In previous guides on iguru, we have used the Burp Suite for various purposes. To test, evaluate and hack online applications. BurpSuite is one of a set of tools that each hacker/pentester/bug bounty hunter he should know!
Burp Suite is an excellent web site hacking tool used by many pentesters to check for vulnerabilities in websites and web applications.
Burp Suite works with detailed knowledge of the implementation of an HTTP protocol. This tool works through an algorithm that can be configured by settings and can generate malicious requests attacks HTTP used by a hacker.
Burp Suite is particularly useful for discovering vulnerabilities such as SQL injections and cross-site scripting.

In this guide, we will use BurpSuite to scan a web application for vulnerabilities. Fuzzing is the process of sending random data to an application in order to crash the application and thereby identify vulnerabilities (if any). If we can crash an application with some random input, we can then identify the cause of the crash and potentially use it to exploit the application. So, for example, if we send data that is too large for the application to handle and the application crashes, this may indicate a possible vulnerability buffer Overflow.
So we're going to use BurpSuite to send specially formatted input to a web application in an attempt to discover SQL vulnerabilities injection and XXE. It's a great technique for finding vulnerabilities for bug bounty!
Step #1: Open Kali and OWASP-BWA
The first step, of course, is to start Kali and OWASP-BWA.

Now, open your browser and click on the Mutillidae II application. This should open the app as shown below.
Step #2: Open BurpSuite
Then launch BurpSuite in Kali.
In your browser open it OWASP2013->Injection (SQL)->SQLi-Bypass Authentication ->Login.
This will open a screen similar to the one below.
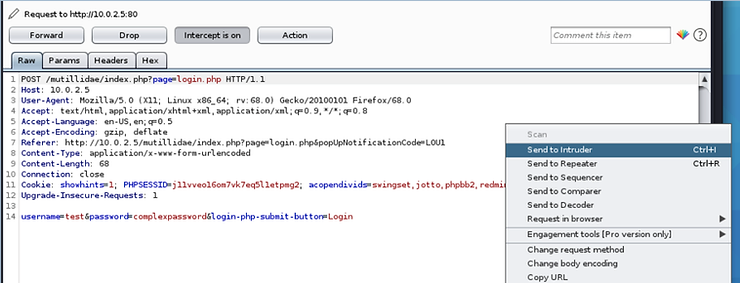
Now, with Intercept ON (and browser proxy enabled) in the proxy server in BurpSuite, type any random username and password. I used "test" and "complexpassword". The proxy will catch or intercept the request as shown below.
Right click and select Send to Intruder
Now, click on the tab Intruder at the top of the page. This opens Intruder showing 4 tabs, Target (Target), Stances (Seats), Payloads (Payloads) and Options (Choices).
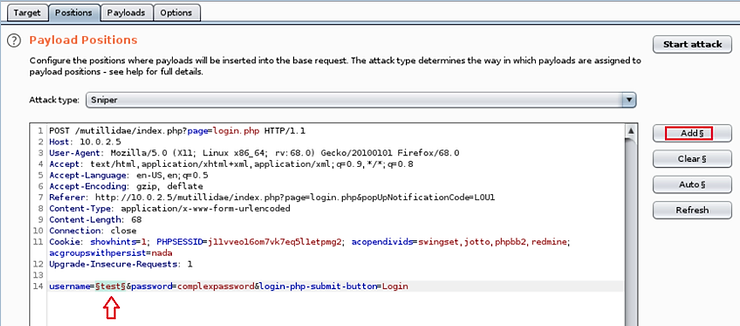
Select Positions. Intruder will highlight various possible locations of the payload. Click the button Clear (Clear) on the right side. Now highlight the field username and click the button Add.
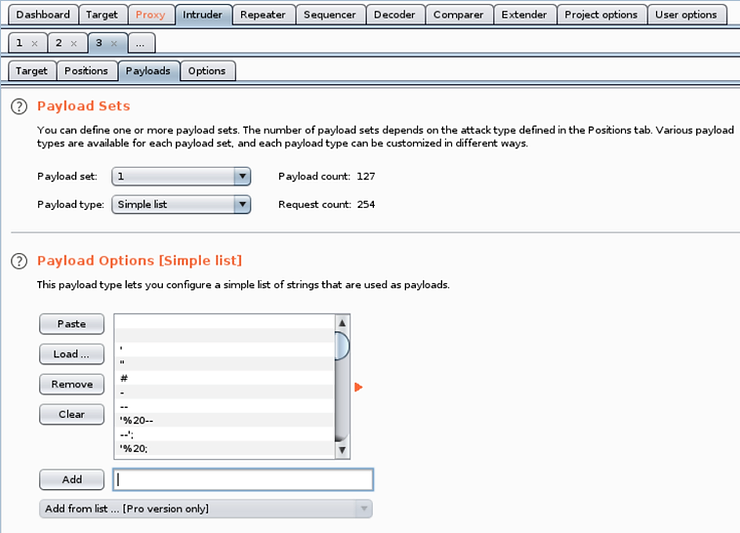
Then click on Payloads. Here you should add a payload or a list of fuzzing strings.
