Plone CMS: The Story of the FBI Hack, no matter what whether it's true or is a hoax which aims to advertise a useless exploit, has brought me curiosity. What is and what does this CMS do? What's the difference from the others?
Let's get it from the beginning.
Since I already have a LAMP system installed (the initials of Linux, Apache, MySQL, PHP) I figured it wouldn't take me long. I dropped out because it took me even less. The installer of the Web application is standalone, that is, it can set up the site by itself without even having LAMP, or so to speak better the AMP.
I ran him installer on Linux (you will find it and for Windows but also for VirtualBox).
I will describe the installation on Linux:
You open a terminal in the folder that contains the installer and run the following commands:
tar-xf Plone-5.0.6-UnifiedInstaller-r1.tgz
cd Plone-5.0.6-UnifiedInstaller-r1
Let's start installing with options:
sudo ./install.sh $ OPTION
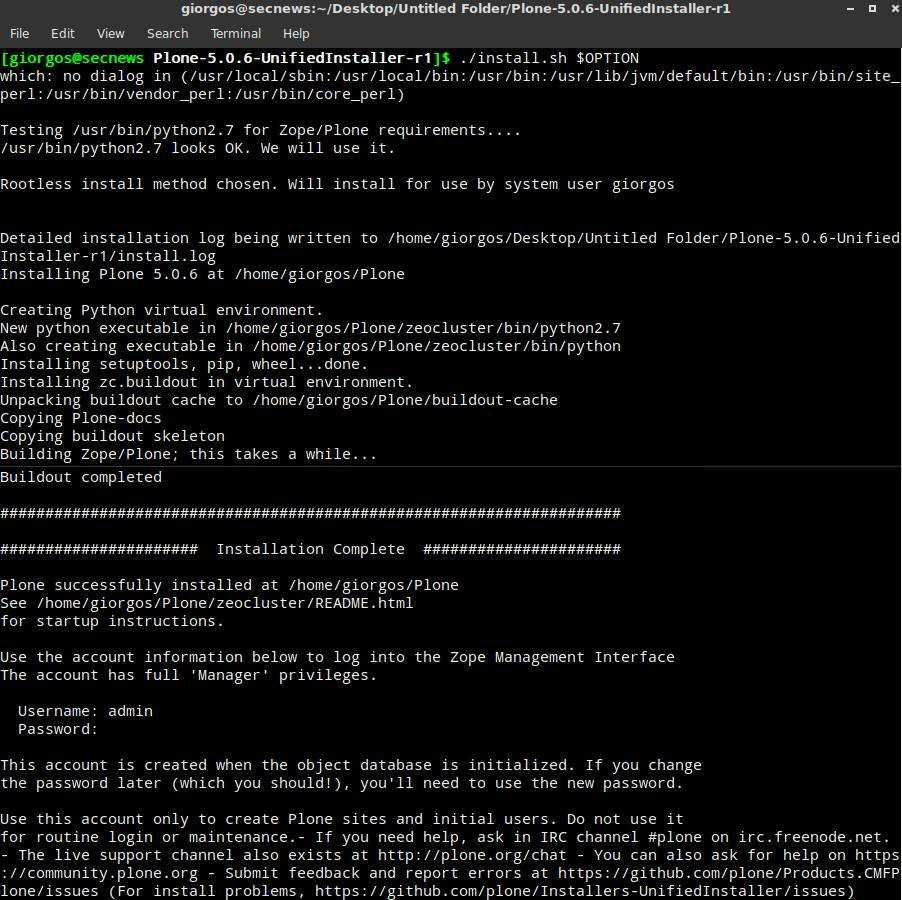
The latest commands are for activating and stopping Plone CMS.
