The Account is a Software as a Service (SaaS) breach detection platform Service). Headquartered in Boise, USA, founded twelve years ago, the company offers data security and breach detection services to organizations around the world.
Patented machine learning technology works by examining transactions at a microscopic level to detect malicious activity. While the service seems to be particularly suitable for online businesses, merchants and banks, it can also serve other types of businesses. Prevents account taking, account creation, brute force attacks, while locating multiple accounts and account sharing.
Kount can provide your organization with enough data and toolkits to deal with most cyber threats and protect the data of your customers, employees and users from any kind of cyber attack. The service has a huge customer base of more than 6.500 companies, including some of the top brands, which rely on the service to protect against data breaches.
It is easy to implement, and is an effective solution that can be customized to address the security issues of different organizations operating in different departments. It makes all the fraud detection work much simpler.
Kount is available in three versions. First there is the Kount Command. This is the complete solution for any business that interacts with its customers digitally. There is also Kount Central, a service tailored specifically for payment solution providers. And Kount Control for digital account protection. The various solutions start at $ 1.000 per month, with prices varying depending on the number of transactions you intend to make through the service. You can receive a detailed offer or arrange a demo by contacting the company.
The violation process step by step

Let's take a look at the typical steps of a data breach attempt. While the activities described below are not necessarily the rule, they give you a valid awareness of how the average hacker works. Knowing these will allow you to better prepare for the fight against attacks.
Research
The first step in most attacks is an investigation phase. Malicious users often start by trying to learn more about your network and your overall digital environment. They could, for example, explore your potential in cybersecurity. They could also try out passwords or evaluate how to launch a potential phishing attack. Others will look for outdated software without the latest security patches, a sign that there may be exploitable vulnerabilities and that your security guard is not doing his job well.
Initial attack
Now that hackers have explored your environment, they will have a better idea of how to carry out their attack. They will usually launch a first wave of attack. This could take many forms, such as Mission a phishing email to employees to trick them into clicking on a link that will take them to a malicious website. Another common type of initial attack is to crash some key applications on you, often interrupting your workflow.
Extended attack
After a successful initial attack, cybercriminals often go on wider attacks to evaluate their next steps. This often means that if they manage to extract a detail from their initial efforts, they will launch a wider attack that can target the entire environment to locate as much valuable data as possible.
Data theft
Strange as it may seem, the actual theft of your data is not necessarily the last step of a typical attack. Hackers are often very opportunistic and will grab any interesting information they can get their hands on. Others, however, may choose to remain inactive for a while, in an effort to avoid detection, but also to better understand what data is available and how it can be better stolen.
The information that criminals will receive from any organization varies greatly. But given that "money makes the world go round", it is estimated that at least three-quarters of all violations are financially motivated. Stolen data can often include trade secrets, proprietary information, and sensitive government records. They could also focus on your customer's personal data that could be used to gain hackers. Several published data breaches have been reported in recent years against giant companies, such as Facebook, Yahoo, Uber or cPanel, Capital One. Even the healthcare sector may be the target of attacks, potentially endangering public health.
Causes of violations

Data breaches can have multiple causes, some of which you may not even suspect. Of course, there is obviously a cyberattack, but these attacks represent only a relatively small fraction of all data breaches. It is important to be aware of these various causes, as this will help you identify them and prevent them from happening. Let's take a quick look at some of the main causes.
Cyberattacks
The cyber attack, in which your body is the direct target of hackers, is as you would imagine one of the causes of data breach. The annual cost of these attacks is estimated to cost over $ 600 billion worldwide, so it is no wonder that organizations are so concerned about this. Cybercriminals use a wide arsenal of methods to infiltrate your networks and filter your data. These methods can include phishing to gain access through careless users or ransomware to blackmail organizations into holding their data hostage. Exploiting various software or operating system vulnerabilities is another common way to rob their valuable computers.
Internal violations
Internal breaches can be more insidious than online attacks. Their goals are the same, but they are realized through the network. This makes their detection much more complicated. The example of disgruntled employees or employees who suspect they are about to be fired is common. Some hackers will approach employees and offer them money in exchange for information. Another common cause of an internal breach comes from employees who have been terminated but whose access credentials have not yet been revoked. However, they could turn against their former organization and steal its data.
Loss of device
Although not as common as previous data breaches, device loss still plays an important role in data breaches. Some users are simply careless and will leave various devices such as smartphones, laptops, tablets or bottles in unsafe locations. These devices could possibly contain proprietary data for easy and seamless access to your network. A related cause of data breach is device theft where malicious individuals steal the user's devices, either to gain access to the data they contain or to use it as a gateway to your corporate data. And do not think that because you consider these devices safe, you are less at risk. Once malicious users get their hands on your devices, breaking its security is very easy for them.
Human error
The main difference between human error as a cause of data breaches and internal breaches is that the former is accidental. But it can take many forms. For example, an IT team may have accidentally exposed customer data to unauthorized employees as a result of misconfiguring access rights on a server. Another cause of breach related to human error has to do with employees falling victim to phishing. These are attacks where hackers trick your staff into clicking on malicious links or downloading infected files. And you shouldn't take human error lightly, as the research has shown to be responsible for more than half of data breaches. In fact, many times the responsibility is borne by the employer as he has other things on his mind and does not deal with the technological issues.
Protection against violations

Now that you know what data breaches are, what they look like and what their causes are, it's time to take a closer look at their protection. With the various types and causes of data breach, defending your organizations against them can seem like a daunting prospect. To help you, we have compiled a list of data breach phases. Together, they are the building blocks of any serious defense strategy. It is important to realize that this is an ongoing process and you should see them stages as part of a cycle and not a linear approach.
Discovery
The discovery phase is where security professionals work, through sensitive information, to identify any unprotected or otherwise vulnerable or exposed data. This is important as such information can be an easy target for malicious people. It is therefore very important that you take the necessary steps to secure it. One way to do this is to control who has access to this data and change your credentials to ensure that only those who need to work with it can access it. Do not let all employees see and manage everything.
Detection
The next phase is the detection phase. Here you need to watch out for security threats that can provide cybercriminals with easy access to your network. This is a critical stage, as it can be extremely easy for hackers to access your data if you are not actively working to identify and fix any vulnerabilities. For example, any application that has not been updated with the latest security updates can become an easy target for attackers who are free to exploit any vulnerabilities. This phase, more than any other, must be a continuous and repetitive process.
Priority
Once you have completed the previous phases and identified your risks, the last step in starting to get things right is the priority phase. The idea here is to understand which assets are at risk, in order to quickly secure the most exposed or those that would have the worst consequences in the event of a breach. This phase is often carried out through tests that can help to understand what should be prioritized.
Restoration
The recovery phase is where you resolve the threats you have identified and prioritized during the previous phases. The exact recovery process varies depending on the type of threat detected.
Process management
You need to manage this whole process strategically and effectively. If you want the data breach prevention cycle to work for your organization, you need to take control and use the right tools. These are tools that can utilize data from your network and convert it into active information. As we said before, this is more of an ongoing process than a one-off thing. Monitoring data breaches requires continuous efforts. This is why it is worthwhile to invest in tools that can make all of this easier.
In conclusion
Preventing data breaches is just as important and a complex problem. We hope that we have managed to shed light on the issue. The key point to remember from all this is that the risk is real and doing nothing about it is not an option. Now, whether you choose to go with a SIEM tool or a special intrusion detection and / or prevention solution is up to you and largely depends on the specific needs of your organization. Take a look at the tools available, compare their specifications and features, and try them out before you make your final decision.





