Check Point Research (CPR) monitors Telegram activities and has collected a number of relevant data on the current conflict in Eastern Europe.
On the day Russia invaded Ukraine, CPR reported a sixfold increase in the number of Telegram war groups.
Το 71% των ομάδων αυτών που παρακολούθησε η CPR προωθούν flash news με μη επεξεργασμένες και συχνά ανεπιβεβαίωτες πληροφορίες. Το 23% έχουν συσταθεί για να συντονίζουν κυβερνοεπιθέσεις κατά της Ρωσίας, κυρίως DDoS. Το 4% των ομάδων στο Telegram ζητούν δωρεές σε κρυπτονόμισμα για την υποστήριξη της Ουκρανίας. Σε μια νέα δημοσίευση, η CPR παρέχει στοιχεία και παραδείγματα για κάθε μία από τις ομάδες, καθώς και τέσσερις συμβουλές κυβερνοασφάλειας για τους people who use Telegram. 
Some Telegram groups that coordinate cyberattacks in Russia have more than 250.000 users
– CPR urges people wishing to donate to Ukraine to be careful when sending money
A. Flash News and Updates (71% of groups observed)
B. Hacking \ Hacktivist groups targeting Russia (23%)
C. Donation requests for Ukraine (4%)
D. Other issues related to the conflict, some inactive and without users (2%)
Characteristics and examples of group A: Flash News / Updates
Basic features:
- Very active
- Thousands of messages a day, 24/7
Reports unprocessed, uncensored reruns of war zones
- Shares unconfirmed information and possible misinformation
Examples:
Figure 1. Live news channel “Russia vs. Ukraine Live news ”with over 110K users on Telegram
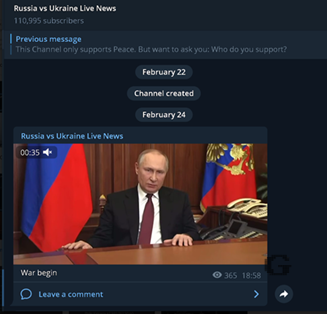
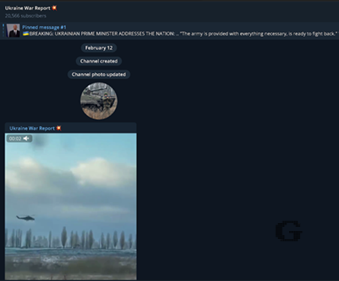
Figure 2. War reporting channel in Ukraine, with over 20 thousand users on Telegram
Characteristics and examples of group B: Hacktivists targeting Russia
Basic features:
- Hackers, IT Professionals and other "IT fans".
- Teams are used to coordinate attacks and select targets
- Teams assist each other in carrying out attacks and exchanging results
Some groups have more than 250.000 users
- DDoS the most common attack request, followed by attacks via SMS and calls
Examples:
Figure 3. SMS attacks and calls to Russian targets
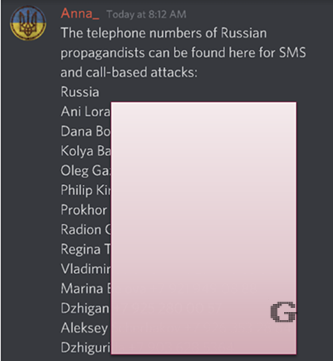
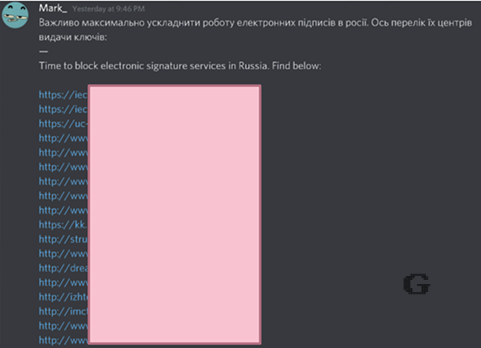
Figure 4. The Mark team invites users to attack Russian websites by providing URLs.
Characteristics and examples of group C: Donation scams
Basic features:
- Most donations require a cryptocurrency
- Teams have tens of thousands of users
- Many groups are suspicious and most likely fraudulent
Examples:
Figure 5. Group raising funds through Bitcoin and Ethereum accounts - Over 20k users
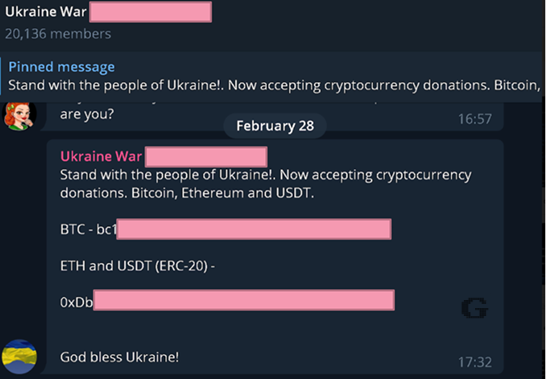
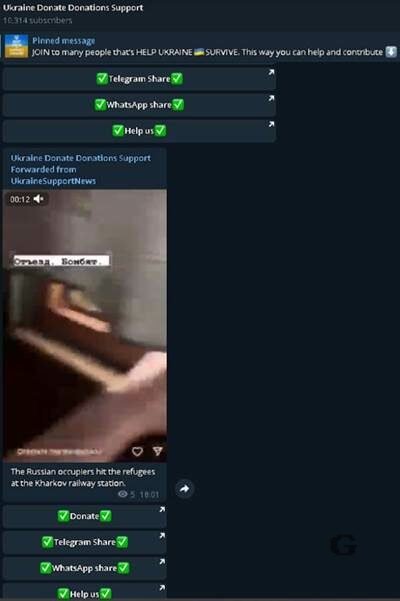
Figure 6. Donation support team for Ukraine on Telegram
Comment by Oded Vanunu, Head of Products Vulnerabilities Research at Check Point Software:
"Telegram has become a digital arena of conflict, where people choose sides on the internet. We see people from all over the world organizing and having the resources to support either Russia or Ukraine. Some groups are coordinating cyber attacks targeting Russia. Other groups serve as information and news hubs to present the raw side of the war. Other groups are demanding money either to support Ukraine or to commit fraud. Overall, we have seen a sixfold increase in Telegram groups on the Russia-Ukraine war since the day Russia invaded Ukraine. I highly recommend that people keep a close eye on their Telegram activity and the types of people they can come in contact with. There is a side in the Telegram that wants to take advantage of the supporters of either Ukraine or Russia. We are currently sharing what we see in the Telegram and our initial comments. We will continue to monitor the activity on Telegram in the coming weeks ".
Cyber security tips for Telegram users
1) Do not click random links. Do not click on links that are of unknown origin to you, especially in times of crisis and extreme circumstances. Criminals can take advantage of the situation to try to steal credentials, personal information and other personal information by sending malware or phishing links
2) Beware of suspicious requests. If a message from an unknown source makes a request or request that seems unusual or suspicious, this may be an indication that it is part of a phishing attack.
3) Think two times before sending money. Sending money to unknown sources for help can often lead to fraud. Be careful who you contact and what kind of information you are asked to provide. Social media messaging is not the right platform for big financial transactions, especially in unrecognized sources.
4) Verify your sources. Follow the news and seek the "truth" from reliable sources that you can trust.





