Osmedeus lets you do Pentesting automatically, such as identifying and scanning the target, performing its collection of awesome tools.
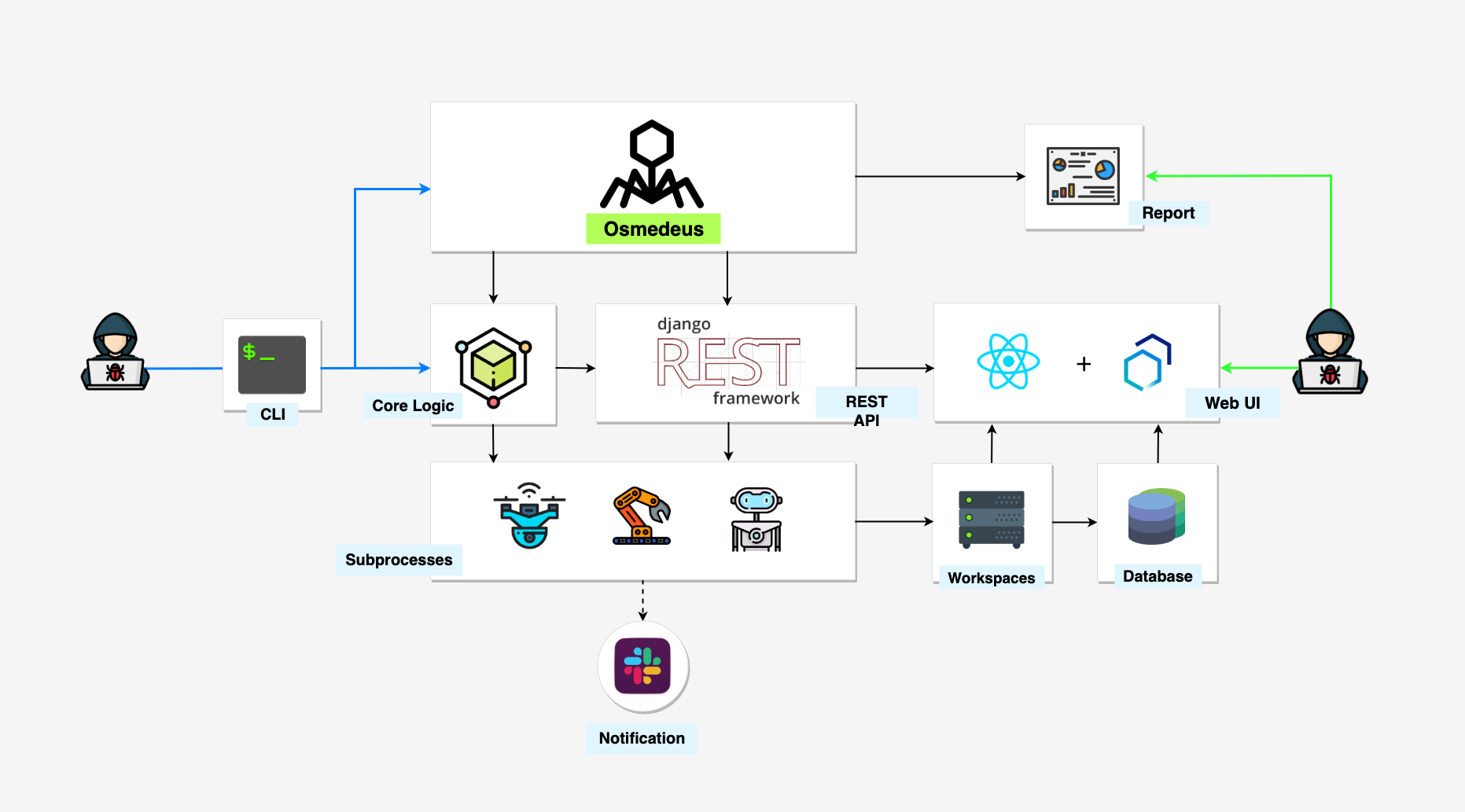
Specifications
- Subdomain Scan.
- Subdomain TakeOver Scan.
- Screenshot the target.
- Basic recon like Whois, Dig info.
- Web Technology detection.
- IP Discovery.
- CORS Scan.
- SSL Scan.
- Wayback Machine Discovery.
- URL Discovery.
- Headers scan.
- Port Scan.
- Vulnerable Scan.
- Seperate workspaces to store all scan output and logging details.
- REST API.
- React website UI.
- Support Continuous Scan.
- Slack notifications.
- Easily view report from commnad line.
