With more cyber threats today than ever before, there are too many companies with poor security. On average, it takes over six months for a company to detect a data breach.
In recent years, network monitoring practices, such as log analysis, have become key tools for identifying security and performance issues that the network faces on a daily basis.

What is log analysis?
In a network, each computers creates an information file. A log file is essentially a chronological record of events that take place on a device. Devices and applications provide logs to document events on a device so that a user can easily refer to them. These files detail system events and user actions, such as opening or renaming a file.
It is important to note that there are many types of logs, such as event logs, control logs, transaction logs, message logs, and error logs, each of which tells you something different about your systems. Log analysis is the process of collecting, compiling, and tracking each of the types of logs created by devices and applications connected to your network.
Logs are a "goldmine" of information and include valuable records in your computer systems. By tracking the log data of these systems, you gain more visibility into your network infrastructure and information that helps you manage performance more efficiently.
You can open logs with a word processor or logger / logger. A logger is more efficient because it collects data from all these devices, collects it and stores it centrally, so you can easily control it with a single tool.

Why is logging analysis important?
Log analysis is important because it allows you to troubleshoot performance issues and resolve issues more quickly. Having a log analyzer with a device event retrieval recorder can find the root cause of security events much faster. Faster discovery speeds up your analysis time and reduces the risk and duration of downtime.
By taking a precautionary approach to managing performance issues, you can spot problems early or before they happen. High-speed analysis prevents unnecessary downtime, reduces costs associated with defective infrastructure, and ensures that your service remains available to your customers.
The use of a log analyzer is also necessary to demonstrate and maintain compliance with regulations. If you work in an industry with control or security policy requirements, log analysis provides a control path that you can use to verify that your computer systems are adequately protected.

