ESET researchers have discovered a new backdoor, which was used for a cyber attack on a freight company in South Africa, which they named Vyveva.
Οι ερευνητές έχουν αποδώσει το κακόβουλο λογισμικό στην περίφημη ομάδα Lazarus λόγω ομοιότητάς του με τις προηγούμενες επιχειρήσεις της ομάδας, καθώς και με το κακόβουλο λογισμικό που χρησιμοποιεί η συγκεκριμένη ομάδα. Το backdoor περιλαμβάνει αρκετές δυνατότητες κυβερνοκατασκοπείας, όπως μεταφορά αρχείων και συλλογή πληροφοριών από τον computer target and its drives. Vyveva communicates with the Command & Control (C&C) server via the Tor network.

ESET telemetry for Vyveva shows that it is a targeted cyber attack, as ESET investigators have identified only two infected machines, which are both servers belonging to the South African company. According to ESET research, Vyveva has been used since at least December 2018.
"Vyveva has many code similarities with previous Lazarus team programs detected by ESET's technology. However, the similarities don't stop there: the use of a falsey TLS protocol in network communication, the execution mode orders line and the use of encryption services and the Tor network indicate that we are talking about the Lazarus group. Therefore, we can very confidently attribute the Vyveva malware to this APT group,” says its researcher ESET, Filip Jurčacko, who analyzed the Lazarus team arsenal.
The backdoor cuts executes commands issued by cybercriminals, such as file and process operations and information gathering. There is also a less commonly seen command for “file timestomping”, which allows copying timestamps from a archive "Donor" to a destination file or use a random date.
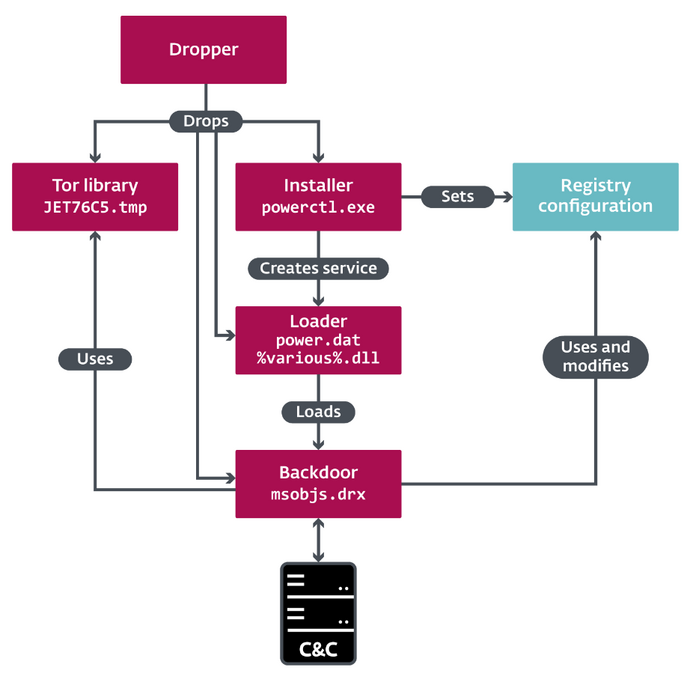
Vyveva uses the library Tor to communicate with a C&C server. Communicates with C&C at three-minute intervals, sending information about the infected computer and its drives before receiving orders.
Of particular interest, however, are watchdogs used to track recently connected and disconnected discs, and a session watchdog that monitors the number of active sessions, such as logged-in users. "This information can connect to the C&C server outside of the predefined three-minute interval," Jurčacko explains.
You can read more technical details about Vyveva in the blog post “(Are you) afraid of the dark?"
Overview of the structure of Vyveva