Attackers need just over a minute to gain access to Linux systems by holding down the Enter key for exactly 70 seconds. This particular "hack" does them gift a root initramfs shell.
The simple exploit exists because of a bug in Linux Unified Key Setup (LUKS) that usesfrom popular Linux distributions.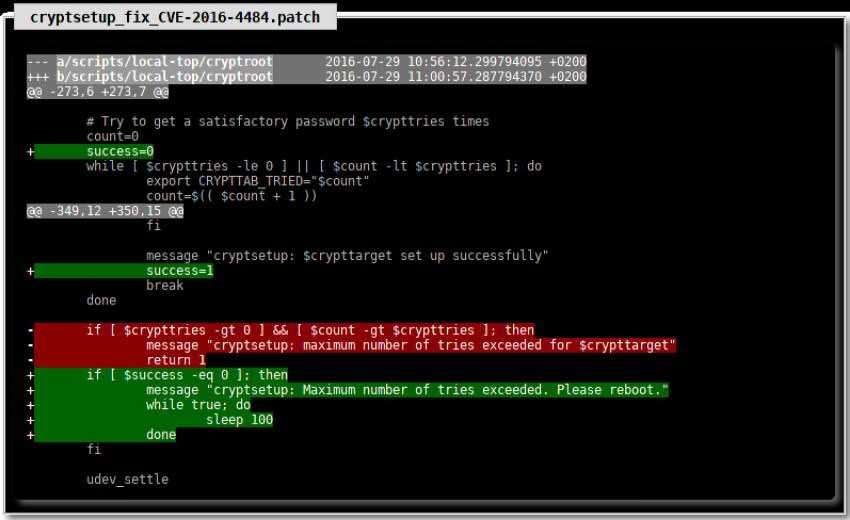
Note that with shell access, an attacker could decrypt systems. THE attack it also works on Linux virtual systems in the Cloud.
The Debian and Fedora are two distributions that have been confirmed to be vulnerable to the problem.
The problem was identified by Hector Marco, a lecturer at University West of Scotland, along with assistant professor Ismael Ripoll from the Polytechnic University of Valencia. Researchers say the problem does not require a particular configuration of the system and they say:
This vulnerability allows [the hacker] to obtain a root initramfs shell on the affected systems. Vulnerability is very reliable, because it does not depend on specific systems or configurations.
Attackers can copy, modify, or destroy the hard drive as they create a network to export the data. Vulnerability is particularly severe in environments such as libraries, ATMs, airport machines, workshops, etc. where the entire boot process is protected by the BIOS password and GRUB and they have only one keyboard or a mouse.
The exploit has been repaired according to Marco and Ripoll.
http://hmarco.org/bugs/CVE-2016-4484/CVE-2016-4484_cryptsetup_initrd_shell.html