How log analysis works
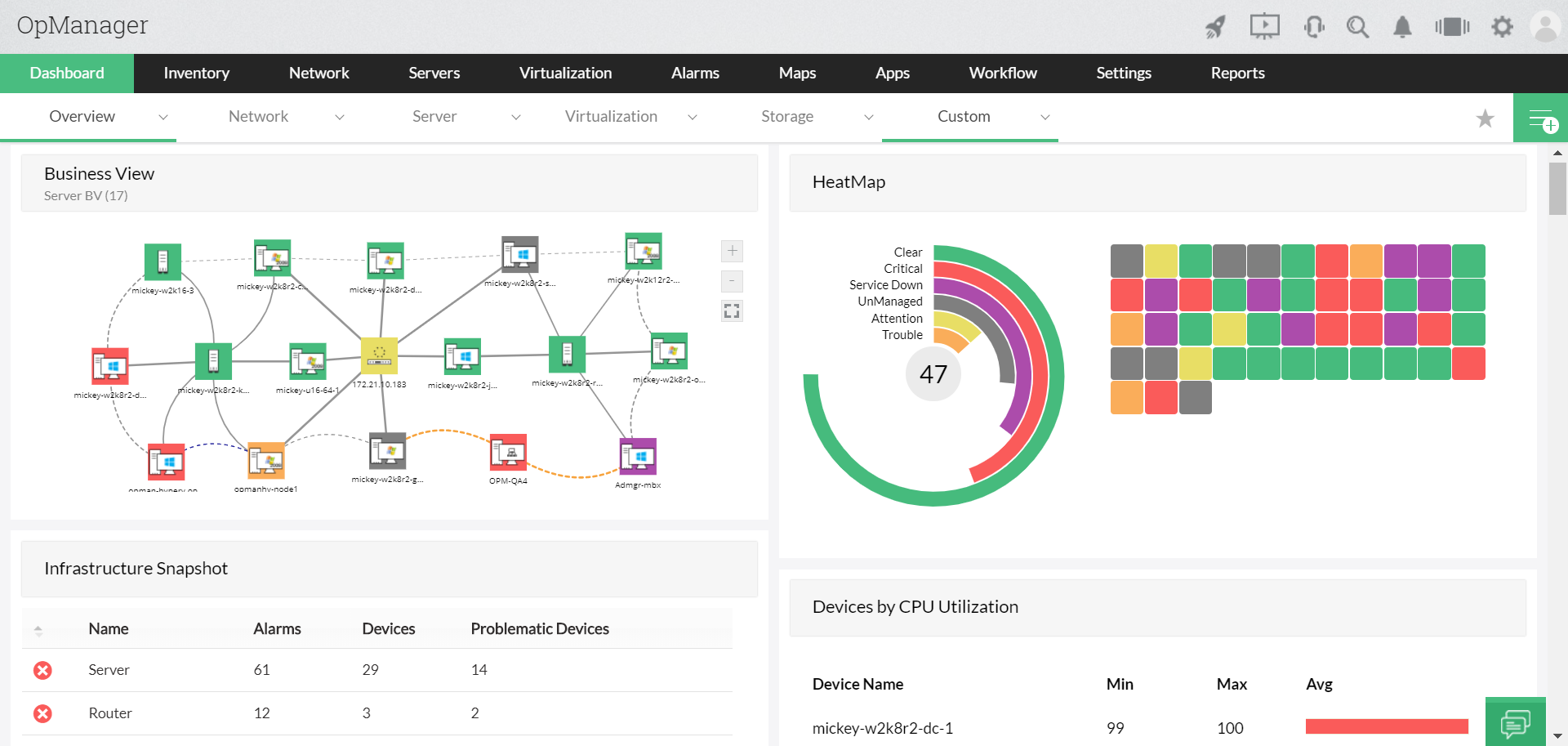
Devices across your network create logs, which are collected and stored by a log analyzer for tracking. In one place, you can track data received from different sources with the help of graphical features such as dashboards and graphs. Centralized log collection lets you track real-time performance events.
Many log analysis tools allow you to configure alerts which generate email or SMS alerts about important logging or security events when they occur. Collecting and aggregating your log data with a log analyzer makes the troubleshooting process much faster.
For example, if you find that your network has been compromised, you can perform a forensic analysis of your log data to find out where the intruder came from, including the vulnerability it exploited. All of this data provides you with contextual information that you can use to resolve the issue.
Cases of using log analysis
Logs are a flexible resource and you can use them to monitor in a variety of scenarios, such as managing security events, optimizing performance, maintaining compliance, and troubleshooting. For example, you can use a log analyzer to track live network traffic and detect threats such as DDoS attacks.
When you're not under attack, you can use log analysis to help you optimize the performance of your IT infrastructure. Log analysis allows you to monitor your resource usage so you can see how much storage space is available. This way, you can see when your infrastructure is struggling to meet user requests and add new pconditions considering.
Performance optimization also has the advantage of reducing disruption to your customers. By properly addressing performance issues, you minimize the likelihood (and inconvenience) of service downtime and reduce the likelihood of customer alienation due to poor user experience.
Machine Learning and threat detection
One feature offered by many log analytics is threat detection. Threat detection uses mechanical learning to locate them and perform on log entries received from your network. These systems look for unusual events that indicate a performance problem or other malicious activity. The system then notifies the user for further investigation.
Threat detection is invaluable because it automatically searches regardless of log data and filters unrelated updates καταγραφής. Η υιοθέτηση ενός αναλυτή καταγραφής με μηχανική learning it's a very efficient way to manage performance issues, which reduces the amount of manual monitoring you have to do.

Protect your systems with log analysis in 2020
Logs are an undervalued resource. Developing a log analyzer for performance data collection allows you to monitor network performance much more efficiently. Regular analysis of logs will give you confidence that you have met the regulatory requirements and have the measures to protect the systems on which you rely on a daily basis.
With a wealth of affordable log analysis solutions on the market, now is the time for businesses to diversify their network monitoring strategies. In 2020, log analysis will be the key for businesses that want to maximize the miles coming out of their infrastructure.





