Researchers at Avanan, a Check Point Software company, have identified and blocked a cyberattack that misled the CFO of a major sports organization for financial gain.
The perpetrators tried to trick a low-ranking executive in the finance department into sending money to a supposed insurance company. The cyberattack technique used is known as a Business Email Compromise (BEC) attack, where cybercriminals impersonate the organization's executives for financial gain. The researchers of Avanan warn that these cyberattacks are on the rise, playing on people's desire to make a good impression on their boss.
- Attackers have struck more than once
- Two examples of spoofed emails caught in the campaigns are provided
- Avanan researchers provide several cybersecurity tips to protect against BEC attacks
Researchers at Avanan, a Check Point company, identified a cyberattack impersonating the CFO of a major sports organization to convince a low-level employee to send money directly to the hackers. The fake CFO asked for a telegram to be sent to a company that appeared to be an insurance company. Avanan Research managed to block the cyber attack.
It is fair to assume that the drive behind the attack was financially motivated. Little information is known about the attackers, except than they have hit more than once.
Methodology of the attack
The type of cyberattack used is known as a Business Email Compromise (BEC) attack. The attack methodology in this case was as follows:
- The hacker first created a fake account of the company's CFO
- The hacker finds the legitimate email address of a financial team member
- The hacker creates an email message that looks like it was sent by the CFO, with instructions for the process attached.
- The finance manager asks the employee to remit money immediately
- If the employee "bites", the money will end up in the hacker's account
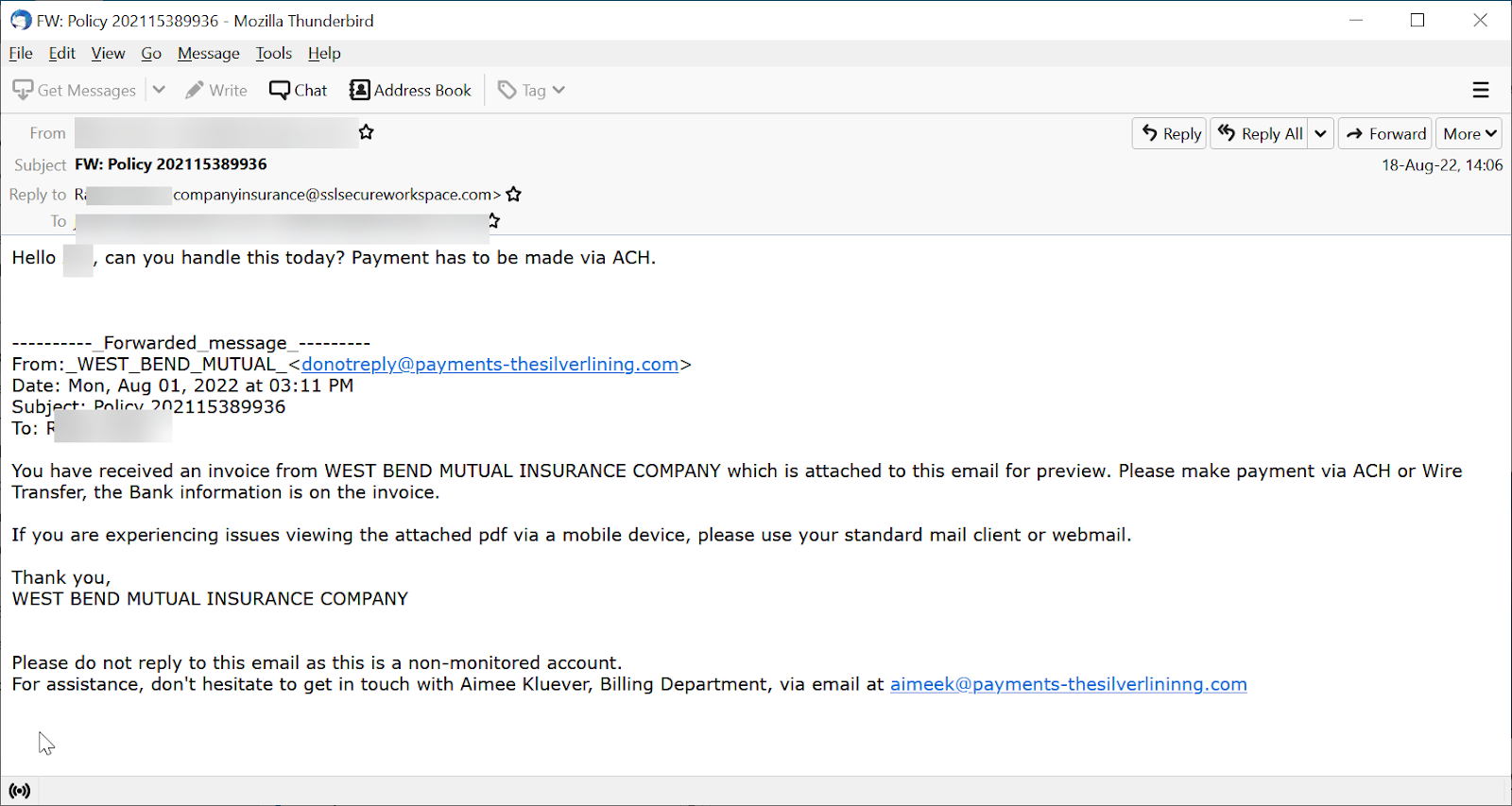
Email Example #1
The user receives an email from the CFO of this large company.
