Avanan Company, by Check Point Software, ενημερώνει για μια νέα εξέλιξη στις επιθέσεις ηλεκτρονικού ψαρέματος, που φαίνεται να χρησιμοποιεί καθημερινές υπηρεσίες όπως το iCloud, το PayPal, το Google Docs and Fedex, in order to infiltrate users' inboxes and carry out attacks. This method is called “Phishing Scams 3.0” and does not require the creation of code, but simply a free account to carry out the attack.
-
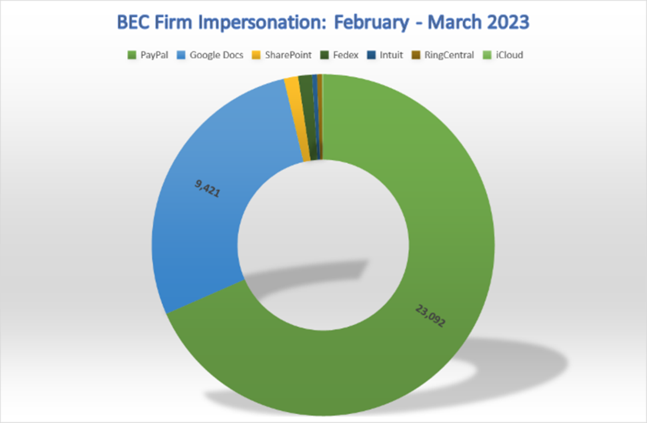
33.817 email attacks were observed in the last two months
-
The iCloud is the most impersonated service
-
Other influencer services: PayPal, Google Docs, SharePoint, Fedex, Intuit and other
How does it work:
1. THE hacker creates a free account (for example) on PayPal
2. The hacker finds email addresses to send.
3. The hacker creates a fake invoice that either concerns a user charge or a renewal process
4. The hacker clicks send.
In Numbers
In the last two months of February and March, investigators have seen us in total 33.817 email attacks, all impersonating legitimate, popular companies and services.
Comment of Jeremy Fuchs, Representative Press of Avanan, company of Check Point Software:
"Scams using the intermediary method, "Business Email Compromise (BEC), have evolved again. A traditional attack BEC it relies on the ability to look like someone with authority within a company or a trusted external partner. Attacks then shifted to a method where an attacker compromises an account, belonging to an organization or one of its partner organizations, and uses it to enter legitimate threads (threads) email, responding as if they were employees. Now, we're seeing something completely new, where attackers are using actual legitimate services to execute their attack. In such scams, the victim receives an email from a completely legitimate service (e.g. PayPal, Google Docs), which includes one to one link malicious website. In the last two months of February and March, our researchers have seen a total of 33.817 email attacks, all impersonating legitimate, popular companies and services. We call this new style of cyber attacks 'Phishing Scams 3.0 ' ή BEC Firm Impersonation. It is important to note that there is nothing malicious about these popular sites, nor is there any vulnerability. Instead, hackers use the legitimacy of these services to get into the inbox. I strongly encourage users to implement two-factor authentication and use email filters to protect against this style of attack.
Cyber Security Tips:
1. Use anti-phishing protection
2. Education and training of employees
3. Segregate tasks
4. Check every external email
Examples:
In the following example the hacker has added a comment to the Google sheets. All he has to do is create a free Google account. Then he can create a Google Sheet and state the intended objective. The recipient receives an email notification.
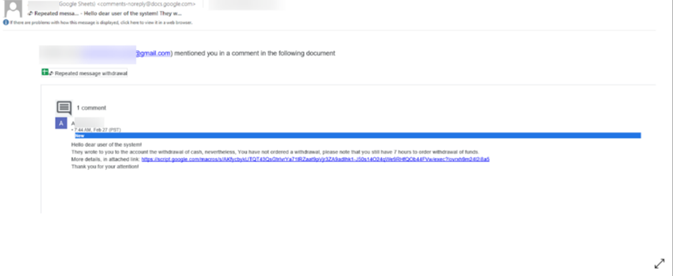
For the end user, this is a pretty standard email, especially if they are using Google Workspace. (And even if it doesn't, it's standard since many organizations use Google Workspace and Microsoft 365).
