Last night, US law enforcement arrested three people for recent invasion of Twitter.
The US Department of Justice (DOJ) has released a stack of documents showing a timeline of the hack, and how US investigators were able to identify three suspected hackers.
- Mason Sheppard, also known as "Chaewon", 19 years old, from the United Kingdom [indictment].
- Nima Fazeli, also known as "Rolex", 22 years old, from Orlando, Florida [indictment].
- Graham Ivan Clark, believed to be "Kirk", 17, from Tampa, Florida [indictment].
According to Justice Department documents, the hack appears to have started on May 3, when Clark, a teenager from Tampa, gained access to a section of the Twitter network.

What happened between May 3 and July 15, the day of the real hack, is not clear but it seems that Clark was not able to immediately exploit his initial access point to the Twitter management tool.
However, a report from the New York Times days after the Twitter hack suggests that Clark initially had access to one of Twitter's Slack workspaces rather than Twitter itself.
NYT reporters, citing sources from the hacking community, reported that the hacker discovered the credentials for one of Twitter's technical support tools pinned to one of the company's Slack channels.
Images of this tool, which allows Twitter employees to control all aspects of an account, leaked to the internet on the day of the hack.
However, the credentials for this tool were not enough to gain access to the Twitter backend. In a Twitter blog post detailing the research of the breach, Twitter says accounts for that admin backend were protected with two-factor authentication (2FA).
It's not known how long it took Clark to do it, but Twitter's investigation says the hacker used a "phone spear phishing attack” to deceive some of his employees and gain access to their accounts, managing to “pass” the two-factor protection
According to Twitter, this happened on July 15, the same day of the hack.
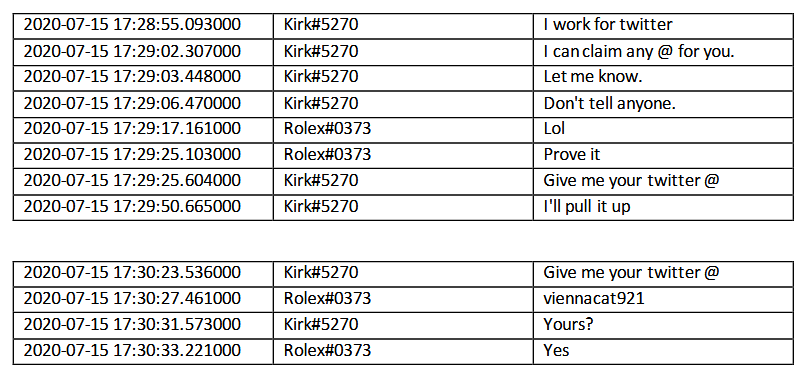
Clark, who appeared on Discord as Kirk # 5270, did not wait to be identified, and according to FBI conversations with Discord, the hacker contacted two other people to help him gain access to that access.
Records of these conversations contained in court documents show that Clark (Kirk # 5270) approached two other users of the OGUsers' Discord channel, a hacking forum for selling and buying social media accounts.
In the chat logs, it appears that Clark approached two other hackers (Fazeli as a "Rolex # 037" user on Discord and Sheppard as "ever so anxious # 0001") and claimed to be working on Twitter.
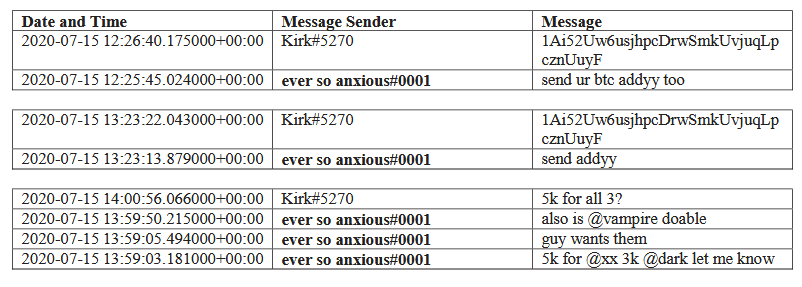
He proves his claims by modifying the settings of an account owned by Fazeli (Rolex # 037) and sold access to Fazeli to his @foreign Twitter account.