When fuzzing, we have several options for input strings. We could send millions of random inputs that could take hours or days, or we could send specially configured inputs that look for a specific type of vulnerability. Here we are specifically looking for SQLi vulnerabilities, so let's use a smaller and specific list of SQLi inputs.
We can go to the Kali terminal and search for fuzzing string wordlists by typing:
kali > locate wordlists | grep fuzzy
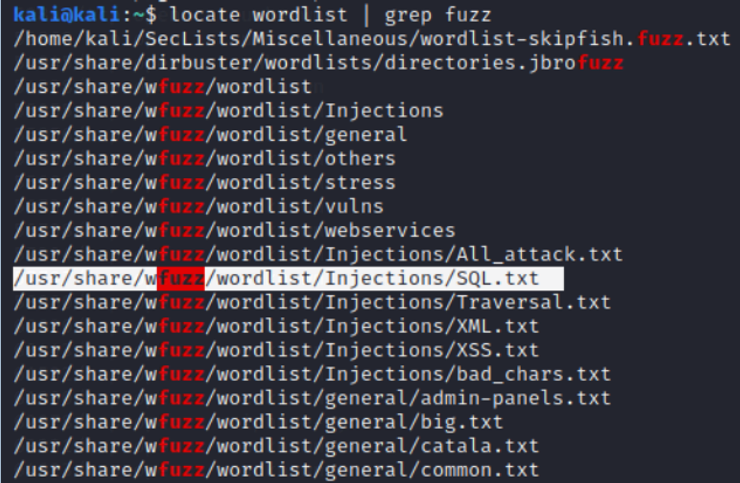
This will find all word lists and filter for the word “fuzz”. There are many, but let's use one specifically for SQL, such as usr/share/wfuzz/wordlists/Injections/SQL.txt.
This list contains many strings that can potentially cause SQL injection. Of course, you can use any of these word lists to find vulnerabilities, but this one looks specifically for SQLi errors.
On the screen payload, click the button Load (Load) and enter the path to the file SQL.txt.
Finally, click the button Start attack and BurpSuite will start testing each of the strings in the username or any selected field.
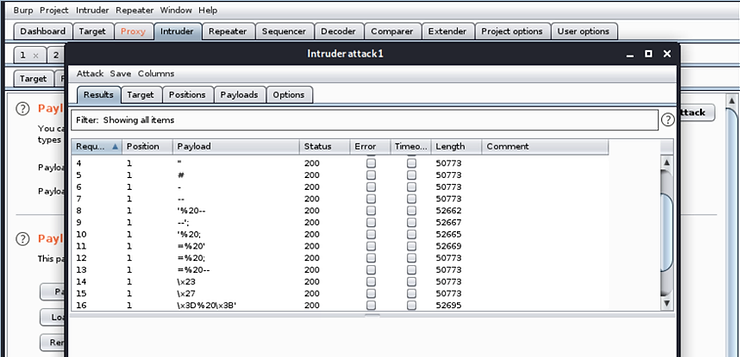
To identify potential SQL Injection vulnerabilities in this form in this application, look for anomalies in Status and the size of Responses. Almost all of these answers are 50773 long, but several are longer. Longer responses are a possible indication of a successful SQLi attack.
Step #3: Fuzzing for XXE vulnerabilities
We can do the same type of fuzzing to check for XXE vulnerabilities, but with an XML-specific input list.
To check for XXE vulnerabilities, go to the XML validator in Mutillidae.
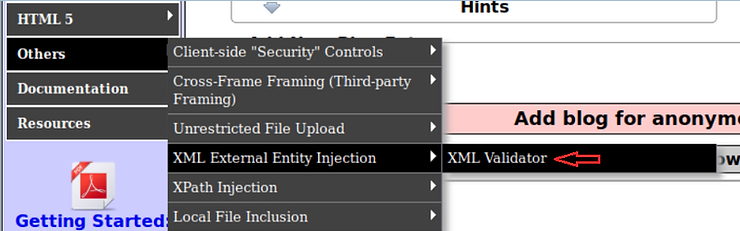
With the window open as below and Intercept ON in the BurpSuite proxy, enter any input into the window XML and click Validate XML.
