The exhibition "Kaspersky Security French Newsletter Overall Statistics"For 2015 highlights a new trend. For the first time, the mobile devices banking threats are among 10's top malware programs that have been deployed for money laundering. Two "Families" mobile banking Trojan - Faketoken and Marcher - found 2015 among 10's top bankers Trojan. Another remarkable and worrying trend for the year is the rapid expansion of ransomware programs. Kaspersky Lab has identified this trend in 200 countries and 2015 regions. 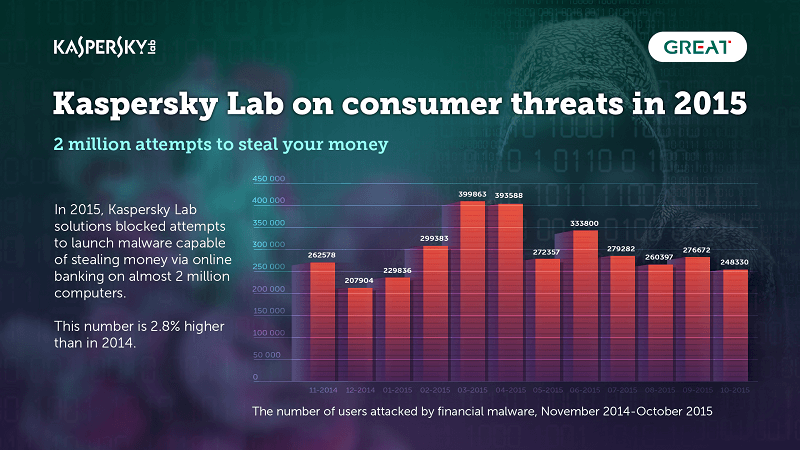
The main trends characterizing the activity of digital criminals 2015 also included the following:
- Seeking ways to minimize the risk of criminal prosecution, digital criminals have "gone" from malware attacks to aggressive adware distribution. 2015, adware programs accounted for 12 from 20 leading online threats, while ad programs were recorded on 26,1% of user computers.
- Η Kaspersky Lab παρατήρησε τη χρήση νέων τεχνικών συγκάλυψης προγραμμάτων exploit, shellcode και payload, καθώς οι ψηφιακοί εγκληματίες επιδίωξαν να καταστήσουν τον εντοπισμό των «μολύνσεων» και την ανάλυση του κακόβουλου code more difficult. In particular, digital criminals used the Diffie-Hellman encryption protocol and covered exploit packages on Flash objects.
- Digital criminals made active use of it technologyof Tor anonymizer to hide command servers, while they also used Bitcoins to make transactions.
The mobile devices banking threats mature
In 2015, two "families" of mobile banking Trojans (Faketoken and Marcher) appeared in the ranking of the top 10 "families" of financial malware. Programs in the Marcher "family" steal payment details from Android devices. Specifically, after having "infected" a device, these programs can detect the start of operation of two applications, the mobile banking app of a European bankand Google Play. When the user launches this app or Google Play, Marcher displays a "fake window", asking for credit card information, which then goes to the fraudsters. Programs in the Faketoken family work in "partnership" with computer Trojans. Specifically, the programs trick the user, who is asked to install an application on their smartphone. In fact, the app is a Trojan that intercepts the one-time verification code (mTAN).
"This year, digital criminals devoted time and resources to developing malicious financial programs for mobile devices. This is no surprise, as millions of people around the world use it smartphone to pay for services and goods. Based on current trends, we can assume that malware against service and solutions mobile devices banking, will represent an even greater part of the landscape of economic threats in the next year"He said Yury Namestnikov, Senior Security Researcher in its Global Research and Analysis Team Kaspersky Lab.
"Traditional" economic threats have not diminished. However, Kaspersky Lab's solutions have been able to block nearly two million (1.966.324) attempts to install malicious software capable of stealing money through 2015 online banking. This size is increased by 2,8% compared to 2014 (1.910.520).
His "detraction" ZeuS
Numerous modifications to Zeus, the most widely used malware software family, have been "deactivated" by malware Dyre / Dyzap / Dyreza. Over 40% of those infected by the 2015 Trojan bank were attacked by Dyreza, which used an effective Internet penetration method to steal data and access online banking systems.
The global nightmare of the programs ransomware
2015, ransomware programs quickly expanded their presence on new platforms. One in six attacks (17%) ransomware is now an Android device, just one year after the platform was first spotted for such programs. Kaspersky Lab experts identified two key trends in the ransomware field during 2015. The first is that the total number of users attacked by encryption ransomware increased to almost 180.000, a size increased by 48,3% compared to 2014. Secondly, in many cases, "cryptographers" become multifunctional, providing, in addition to encryption, functions designed to steal data from the victims' computers.
The geography of online attacks
Kaspersky Lab statistics show that digital criminals prefer to operate and use hosting services in different countries where the hosting market is particularly developed. 80% of alerts for antivirus-prevented attacks were received from online resources in 10 countries. The list of the first three countries where online resources were attacked by malicious software remained unchanged compared to the previous year (US with 24,2%, Germany with 13% and Netherlands with 10,7%).
The full version of the report is available on the site Securelist.com.
On the same site the total statistics for 2014 are also available.