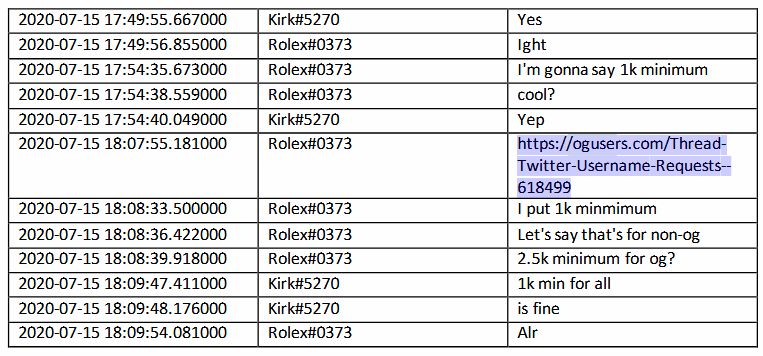
Clark also sold access to Sheppard for many Twitter accounts such as @xx, @dark, @vampire, @obinna and @drug.
When Clark convinced the other two of his access level, all three agreed to post ads on the OGUsers forum to promote Clark's ability to invade Twitter accounts.
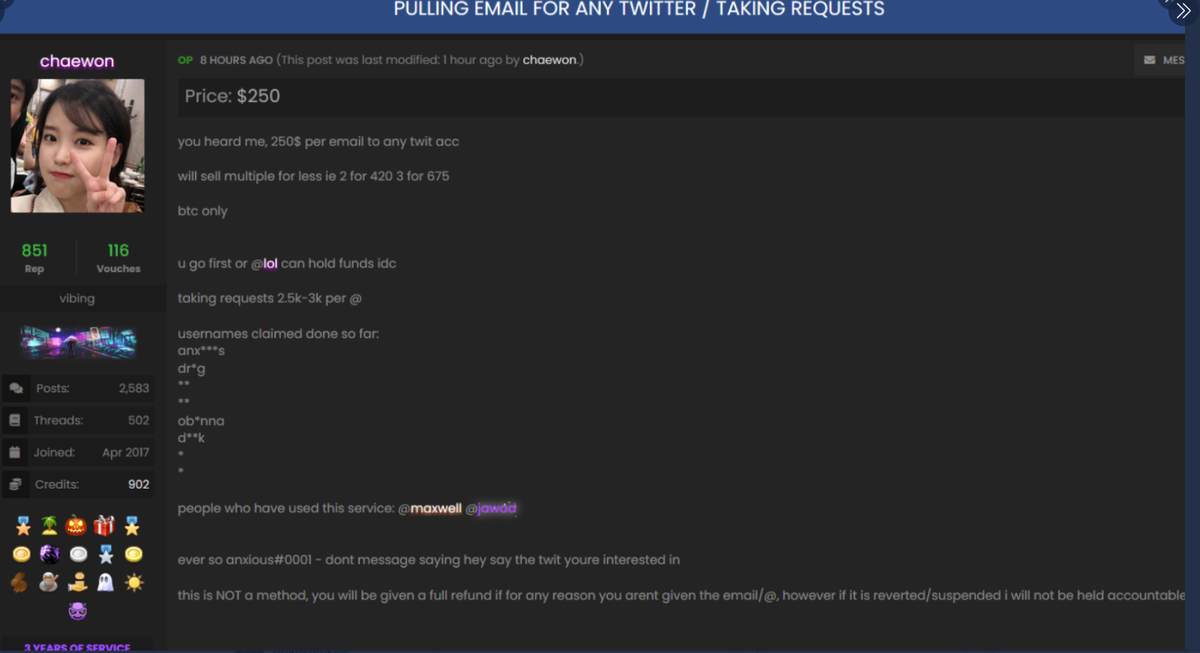
After these ads were posted, it is believed that too many people bought access to Twitter accounts. In a recorded message posted on YouTube by the Executive Office for United States Attorneys, the researchers say they are still considering many users who participated in the hack.
One of the hackers who bought access to Twitter accounts is believed to be responsible for the mass hacking of verified celebrity accounts on July 15 and for posting a message trying to fool people.
The message was found on the accounts of Barack Obama, Joe Biden, Bill Gates, Elon Musk, Jeff Bezos, Apple, Uber, Kanye West, Kim Kardashian, Floyd Mayweather, Michael Bloomberg and others, and asked users to send Bitcoins to various addresses.
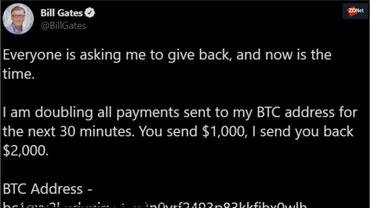
According to court documents, the hackers with the wallets used in this scam managed to collect 12,83 bitcoin or about 117.000 dollars.
At this point the breaches were revealed by Twitter staff, who intervened to block the verified accounts while ousting Clark from their network.
