Check Point Research (CPR), its Threat Intelligence division Check Point Software Technologies Ltd. global cybersecurity solutions provider, has released its Brand Phishing Report for the third quarter of 2022.
The report shows the brands most often imitated by criminals in their attempts to steal personal information or payment credentials of individuals during July, August and September.

While LinkedIn was the most imitated brand in both the first and second quarters of 2022, shipping company DHL took the top spot in the third quarter, accounting for 22% of all phishing attempts worldwide. Microsoft is in second place (16%) and LinkedIn has dropped to third, accounting for just 11% of fraud, compared to 52% in Q1 and 45% in Q2.
DHL's rise could be partly due to a major global fraud and phishing attack about which the company itself warned a few days before the start of the quarter. Instagram also appeared in the top ten list for the first time this quarter, after a phishing campaign related to the "blue badge" was reported in September.
The transportation industry is one of the top industries for brand phishing, second only to technology. As we head into the most dynamic period for retail sales of the year, CPR will continue to monitor transport-related fraud as actions will likely increase their efforts to exploit online shoppers.
“Phishing is the most common type of social engineering, which is a general term that describes attempts to manipulate or deceive users. It is an increasingly common threat vector used in most security incidents,” commented Omer Dembinsky, Data Research Group Manager at Check Point. “In the third quarter, we saw a dramatic decrease in the number of LinkedIn-related phishing attempts, which reminds us that cybercriminals often change their tactics to increase their chances of success.
But it's still the third most copied company, so we'd urge all users to be wary of any emails or communications purporting to come from LinkedIn. Now that DHL is the brand most likely to be imitated, it is vital that anyone expecting a delivery goes straight to the official website to check progress and/or alerts. Do not trust any email, especially those that ask for information to be shared."
In a phishing attack, criminals try to impersonate the official website of a well-known company, using a similar domain name or URL and web page design to the authentic website.
The link to the fake website can be sent to targeted people via email or text message, the user can be redirected while browsing the web, or it can be activated by a rogue app to cell phones phones. The fake site often contains a form designed to steal users' credentials, payment information, or other personal information.

Top phishing brands in the 3rd quarter of 2022
The following are the top brands that rank based on their overall appearance in brand phishing attempts:
- DHL (related to 22% of all phishing attacks worldwide)
- Microsoft (16%)
- LinkedIn (11%)
- Google (6%)
- Netflix (5%)
- WeTransfer (5%)
- Walmart (5%)
- WhatsApp (4%)
- HSBC (4%)
- Instagram (3%)
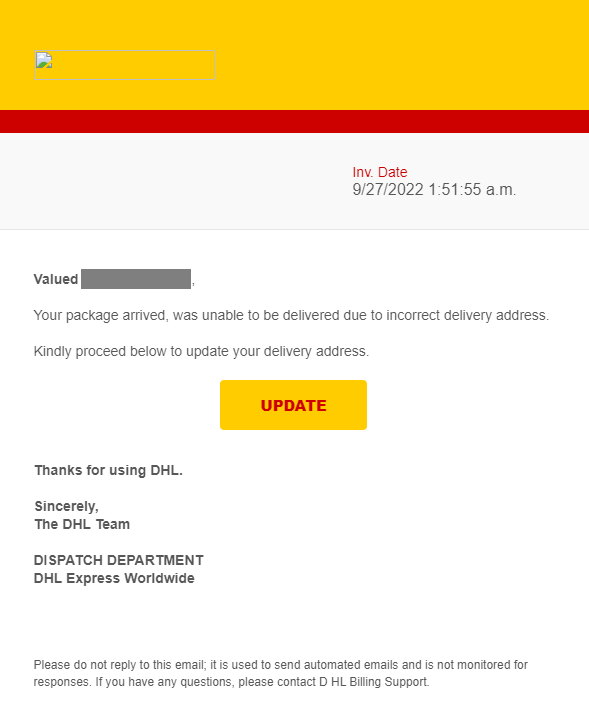
DHL Phishing Email – Example of account theft
Στο πλαίσιο εκστρατειών με τη χρήση του Branding της DHL που εμφανίστηκαν κατά τη διάρκεια του 3ου τριμήνου του 2022, παρατηρήσαμε ένα κακόβουλο ηλεκτρονικό μήνυμα ηλεκτρονικού ψαρέματος που εστάλη από μια διεύθυνση webmail “info@lincssourcing[.]com” και παραποιήθηκε ώστε να φαίνεται ότι εστάλη από την “DHL Express”. Το μήνυμα ηλεκτρονικού ταχυδρομείου περιείχε το θέμα- “Undelivered DHL(Parcel/Shipment)”, και το περιεχόμενο (βλ. Εικόνα 1) προσπαθεί να πείσει το θύμα να κάνει κλικ σε έναν κακόβουλο σύνδεσμο, ισχυριζόμενο ότι υπάρχει μια παράδοση που προορίζεται γι' αυτόν και μπορεί να αποσταλεί αμέσως μετά την ενημέρωση της διεύθυνσης παράδοσης.
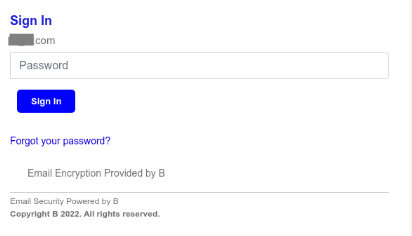
This link leads to a malicious website- “https://bafybeig4warxkemgy6mdzooxeeuglstk6idtz5dinm7yayeazximd3azai[.]ipfs[.]w3s[.]link/dshby[.]html/” (see Figure 2) which requires you to enter your username and password. victim's password.
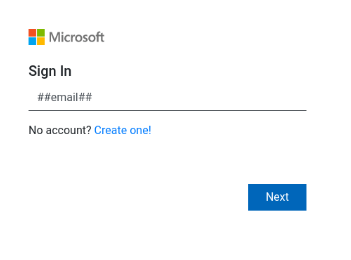
OneDrive Phishing Email – Example of Account Theft
In this phishing email, we see an attempt to steal a user's Microsoft account information.
The email (see Figure 1), which was sent from the webmail address “websent@jointak.com.hk” with a fake sender name – “OneDrive”, contained the subject “A document titled 'Proposal' has been shared with your OneDrive". The attacker tries to trick the victim into clicking on the malicious link by claiming that an important document titled “Proposal” has been shared with them on OneDrive.
This malicious link – ” https://mail-supp-365[.]herokuapp[.]com/” redirects the user to a fake Microsoft web app login page (see Figure 2) where the user has to enter his account password.

Όπως πάντα, ενθαρρύνουμε τους χρήστες να είναι προσεκτικοί όταν αποκαλύπτουν προσωπικά δεδομένα και διαπιστευτήρια σε επαγγελματικές εφαρμογές ή ιστότοπους και να σκέφτονται δύο φορές πριν ανοίξουν συνημμένα μηνύματα ηλεκτρονικού ταχυδρομείου ή συνδέσμους, ιδίως μηνύματα ηλεκτρονικού ταχυδρομείου που ισχυρίζονται ότι προέρχονται από Companies such as DHL, Microsoft or LinkedIn, as they are more likely to be impersonations.





