Before you start trip to learn how to avoid being detected by AVs, it's important to first understand how an AV works. In this short post, we'll look at the primary methods antivirus developers use to detect malware

Most producttoday's antiviruses use only one of many Engines. Each of these machines has specific goals. The four main engines are as follows,
-
A Static Engine
-
Dynamic Engine
-
Heuristic Engine
-
Unpacking Engine
Static analysis
Each of these Engines has a specific goal and each has its own strengths and weaknesses. For example, the static engines most people are familiar with simply look for signatures of known malware. The best known of these are the YARA signatures which are updated almost daily.
The static engine simply compares files against a database of known malware signatures. This can be more difficult than it seems, as it is relatively simple to make modifications to the malware (creating a different signature) and thus bypass this static analysis.
Dynamic analysis
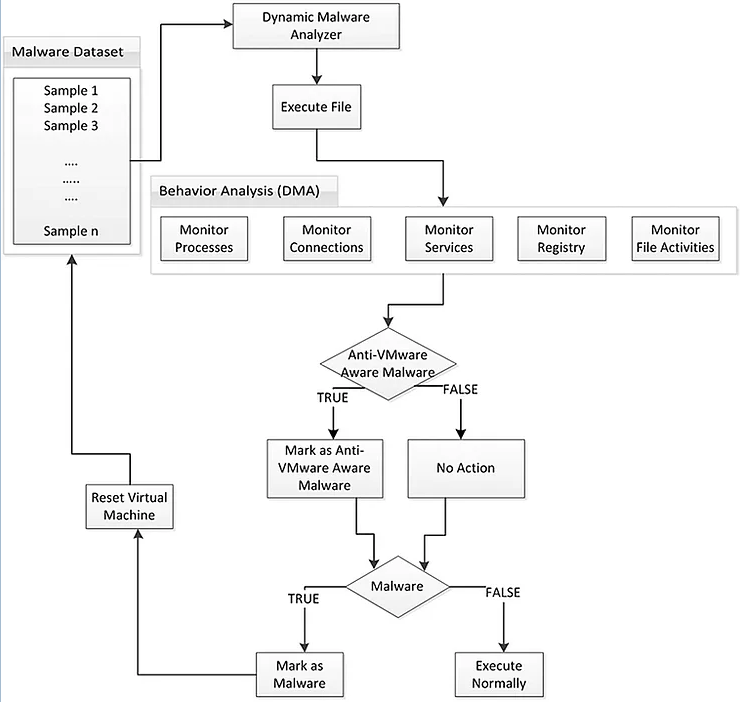
Dynamic analysis is a bit more advanced. It identifies malware by its behavior. The first behavior dynamic analysis looks for is API (application programming interface) calls.
Dynamic analysis uses system hooks to look for malicious behavior. Additionally, dynamic analysis uses sandboxing. The AV software creates a virtual environment separate from the host's memory and runs the suspected malware. In this way, the AV application can analyze the suspicious file in a safe environment without risk to the natural person host.
Heuristic analysis
Most AV applications now use a heuristic engine. To top it off for you, heuristics use the old "if it walks like a duck and quacks like a duck, it's probably a duck" rule. The AV application creates a score for each file based on various factors and then, through statistical analysis, determines the likelihood that it is malware.
For example, the heuristic will look for processes interacting with the LSASS.exe process, processes signed by a trusted software vendor, a process trying to become persistent, and a process trying to communicate with a C&C server.
The biggest drawback of heuristics is false positives, where the AV application determines that a file is malicious when it is not.
Analysis Un-Packed
One of the major ways malware developers use to evade AV applications is to package or compress their code.
In this way, they can avoid static detection by creating a different signature that is not recognized by the AV application during signature/static analysis.
The AV vendor must develop a decompressor for each packer available to malware developers. This can be a very slow and tedious process, but necessary if AV is to detect the malicious files that are manufactured.
Summary
A critical prerequisite for developing anti-virus evasion techniques is a good understanding of how anti-viruses work. Now that you have an idea of how these systems work, you're ready to start avoiding antiviruses.