The Twitter investigation that followed found that Clark "teased" 130 accounts with his access to the Twitter management tool.
The day after the violation, Twitter filed a lawsuit against the authorities and the FBI and the secret service began their own investigation.
According to court documents, the FBI used data shared on social media, news sites and the Discord chat service.
The FBI also used a copy of the OGUsers forum database that leaked online in April this year after the forum was hacked. This database contained details of registered users, such as email, IP addresses, and private messages.
Authorities also received data from Coinbase about Bitcoin addresses involved in the scam.
By correlating data from the three sources, the FBI was able to identify the hackers and link them to email and IP addresses.
Authorities located Fazili after linking the Discord username to the OGUsers page, an obvious operational security flaw.
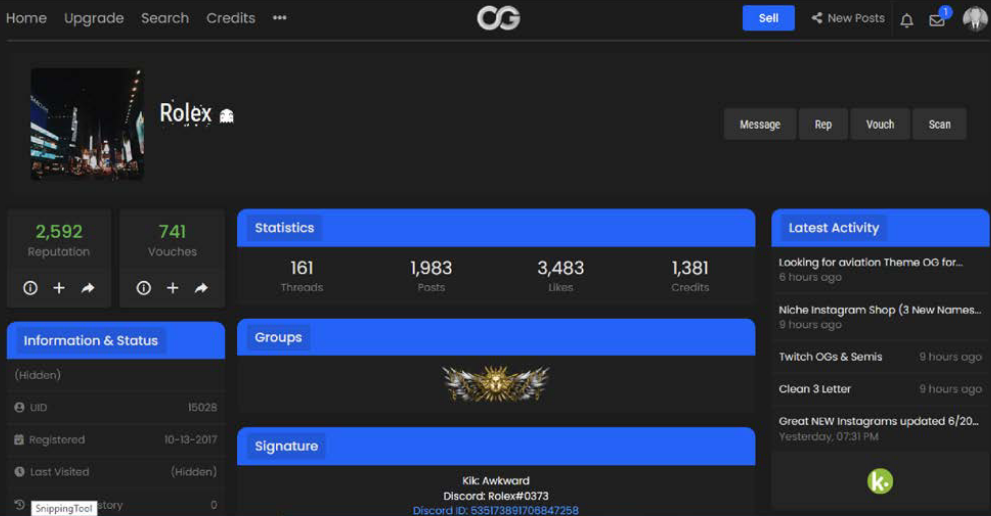
Fazili made many mistakes in hiding his identity. He used damniamevil20@gmail.com for an OGUsers account and chancelittle10@gmail.com to hack @foreign's Twitter account.
However, he used the same two addresses to register accounts with Coinbase, which he later verified with a photo of his driver's license (!).
In addition, Fazili also used a link from his home to access accounts on all three sites, leaving his home IP address in the log files of Discord, Coinbase and OGUsers.
The same thing happened with Sheppard. The investigators said they were able to link Discord Sheppard's user to OGUsers thanks to an ad posted on the site on the day of the breach. They later confirmed this through the leak of the OGUsers database, where they found Chaewon (Sheppard) using to buy access to a video game with a Bitcoin address linked to other addresses used on the day of the hack.
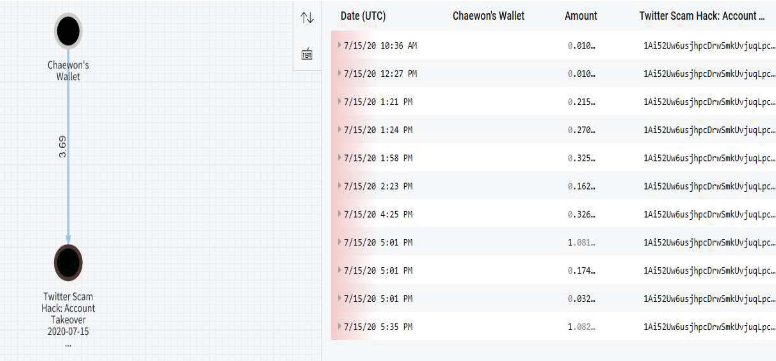
As in the case of Fazili, Sheppard had accounts with Coinbase, where he used his actual driver's license to verify them.
Authorities did not directly link Clark to Discord user Kirk # 5270, but details from the indictment show he is the same person.
Hillsborough District Attorney Andrew Warren says the 17-year-old from Tampa (Clark) was the “brain” of the hack.
The research was conducted by Catalin Cimpanu of ZDNet.