The finance director asks the email recipient to make a payment to a legitimate insurance company, West Bend Mutual. Even smarter is the fact that the URL in the “from” address comes from her tagline.
However, this is clearly a fake, as the "reply-to" address at the top of the email is different from the company's email address. You will notice the banner indicating that the email is not from the displayed sender. This was added by the tenant's generic Office 365, not Proofpoint. It's the only thing that alerted the end user that something was wrong.
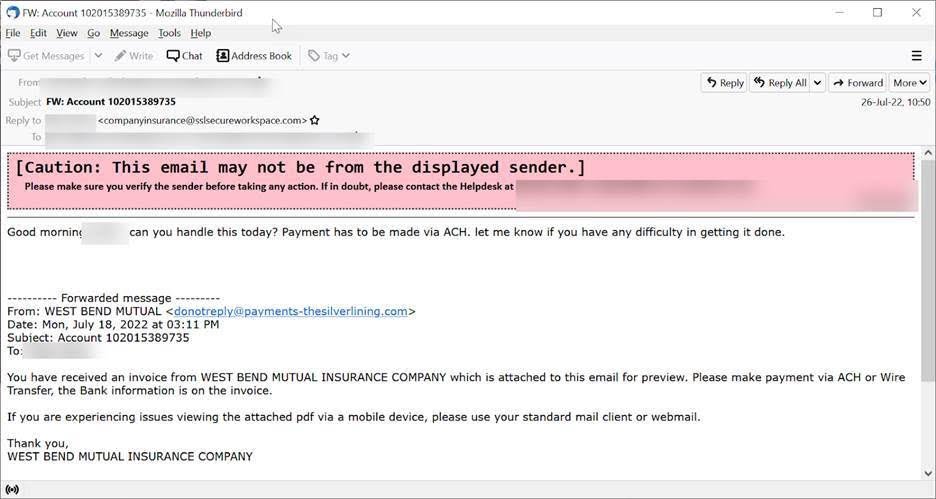
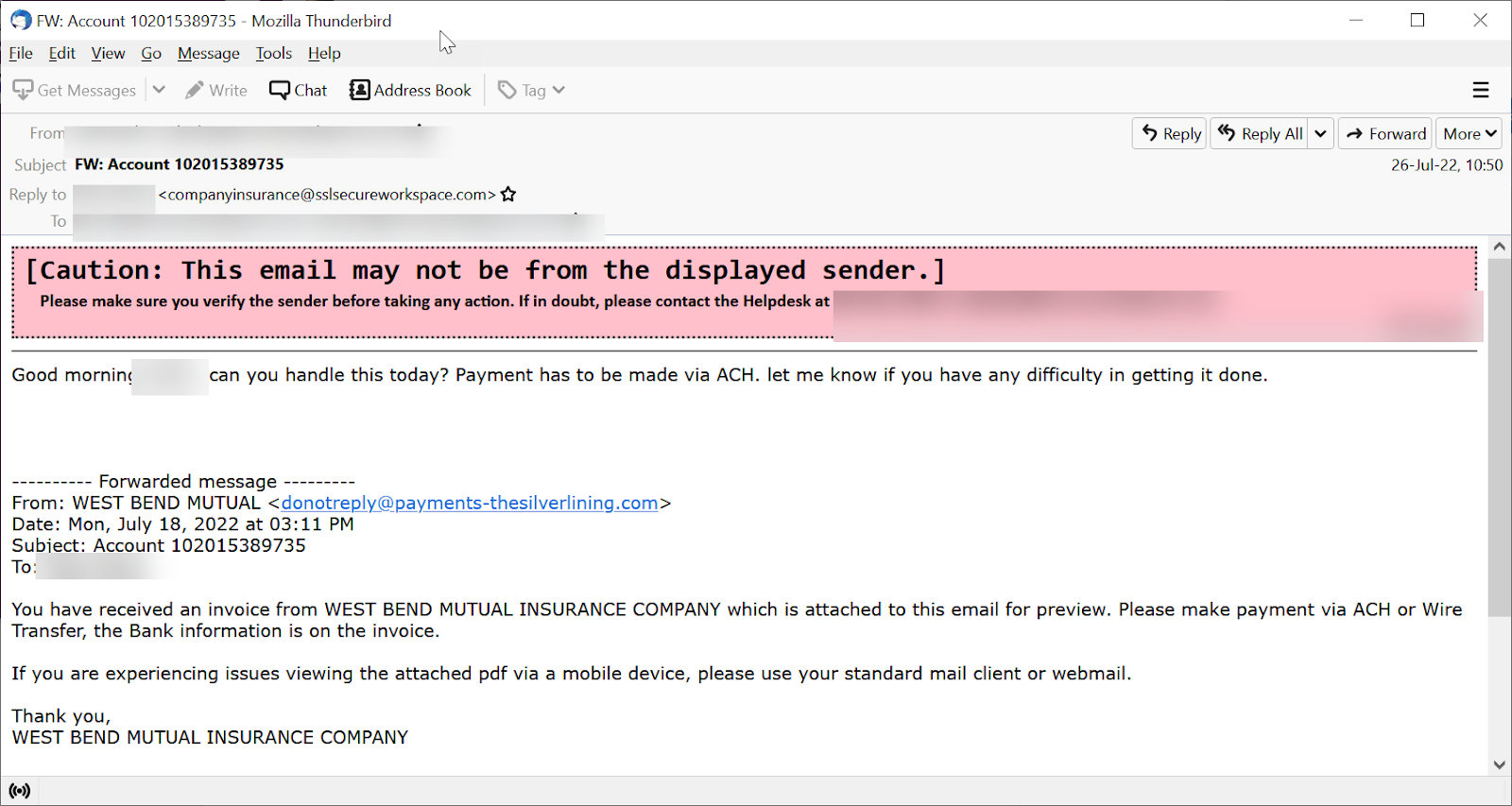
Email Example #2
This is an almost identical email that affected another company. In fact, we've seen dozens of these types of attacks.
Notice two differences: There is no external banner warning the end user of potential danger - the “Contact” email at the bottom reads Silver Lining as Silver Lining.
His comment Jeremy Fuchs, spokesman for Avanan Research, a Check Point Software company:
«We discovered an attack impersonating the CFO of a major sports organization. The "fake" CFO—aka the hacker—asks a low-ranking CFO to send a remittance to an insurance company. Instead, the amount would go directly to the hacker. In this case, we were able to successfully block the attack.
These "Business Email Compromise" attacks are extremely popular, difficult to stop and difficult to detect. End users should always exercise caution before paying invoices. It is better to confirm directly with the financial manager before payment.
I strongly recommend that users implement advanced email security that relies on more than one factor to determine whether an email is malicious or not. Be sure to read the entire email before acting, looking for any inconsistencies or oddities."
Cyber Safety Tips
- Always check the reply-to addresses to make sure they match
- If you're ever unsure about an email, ask the original sender.
- Read the entire email - look for any inconsistencies, correctgraphics errors or inconsistencies
- If you use banners, make sure you don't bombard end users with them - only use them at critical moments so that end users take them seriously