Recent documents revealed by Edward Snowden show that the US National Security Agency (NSA) and the UK's secret service (GCHQ) hacked the video feeds of Israeli unmanned aerial vehicles (UAVs, drones).
Like most military aircraft these days, drones are equipped with videocameras. These cameras are used for recording material but also for remote control of the aircraft.
The data collected by the aircraft cameras are coded and sent to satellites. They are then transferred to military bases or other special ground stations.
According to the documents leaked by Snowden, the US and the UK had set up such a ground station in location of Troodos in Cyprus, in 1998, especially for the videos collected by the Israeli drones.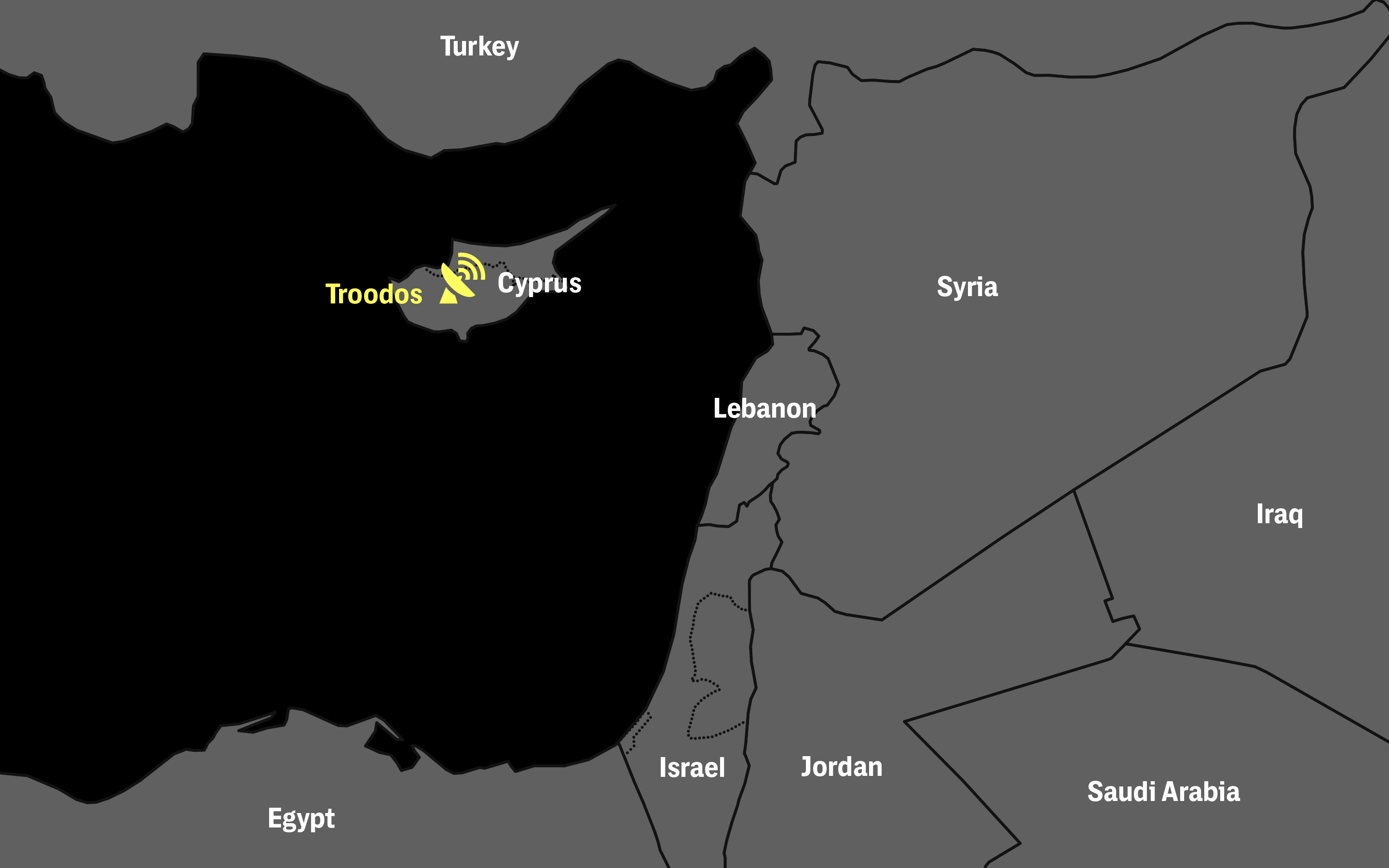
The US and UK intelligence services began using a wide net to spy on video feeds, but eventually narrowed the scope when they discovered the individual frequency of each drone. The technique is similar to that uses someone to listen to her radio frequencies polices.
1997, however, Israel has discovered that Hezbollah managed to kill 12's commanders after he passed the feeds without encryption by a drone. Since then, Israel has reportedly implemented encryption for all drone video feeds.
This did not prevent US and UK agents, who 2008 discovered that by intercepting periodic snapshots of encrypted video feeds, they could use a C library called AntiSky to decode the aircraft's camera record.
Edward Snowden's revelations and the leaked NSA documents exist at TheIntercept.