Installation
git clone https://github.com/j3ssie/Osmedeus cd Osmedeus chmod + x install.sh ./install.sh
Use
# normal routine ./osmedeus.py -t example.com ./osmedeus.py -T list_of_target.txt # normal routine but slow speed on all moddule ./osmedeus.py -t example.com --slow 'all' # normal routine but exclude some modules ./osmedeus.py -t example.com -x 'linkfinding,dirb' # direct mode examples ./osmedeus.py -m subdomain -t example.com ./osmedeus.py -m portscan -i " 1.2.3.4/24" ./osmedeus.py -m "portscan,vulnscan" -i "1.2.3.4/24" -w result_folder # direct list mode examples ./osmedeus.py -m portscan -I list_of_targets.txt ./ osmedeus.py -m portscan,vulnscan -I list_of_targets.txt ./osmedeus.py -m screen -I list_of_targets.txt -w result_folder # report mode ./osmedeus.py -t example.com --report list ./osmedeus.py -t example.com --report export ./osmedeus.py -t example.com --report sum ./osmedeus.py -t example.com --report short ./osmedeus.py -t example.com --report full
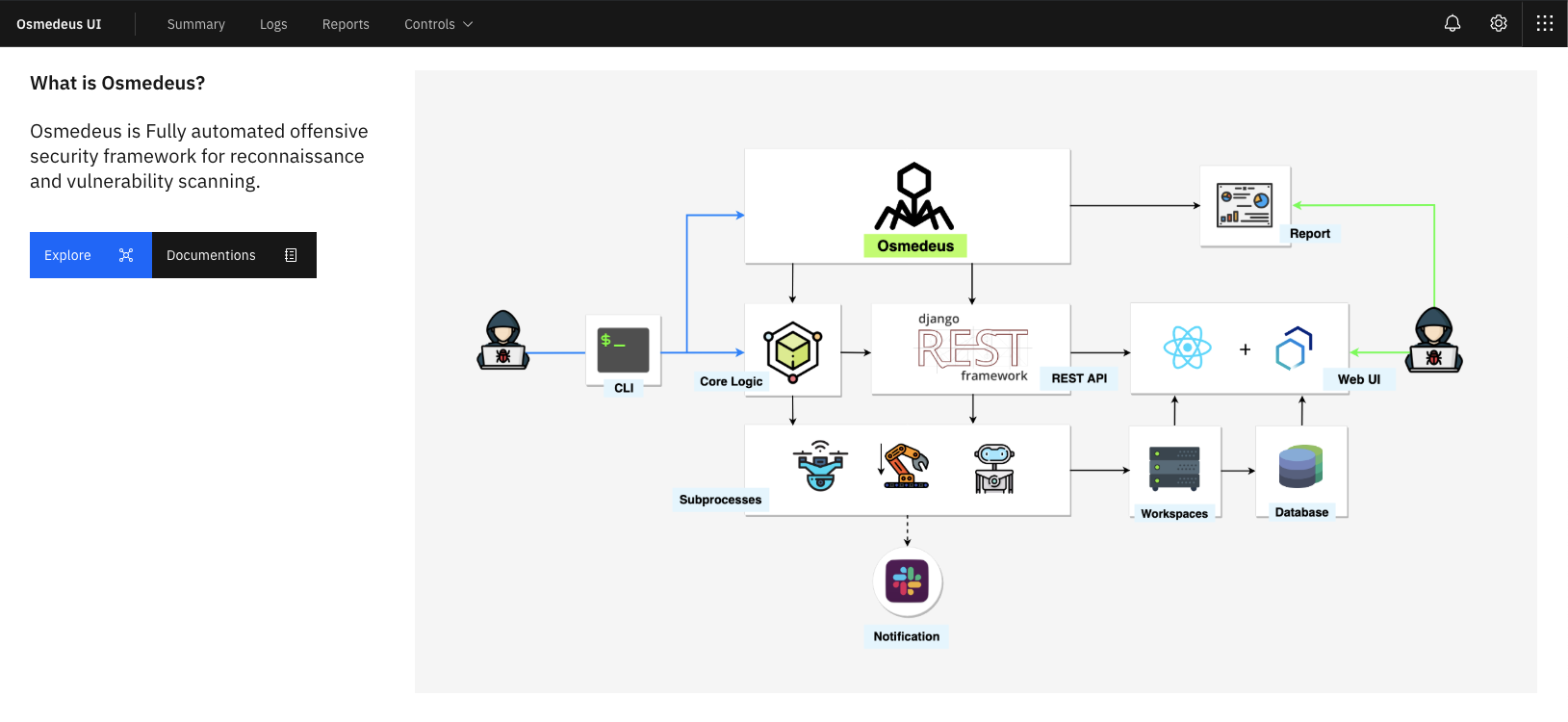
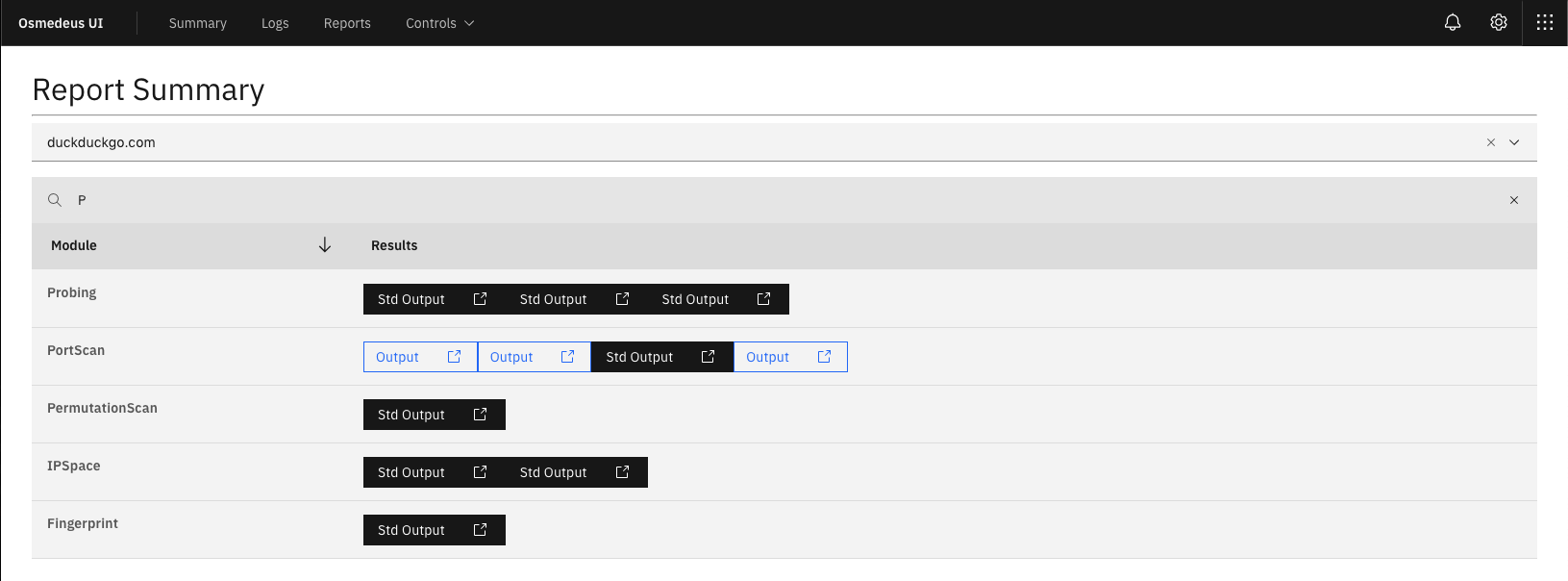
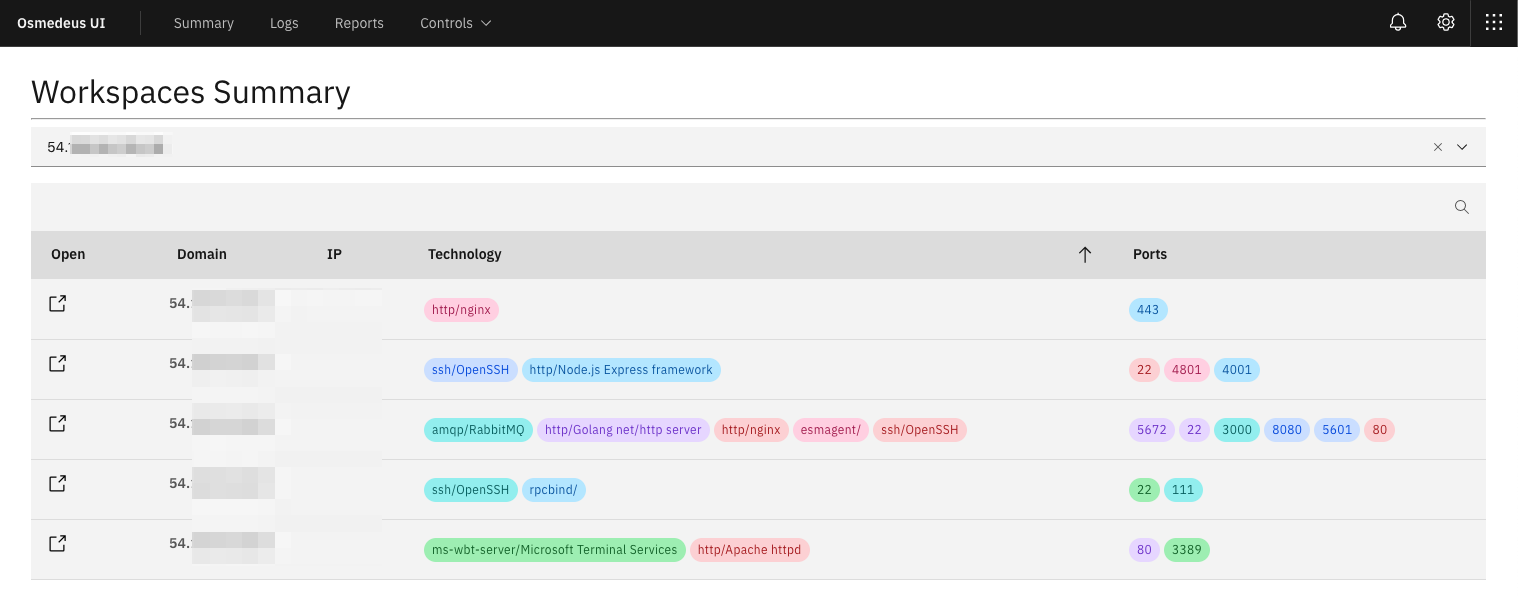
Application snapshots
You can download it program from here.





