Government hacking team North Korea's Lazarus added another tool in her arsenal. This time it's a Windows one Update client that uses the living-off-the-land binaries (LoLBins) technique to run malicious code on Windows systems.
The new malware development method was discovered by the Malwarebytes Threat Intelligence team during the analysis of a spearphishing campaign in January that claimed to be the American security and aerospace company Lockheed Martin.
If victims open malicious Word attachments and enable macros to run, a macro drops a WindowsUpdateConf.lnk file into the startup folder and a DLL file (wuaueng.dll) into a hidden Windows / System32 folder.
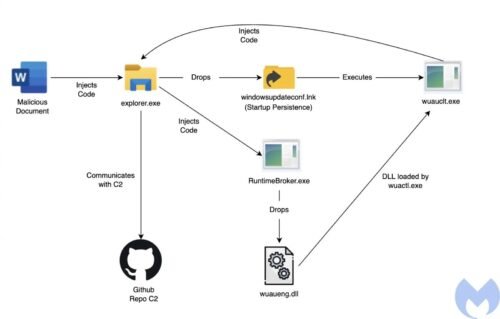
In the next step, the LNK file is used to launch the WSUS / Windows Update client (wuauclt.exe) which runs another command to load the malicious DLL of attackers.
"It's an interesting technique used by Lazarus to run its malicious DLL using the Windows Update Client and bypass security detection mechanisms." he says Malwarebytes.
Researchers linked these attacks to the Lazarus group based on several factors data, όπως τις επικαλύψεις των υποδομών-τεχνικών τους, τα μεταdata of documents and similar targeting to previous campaigns.
This tactic was discovered by MDSec researcher David Middlehurst, who found that intruders could use a Windows Update client to run malicious code on Windows 10 systems.
This can be done by loading a custom DLL and using the following command line (the command Lazarus used to load its malicious load):
wuauclt.exe / UpdateDeploymentProvider [path_to_dll] / RunHandlerComServer
MITER ATT & CK reports that the attack uses a way of defensive avoidance strategy known as Signed Binary Proxy Execution and allows intruders to bypass security software, control applications, and protect digital certificate validation, since everything is done through Windows Update.
The Lazarus group (also known as HIDDEN COBRA by US intelligence services) is a North Korean military hacking group that has been active for more than a decade, at least since 2009.





