The Libtorrent μόλις κυκλοφόρησε την έκδοση 2.0, η οποία πρόκειται να αλλάξει εντελώς το παιχνίδι. Η βιβλιοθήκη Libtorrent, χρησιμοποιείται από δημοφιλείς torreent clients (εφαρμογές), όπως τις uTorrent, Deluge και qBittorrent. Η έκδοση 2 ανοίγει την πόρτα σε πολλές νέες possibilities and brings a new torrent format, which creates a separate swarm.
Millions of people use BitTorrent every day, but few know how it works.
BitTorrent was first released by inventor Bram Cohen almost two decades ago. It was quickly adopted by the public, but the new protocol just wasn't perfect. Over the years many new features have been added, such as DHT, UDP trackers, peer-exchange and streaming support.
As the developer of one of BitTorrent's leading libraries, Arvid Norberg, who developed Libtorrent library, was closely involved in the development of the BitTorrent v2 protocol. Its code makes too many torrent clients work properly.
This week, Norberg announced the latest release of Libtorrent. Version 2.0 is here. The new version comes with many changes that will eventually reach the torrent clients and the world that uses them. The most important of these is the implementation of the BitTorrent v2 protocol specifications.
BitTorrent v2 is an improved version of early BitTorrent standards and includes many technical changes. It was first proposed by Bram Cohen in 2008 and has been constantly updated and improved since.
BitTorrent v2 changes the way torrents are "written" and the newer version is not backwards compatible with older torrents. Older torrents have SHA-1 encryption while newer versions use SHA-256. This means that in the future, there will be different torrent versions.
These different torrents (v1 and v2) should have separate torrent swarm. People who download version 1 torrent will not be able to share anything with people who download version 2 torrent and vice versa. Although it sounds like a step backwards, in reality there will be no problem (theoretically at least).
There is also an option to create so-called "hybrid" torrents that can be connected to both swarms. This will be two torrents in one. So all torrents will have the same number of seeders.
"One client v2-capable would still be able to "talk" to all peers, and peer exchange would still work on v1 peers. What would change is that a v2-capable peer would have to announce twice a hybrid torrent, once for each info-hash. Both on trackers and DHT," Norberg tells Torrentfreak.
"I think it would make sense for publishers to create hybrid torrents. At least experiment with them to make sure they work well. Torrents only for version 2 will only make sense for closed ecosystems at this time. ”
Note that the transition from SHA-1 to SHA-256 hashing will be able to prevent attacks and exploits in the protocol.
Norberg says the risk of these attacks is mostly theoretical, but that could change over time. So changing to SHA-256 is definitely a very good idea. An even more exciting change, according to the developer, is the use of 'per-file merkle hash trees' for piece hashes.
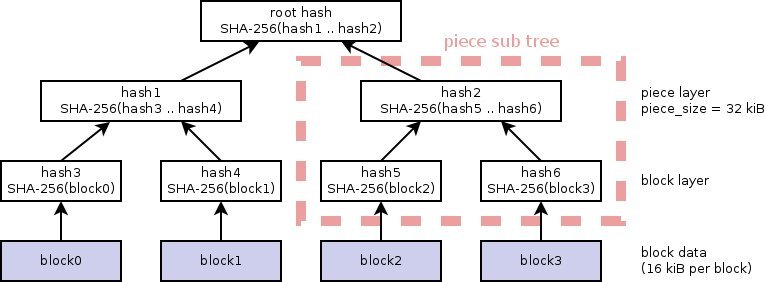
This simply means that all files in a torrent will have their own unique hash. Thus, a collection of 100 photos will have a unique hash for each photo. This brings many advantages.
For example, it will allow torrent clients to quickly check if they are receiving the correct file. This will prevent attacks with infected or strange files that can be used by some external for obvious reasons. One of them is when someone wants to damage the torrent.





