The Microsoft Defender Advanced Threat Protection (ATP) endpoint security platform now provides administrators with a new report designed to help them monitor vulnerable Windows and macOS devices that are connected to their organization's environment.

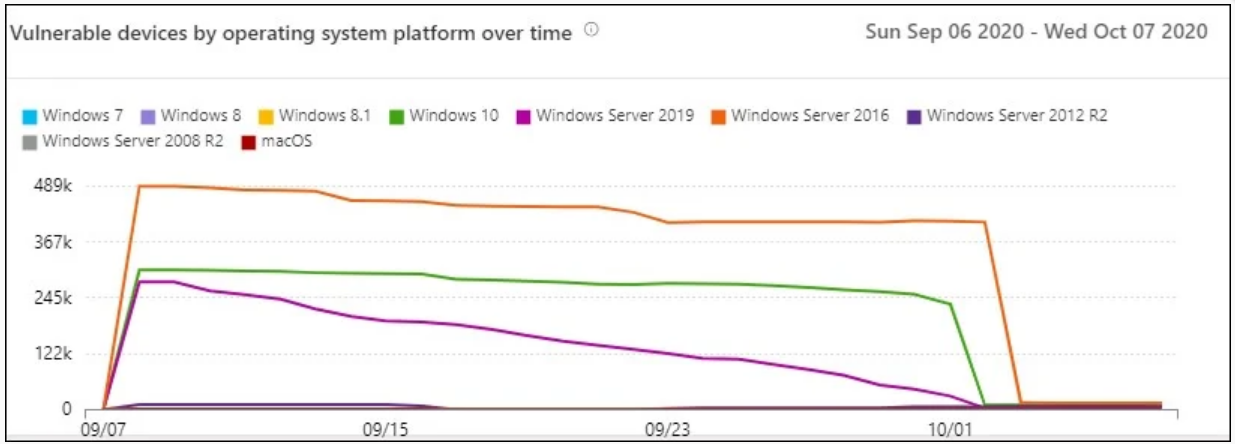
The Vulnerable Devices Report displays graphs with statistics and details on current trends in vulnerable devices with the ultimate goal of making it easier for administrators to understand the scope of reportof devices within the organization.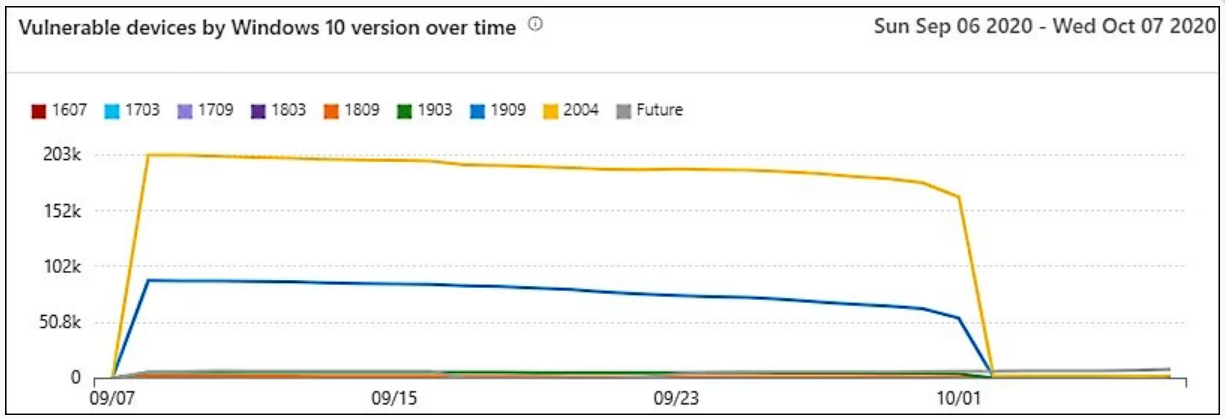
“You can filter data by levels of vulnerability severity, exploit availability, age της ευπάθειας, πλατφόρμα λειτουργικού συστήματος, έκδοση των Windows 10 ή team devices," says Microsoft.
"If there is something you want to explore further, select the relevant graph to see a filtered list of devices on the devices page. From there, you can extract the list. ”
Among the insights administrators can glean from this new Microsoft Defender ATP report (recently renamed Microsoft Defender for Endpoint), Microsoft states:
- Device vulnerability severity levels (eg all devices with critical vulnerabilities)
- Device exploit availability (eg all devices with exploit)
- Age of device vulnerabilities (eg devices with vulnerabilities published 90 days ago)
- Vulnerable devices from the operating system
- Vulnerable devices from the Windows 10 version
For example, the severity graph will show the number of devices based on the most serious vulnerability identified for each of them, while the exploit availability graph will show the number of vulnerable devices based on the severity of known exploits.
The new reporting feature is in public preview starting today and administrators can access it by going to Reports > Vulnerable devices in the Microsoft Defender Security Center after switching their OS to preview features.
Starting in July, Microsoft Defender ATP also added the Microsoft Secure Score for Devices feature that can assess the collective state of device security settings on a corporate network.
This feature detects unprotected systems and provides suggested actions to increase an organization's security.
A detailed description of the procedure that should be followed to address the issues identified by Microsoft Secure Score is available here.





