According to Microsoft, the Chinese cyber espionage group it's tracking called Volt Typhoon is targeting critical infrastructure organizations across the US, including Guam, at least until mid-2021.

Its victims include a wide range of critical sectors, including government, shipping, telecommunications, manufacturing, IT, utilities, transportation, construction, and education.
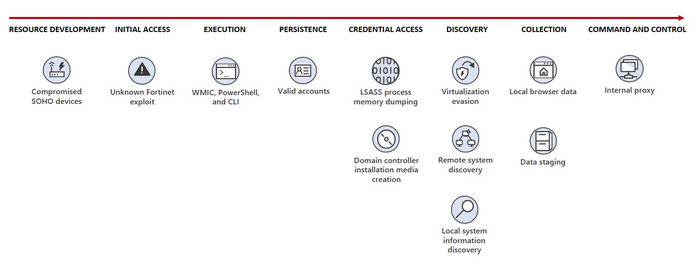
The first attack vector is to compromise Fortinet FortiGuard devices exposed to the internet by exploiting an unknown 0day vulnerability.
Once the target's network is compromised, they can use hands-on activities with it keyboard and PowerShell, Certutil, Netsh, Windows Management Instrumentation Command Line (WMIC), etc. Live off-the-land binaries (LOLBin) to launch what Microsoft describes as “living off-the-land” attacks.
However, according to a joint advisory released today by the FBI, NSA, CISA and the Australian, New Zealand, UK and Canadian cyber security agencies, they have identified Fast Reverse Proxy (frp), the hacking tool Mimikatz credentials, the Impacket network and frameworks, and other open source tools have also been observed.
Volt Typhoon combines malicious activity with legitimate network traffic to avoid detection, such as ASUS, Cisco, D-Link, Netgear, FatPipe and Zyxel, firewalls and VPN devices in compromised small and home office (SOHO) environments.
Using the privileged access gained after a Fortinet device is compromised, govt hacker credentials can be denied through the Local service Security Authority Subsystem Service (LSASS).
The stolen credentials allow them to deploy an Awen-based web shell to export and persist data to the compromised system.
As Mandiant Intelligence chief analyst John Hultquist said, these intrusions into US critical infrastructure organizations are a concerted effort to give China the advantage in the event of a future conflict between the two countries. It appears to be part of a concerted effort to give access to China in the event of a future conflict between the two countries.
"There are many reasons for targeting critical infrastructure, but an unrelenting focus on these areas may indicate preparations for disruptive or destructive cyber attacks," said Hultquist.
States conduct long-term incursions into critical infrastructure to prepare for potential conflicts. Similar emergency invasions are regularly carried out by states.
Over the past decade, Russia has targeted several critical infrastructure sites in operations that would not be considered rapid launch operations. China has similarly targeted the oil and gas sector in the past. While these operations are aggressive and potentially dangerous, they do not necessarily indicate that an attack is imminent."
Microsoft said it followed its normal procedures and proactively contacted all customers targeted or compromised in these attacks, providing them with the information they needed to protect their networks from future breach attempts.