Here's another example, this time using Google Docs.
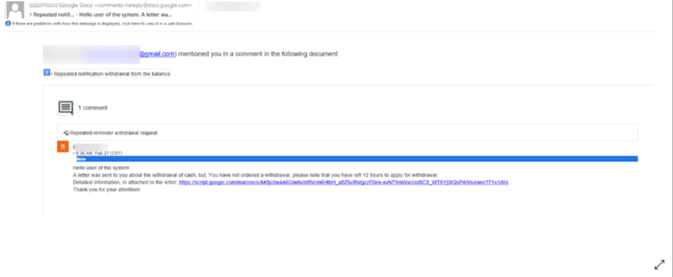
This is from a legitimate sender – Google. The URL, which is a script.google.com URL, is also legitimate on first scan. This is because this domain is legit.
However, when you click on it, it redirects to a fake crypto site. These fake cryptocurrency websites work in certain ways. They can be simple phishing sites where credentials will be stolen. Or there are a variety of other options, be it straight stealing or crypto mining.
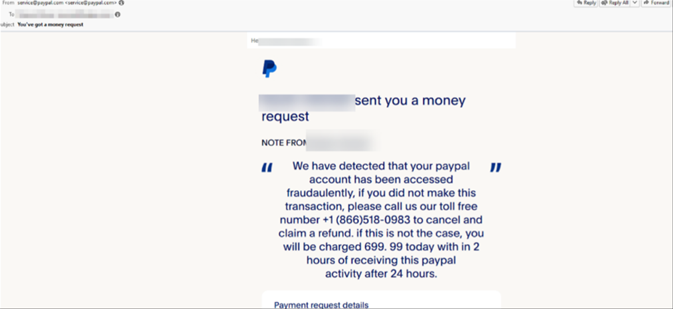
Example impersonation PayPal
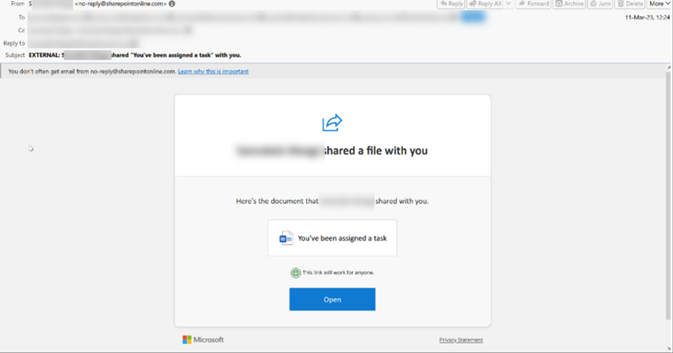
Example impersonation SharePoint
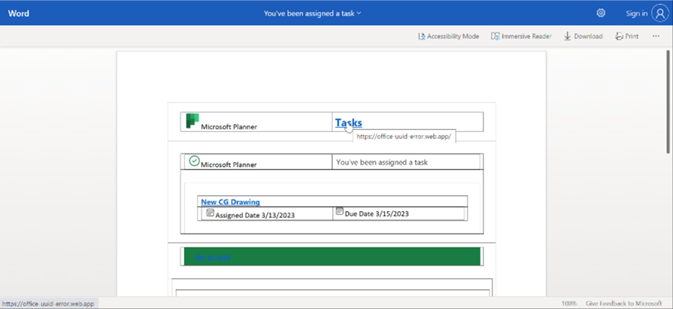
Phishing link hosted on SharePoint
In all recorded examples, the email address from which the email was sent appeared perfectly legitimate and contained the “correct” addresses, making detection and identification much more difficult for the average receiving user.





