Today we will show you how to use Android device you as Rubber Ducky to do HID attack on an Android device or PC.

This feature already exists in Kali Nethunter and what it actually does is through a device Android, access another device.
We are given the possibility to bypass it screen lock, as well as taking full control of a device and for future use.
HID attacks with Android
It's not a new one technique, just a demonstration of how to perform a HID attack using Android instead of a rubber ducky stick. The Android device we will attack does not need to be rooted, to have the ADB/USB option enabled or not, and to have the device authorized, since the attacker's smartphone acts as a connected keyboard.
hid_attack: the script contains custom commands that are executed against the target Android device or computer we want to attack.
The script may not work every time. Therefore, we must play with the keys we send to our target and change the exploit if it does not succeed with the first one. A list of all possible keys can be found at the link below.
What we need
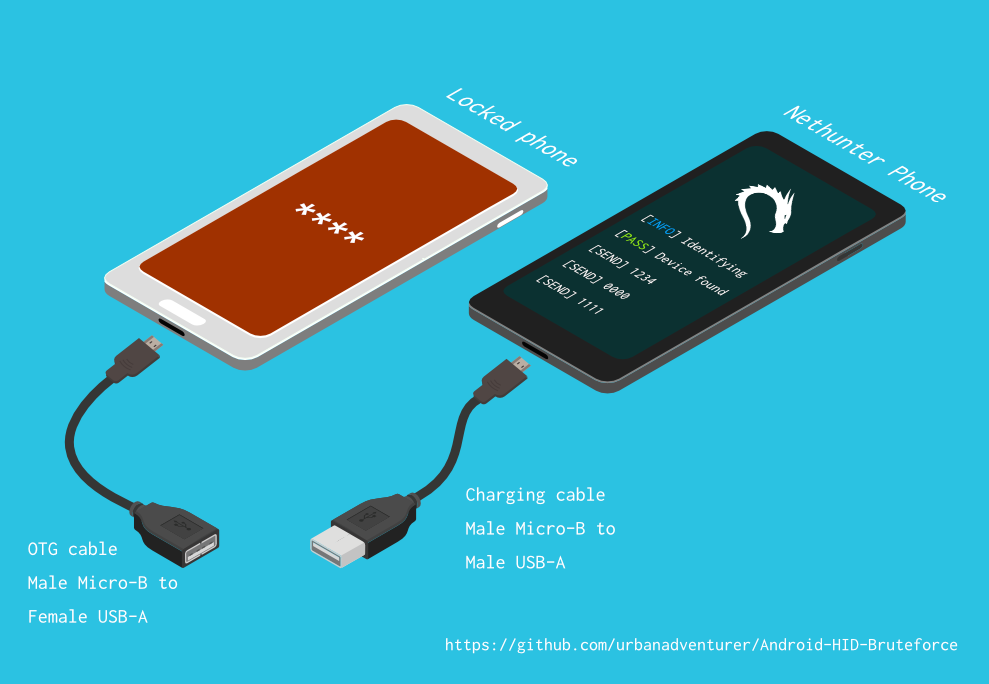
- A rooted Android device with support HID attacks on Kernel settings (eg NetHunter ROM)
- OTG cable
Specifications
- Crack PINs of any length from 1 to 10 digits.
- Use configuration files to support different phones.
- Optimized PIN lists for 3,4,5 and 6 digits.
- Bypasses phone pop-ups including low power warning
- It detects when the phone is disconnected or turned off and waits while retrying every 5 seconds
- Adjustable delays in N seconds after every X PIN attempts
- Creates Log file
Advantages
- Turn your phone into a PIN cracking machine.
- Unlike other methods, you don't need to have ADB or USB Debug enabled on the locked phone.
- The locked Android phone does not need to be rooted.
- No need to buy specialized hardware, e.g. Rubber Ducky, Teensy, Cellebrite, XPIN Clip, etc..
- You can easily modify the backoff time to jailbreak many types of devices.
Use
Android-PIN-Bruteforce (0.2) is used to unlock an Android phone (or device) by bruteforcing the lockscreen PIN.
Find more information at: https://github.com/urbanadventurer/Android-PIN-Bruteforce
Commands:
crack Begin cracking PINs
resume Resume from a chosen PIN
rewind Crack PINs in reverse from a chosen PIN
diag Display diagnostic information
version Display version information and exit
Options:
-f, --from PIN Resume from this PIN
-a, --attempts Starting from NUM incorrect attempts
-m, --mask REGEX Use a mask for known digits in the PIN
-t, --type TYPE Select PIN or PATTERN cracking
-l, --length NUM Crack PINs of NUM length
-c, --config FILE Specify configuration file to load
-p, --pinlist FILE Specify a custom PIN list
-d, --dry-run Dry run for testing. Doesn't send any keys.
-v, --verbose Output verbose logs
Usage:
android-pin-bruteforce [options] PoC for Android
PoC for PC
PoC with Nethunter
PoC without Nethunter
How to avoid such an attack
- We always charge our cell phone with ours charger
- We always use a complex screen lock code or a complex pattern
- We use protection programs on our device and more specifically programs that detect and prevent exploits.
HID support in custom ROM
https://github.com/pelya/android-keyboard-gadget
Brute-force attack using our Android
https://github.com/urbanadventurer/Android-PIN-Bruteforce
List of all available keys
https://github.com/anbud/DroidDucky/blob/master/droidducky.sh





