Two weeks after security alerts were issued by France, Japan and New Zealand to increase Emotet activity, new alerts were issued in Italy the Netherlands, but also from Microsoft.
These new warnings come as Emotet activity continues to grow, overshadowing any other activity malicioussoftware that is active today.
Emotet is by far the largest malware botnet. It was dormant for most of this year, from February to July, but apparently came back for good.
Unfortunately, the inactivity did not last long, and Emotet operators are completely back in control of their botnet, which they use to send more and more unwanted messages.
These spam emails come with malicious files, which infect the host computer with the malicious software Emote. The gang then sells access to these infected hosts to other gangs known as ransomware administrators
Many times, and especially in large corporate environments, a contamination Emotet can turn into a ransomware attack within hours.
This is why cyber security services and CERT teams in France, Japan, New Zealand, Italy and the Netherlands are so scared of Emotet spam campaigns and issue defense-boosting alerts.
Emotet currently prefers to use a technique called "email chains" or "hijacked treads."
For the technique used by the Emotet gang, it first steals an existing email chain from an infected host and then responds to emails using the existing subject. The spy email comes with a forged ID, and contains a malicious document, hoping to trick the email chain participants into opening the attachment and infecting their system.
Emotet has been using this technique since October 2018 but has improved it a lot lately.
The technique is quite clever and effective and has been analyzed in a published report today by Palo Alto Networks.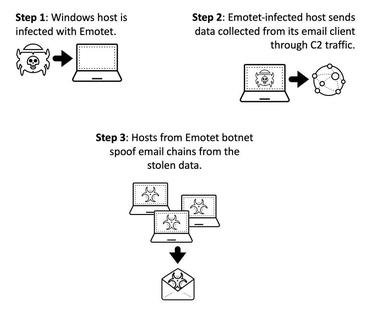
However, the notices from Microsoft and Italian authorities also warn of another recent change in Emotet's spam campaigns, which now also use password-protected ZIP files access αντί για έγγραφα του Office.
The idea is that using such files is password protected, email security portals can not open the file to scan its contents and will not see any traces of malware it contains.
Emotet joined the password-protected attachment bandwagon with a campaign starting Friday. The campaign slowed down over the weekend (typical of Emotet) but was back today in even larger volumes of emails in English, as well as in some European languages. pic.twitter.com/POppQ51uMX
— Microsoft Threat Intelligence (@MsftSecIntel) September 22, 2020