cd ~ / Plone / zinstance / bin / plonectl start
ή
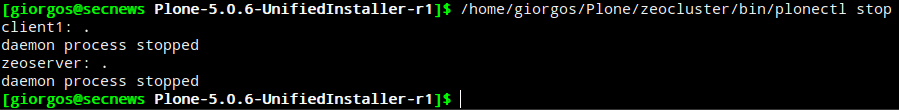
cd ~ / Plone / zinstance bin / plonectl stop
You are ready, you can see the first page of Plone CMS at:
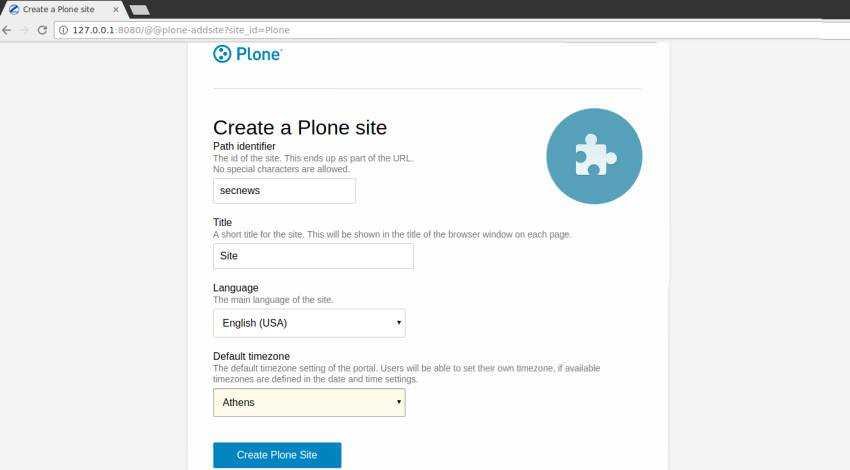
Then you can explore with your quiet setup
and the first page
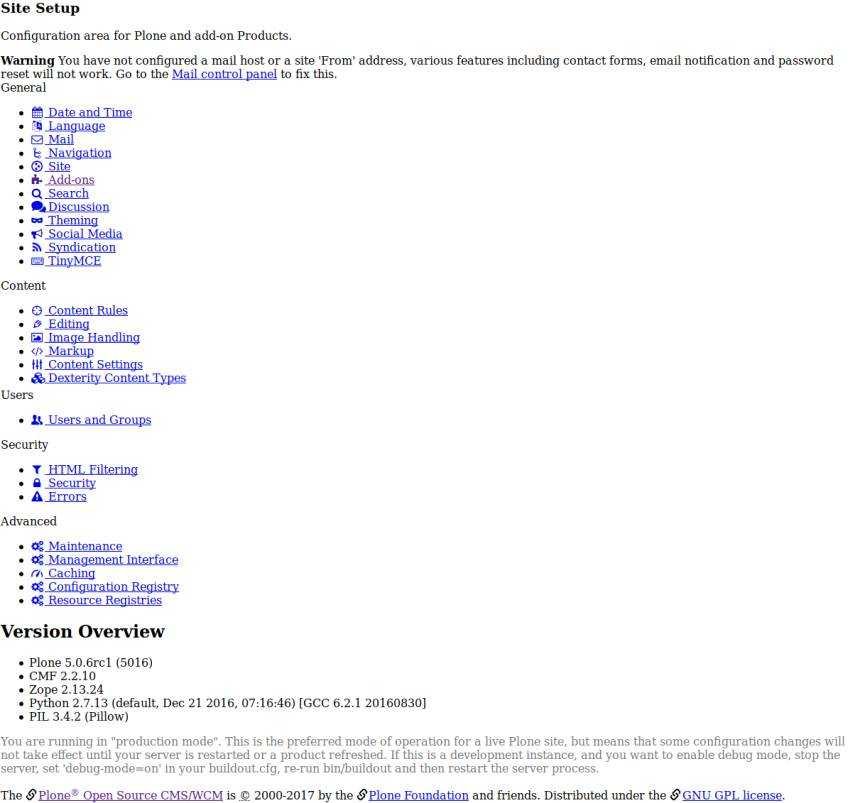
At a glance I noticed that an application has unlimited possibilities and settings.
Take a look at a detail to understand why Plone CMS does not need AMP
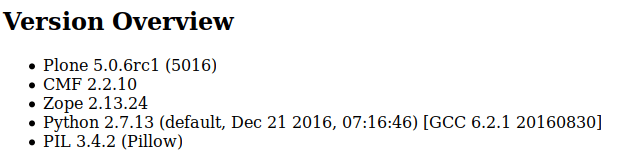
Plone uses a ZODB database. ZODB stores Python objects with any attributes. This does not require database schema or table descriptions as they are used in SQL systems. If the data models describe some Python script descriptions in some way, usually by using zope.schema packages.
This chapter is about the basics of ZODB, in conjunction with the ZODB database directly, such as the configuration database settings.
More information about ZODB
Of course I will mention the claim of the company that wants Plone to be the safest CMS in the world. On their website they say:
"The Plone CMS is one of the most secure website systems available. It is rare to have Common Vulnerability Exposures (CVE) published about Plone. A review of CVEs in the last 3 years for popular CMSs showed the following results with Plone being a clear winner with significantly fewer CVEs:
- Plone: 40
- Drupal: 409
- WordPress: 596
Source: National Vulnerability Database, February 2015 ″
However, they forgot to mention the adoption-use rates of each platform. Let's say WordPress may have had 596 vulnerabilities in 2015 but in how many installed CMS?
The high usability of each CMS makes it more visible to hackers and security researchers. Let's see now with the latest media reports that Plone's name became widely known how long she will be able to hold the title…
Due to the reports I write above I decided to install CMS, but only for educational purposes…