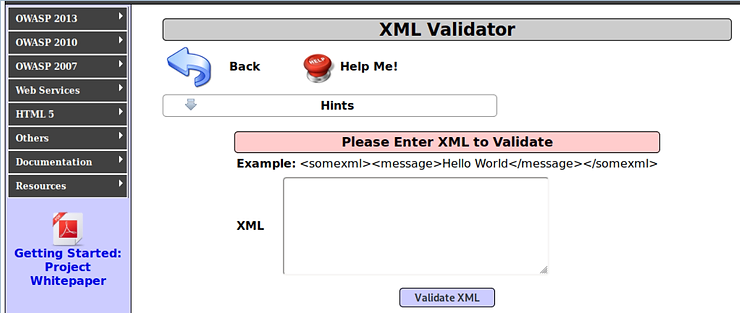
Ο proxy doescatch" the request as shown below.
Now, right click on the proxy and select “Send to Intruder". Open Intruder and clear the slots as you did above. Now, highlight your input and click the button Add.
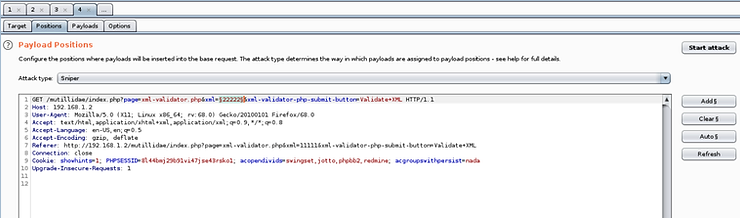
Then click the tab Payloads and load the XXE fuzzing file from the directory wfuzz wordlist (other XXE fuzzing strings are available at /Seclists/Fuzzing/XXE-Fuzzing.txt).
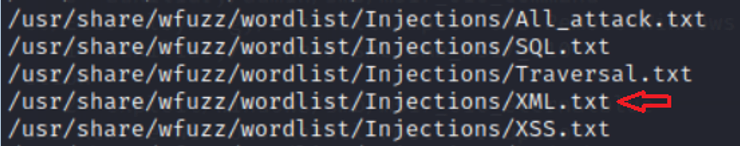
Note that the directory contains XML-related strings.
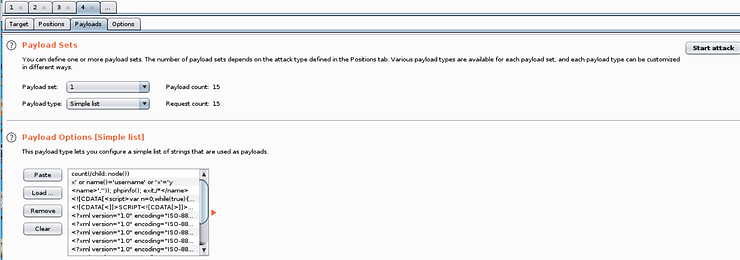
Finally, click the “Start attack".
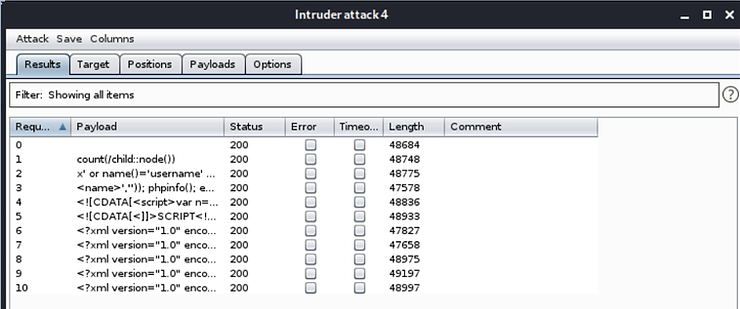
Your Burpsuite will attempt to send these XML strings to the validator. As with SQL injection fuzzing above, search variations on the state and length of the bug to find anomalies that would indicate a potential vulnerability.
Summary
Fuzzing can be a powerful technique for finding hidden vulnerabilities in web applications. BurpSuite enables us to locate almost any form in a web application and send specially configured inputs to the form.
By then reviewing the results for anomalies, we can identify potential vulnerabilities. BurpSuite can be used to scan every input in a form for vulnerabilities.





